Introduction
In the modern digital landscape, where mobile applications are integral to everyday life, ensuring their security has never been more critical. As cyber threats become increasingly sophisticated, organizations must adopt proactive measures to identify and mitigate vulnerabilities before they can be exploited by malicious actors.
Mobile application penetration testing emerges as a vital strategy in this endeavor, simulating real-world attacks to uncover weaknesses that could jeopardize sensitive user data. With alarming statistics underscoring the prevalence of security breaches, the need for rigorous testing protocols is clear.
This article delves into the nuances of mobile app penetration testing, exploring its benefits, common vulnerabilities, the testing process, and the essential compliance considerations that organizations must navigate to safeguard their applications and maintain user trust.
Understanding Mobile Application Penetration Testing
Penetration testing for mobile apps serves as a critical simulated cyber attack designed to identify and address vulnerabilities within mobile software. This process rigorously assesses the software's protective stance by deliberately attempting to exploit vulnerabilities that could potentially be targeted by harmful individuals. Carrying out penetration testing for mobile apps enables organizations to reveal vulnerabilities before they can be exploited in real-world situations, significantly improving the overall protection of their mobile software.
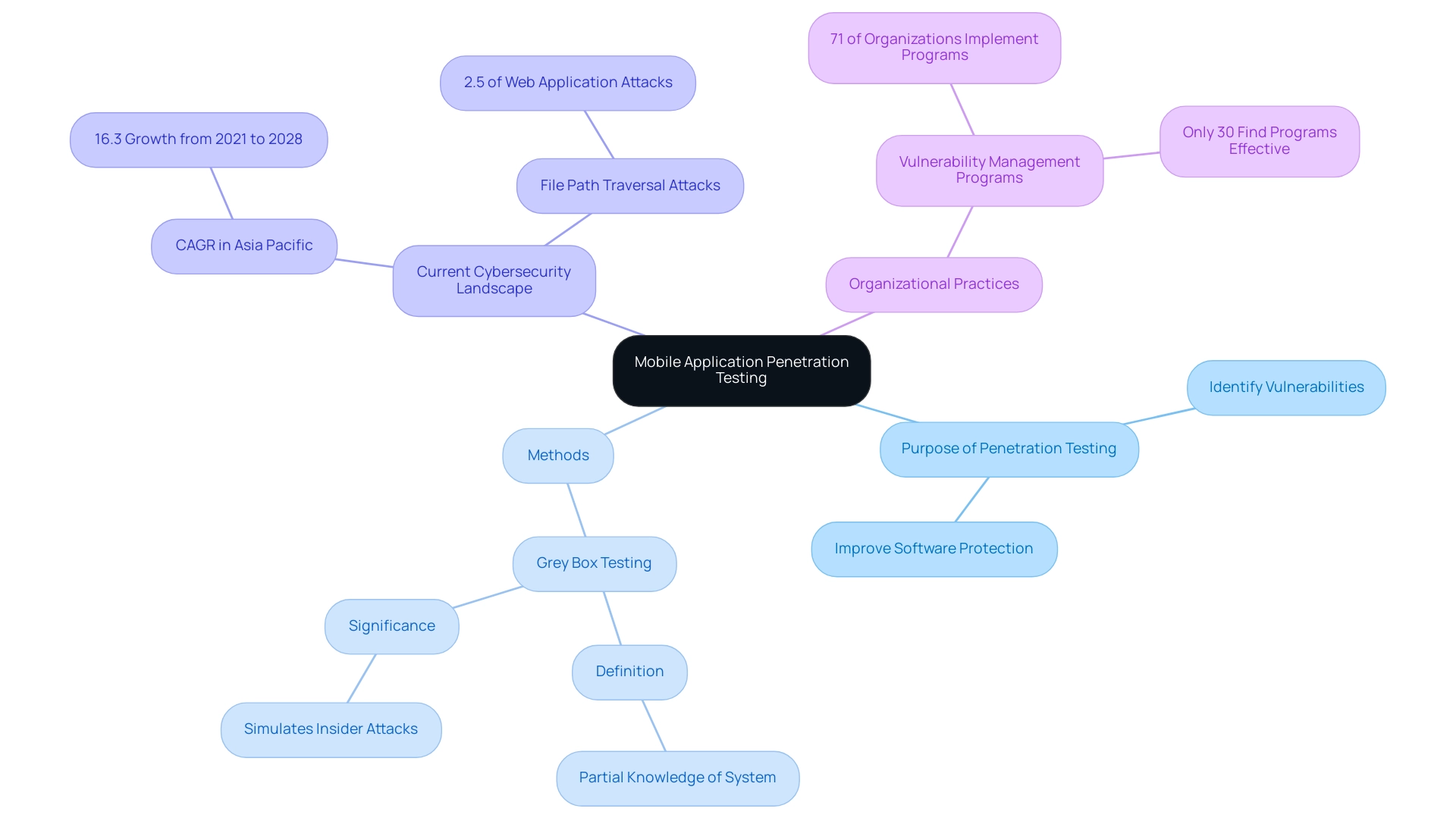
Such proactive measures are essential in today's digital landscape, especially in the context of penetration testing for mobile apps, which face an escalating number of cyber threats. Significantly, recent data show that file path traversal assaults represented 2.5% of all web system attacks, emphasizing the urgent need for thorough evaluation procedures to reduce such weaknesses. Moreover, as the Asia Pacific area expects the largest compound annual growth rate (CAGR) of 16.3% from 2021 to 2028 in cybersecurity initiatives, emphasizing penetration testing for mobile apps is essential for effective software protection evaluation.
In particular, grey box testing—defined as a method where the pen tester has some or partial knowledge of the target system, such as user accounts or network topology—simulates insider attacks and can effectively expose weaknesses that might otherwise go unnoticed. As organizations progressively acknowledge the significance of penetration testing for mobile apps, it becomes evident that establishing strong risk management programs is essential for safeguarding sensitive user information and preserving confidence in their applications. For instance, while 71% of organizations run formal vulnerability management or bug bounty programs, only 30% consider their programs very practical, indicating a significant gap between implementation and perceived effectiveness.
This highlights the importance of ongoing enhancement in protection evaluation methods.
Key Benefits of Mobile App Penetration Testing
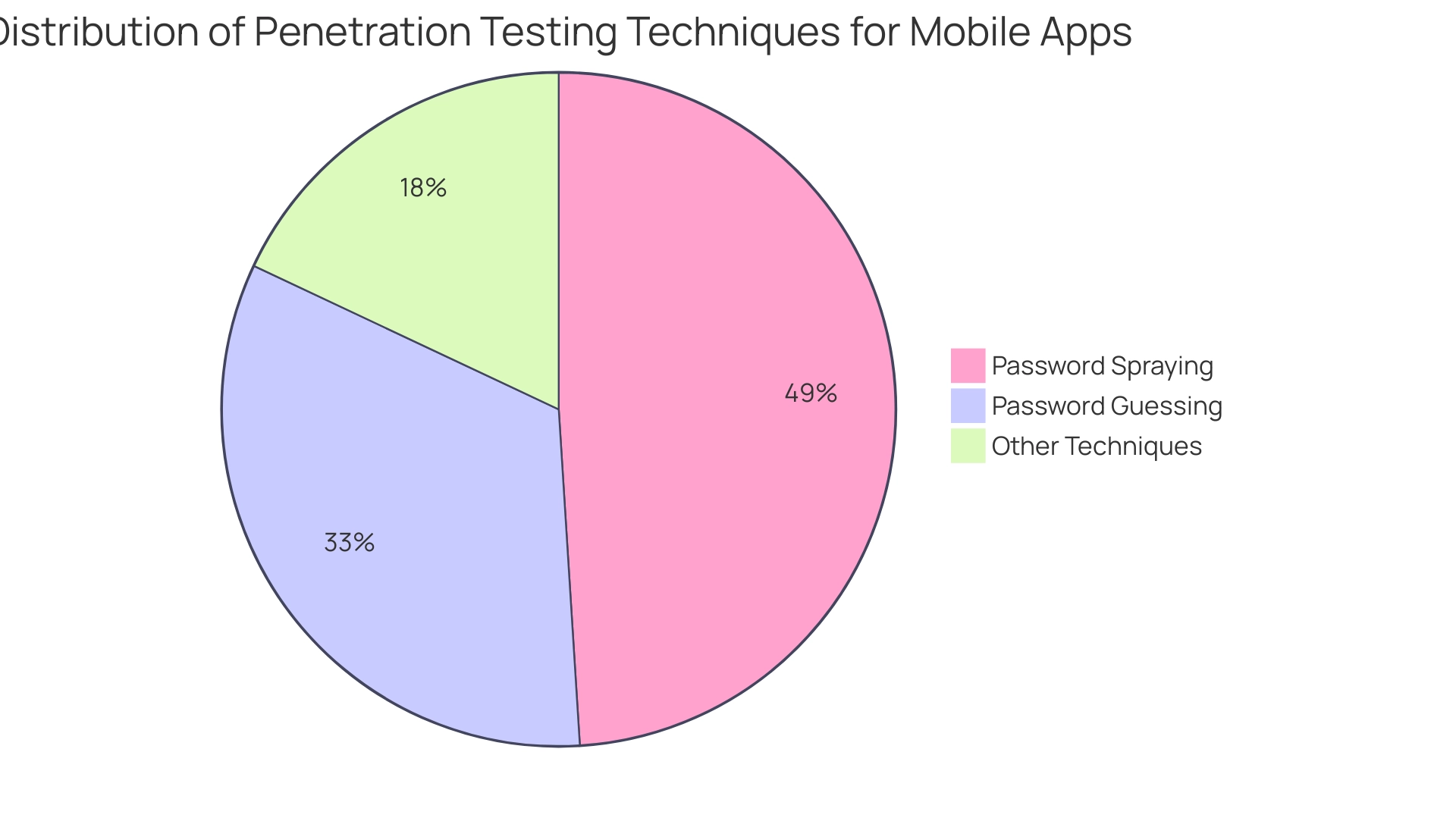
Frequent penetration testing for mobile apps is essential for protecting sensitive user information and improving overall safety. It functions as a proactive step to identify and reduce potential threats before they can be exploited, with pentesters predominantly utilizing techniques such as:
- Password spraying (49%)
- Password guessing (33%)
Furthermore, this assessment is crucial for compliance with industry regulations, showcasing an organization's commitment to protecting user information.
A notable case study highlights the impact of bot-based attacks, which have been identified as a significant contributor to successful breaches stemming from web application vulnerabilities. This highlights the importance for organizations to establish strong bot detection and mitigation strategies, further validating the requirement for regular penetration testing for mobile apps assessments. As highlighted by Gabrielle Hempel, a seasoned engineer and proponent of cybersecurity awareness, these proactive measures not only enhance protection but also cultivate user trust and loyalty—an essential currency in the fiercely competitive mobile app market.
In fact, with 42% of organizations reporting that their cybersecurity budgets are appropriately funded—the highest in eight years—it’s clear that investment in penetration testing for mobile apps is a strategic imperative. The projected growth of the global network protection market, anticipated to rise from $27.39 billion in 2021 to $60.38 billion in 2028, illustrates the increasing importance of cybersecurity measures, including penetration testing. Ultimately, these assessments not only improve an organization's defensive stance but also show diligence in maintaining compliance and protecting user data from increasingly sophisticated threats.
Common Vulnerabilities in Mobile Applications
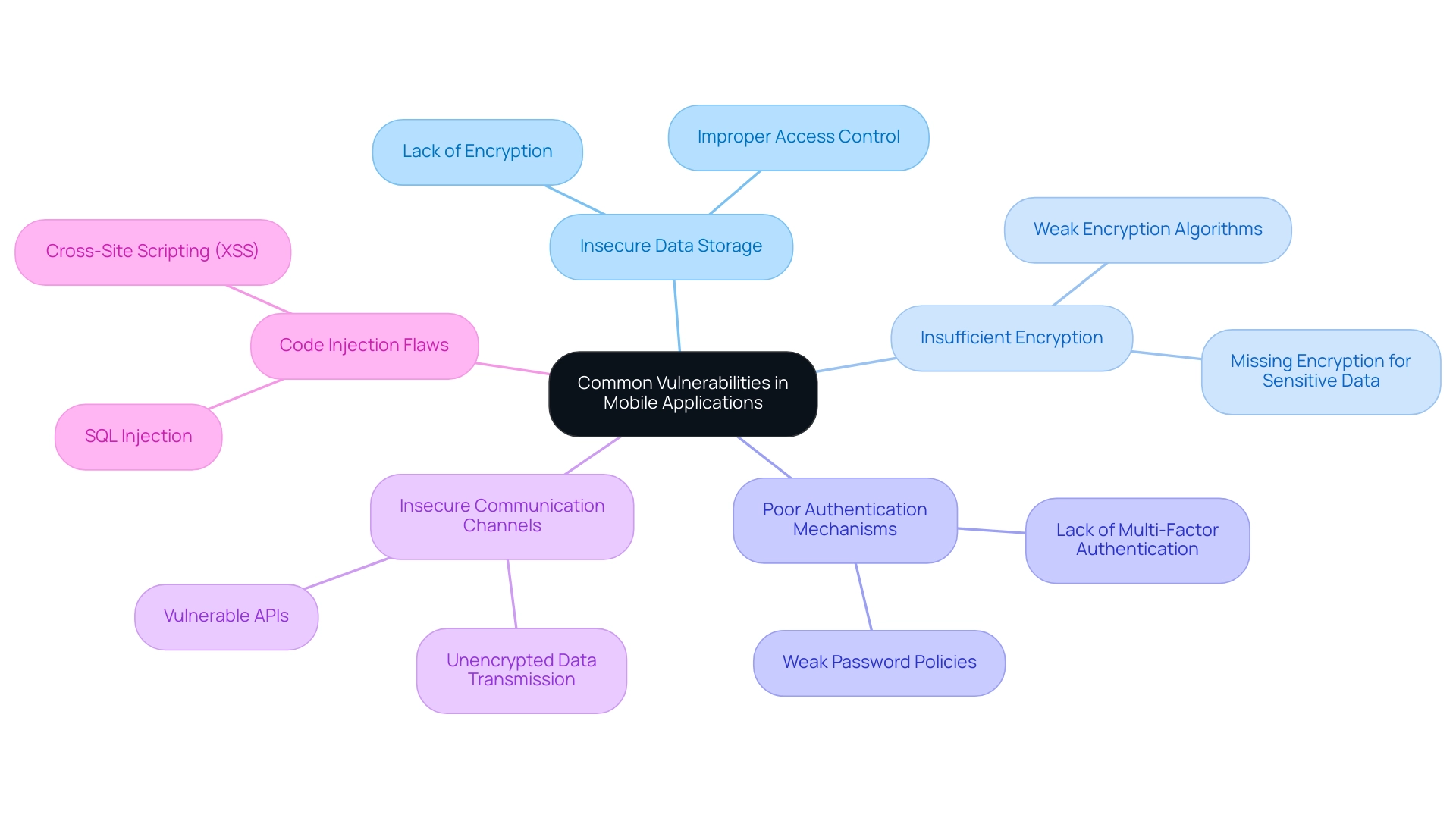
Mobile software remains vulnerable to a range of security flaws, with insecure data storage and insufficient encryption being among the most critical issues. A troubling trend observed in recent reports indicates that the Trojan-Banker.AndroidOS.Svpeng.Aj has surged by 2.79 percentage points, reaching a total of 3.74%.
This concerning statistic highlights the urgency for developers to tackle weaknesses effectively, as attackers increasingly focus on company brand image and developer reputation by compromising end user accounts to manipulate software. As noted by Lookout in their case study, implementing protective measures against mobile cyber threats is essential for safeguarding businesses. Numerous programs overlook encrypting sensitive data stored on devices, leaving it vulnerable to potential attacks.
Furthermore, authentication mechanisms are often poorly implemented, enabling unauthorized access to user accounts. Additional weaknesses include insecure communication channels, which risk exposing data during transmission, and code injection flaws that may permit attackers to execute harmful commands. Recent changes in attacked user distribution highlight a decrease in Hidden adware activity alongside a notable rise in RiskTool programs like Revo and SpyLoan.
This changing threat environment requires that developers and safeguarding professionals prioritize awareness of these vulnerabilities, as it directly informs the penetration testing for mobile apps assessment process and helps guide effective remediation strategies.
The Penetration Testing Process for Mobile Apps
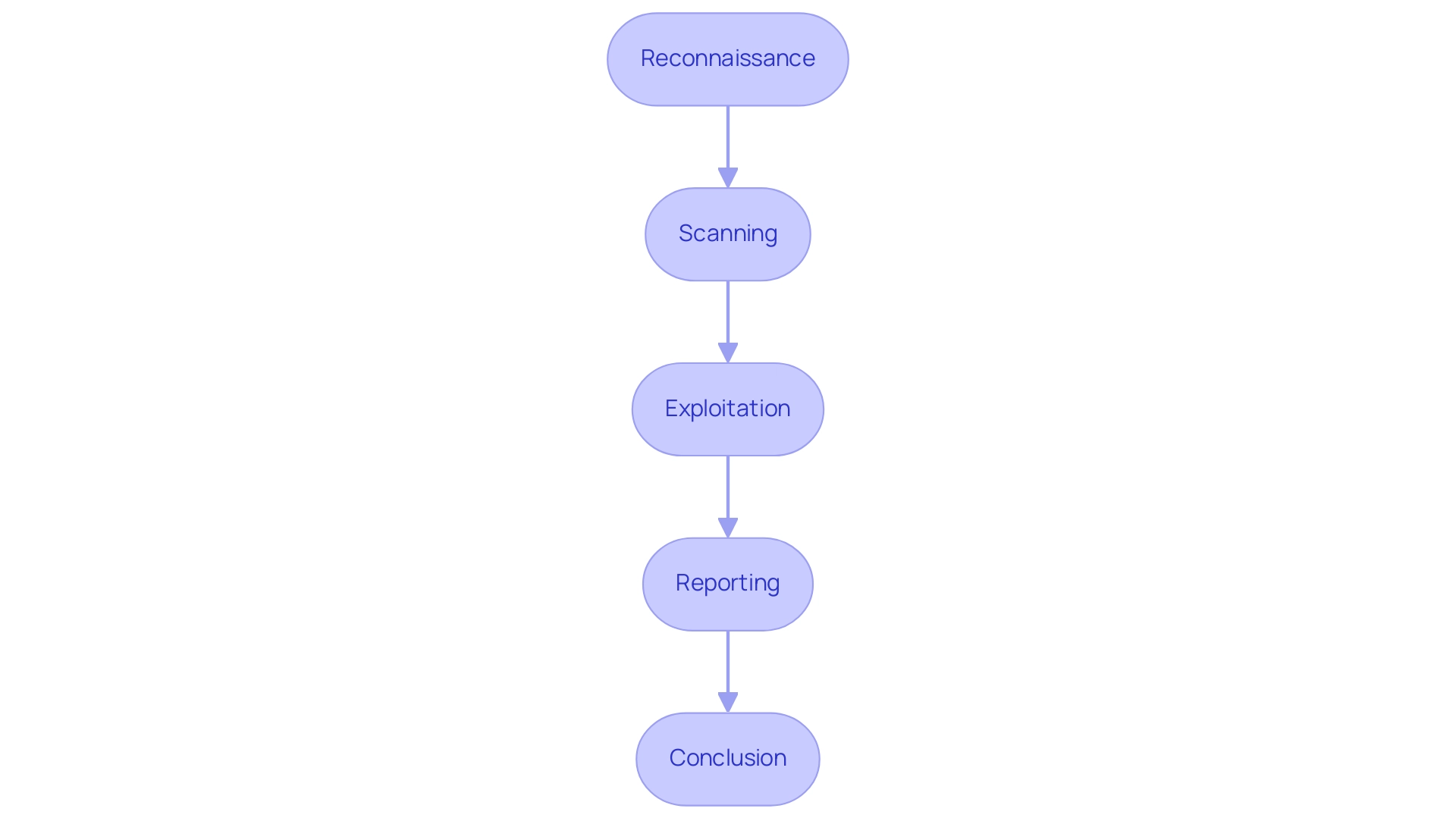
The process of penetration testing for mobile apps includes several essential stages, each intended to systematically evaluate the security stance of the software. Initially, the reconnaissance phase is crucial for gathering extensive information about the system and its environment, laying the groundwork for effective testing. Following this, the scanning phase utilizes automated tools to identify potential weaknesses, a practice emphasized by the statistic that file path traversal attacks make up 2.5% of web service attacks.
In the subsequent exploitation phase, testers simulate real-world attacks to assess the application's defenses against actual threats, which is vital given that reverse engineering poses a risk of 4%. This stage is especially significant, as a recent security assessment firm disclosed that 29% of their targets had at least one critical weakness during evaluations. The importance of penetration assessments is further underscored by a case study titled 'Conclusion on Penetration Assessment,' which emphasizes its crucial role in identifying weaknesses and safeguarding organizations against potential exploits.
Finally, a comprehensive report is generated from the penetration testing for mobile apps, detailing the findings, recognized issues, and actionable recommendations for remediation. This structured methodology not only helps organizations mitigate risks—such as the 1% associated with compromised services—but also reinforces the necessity of regular penetration testing to protect customer data and uphold brand reputation. By employing this thorough approach, directors of e-commerce can ensure a robust protective framework that addresses both current vulnerabilities and future threats.
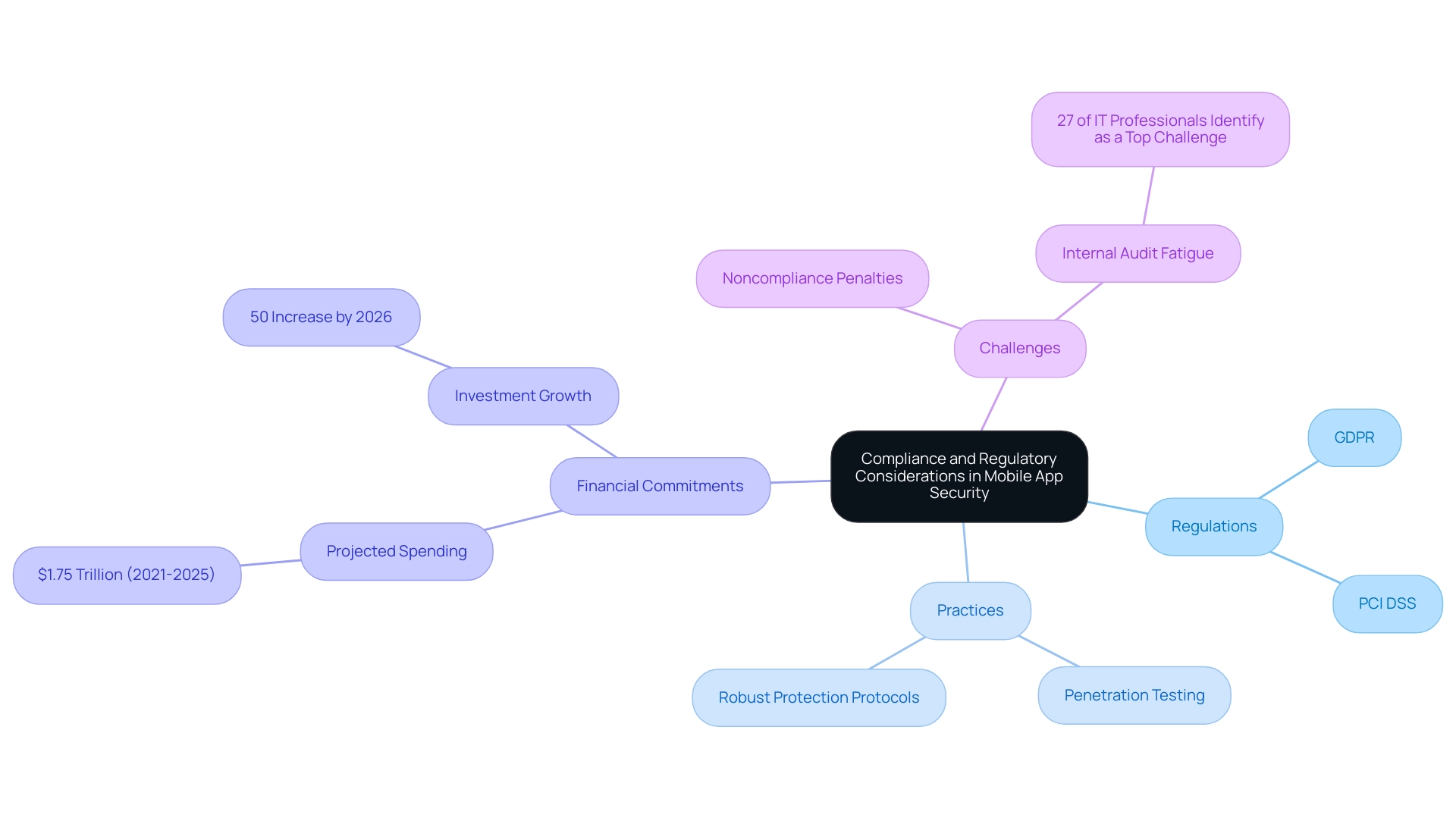
Compliance and Regulatory Considerations in Mobile App Security
Adherence to industry regulations is essential in the field of mobile application protection. Organizations must navigate a landscape shaped by standards such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). These regulations impose stringent protective measures designed to safeguard user data and uphold privacy.
Noncompliance can trigger substantial penalties and tarnish an organization's reputation. Recent statistics reveal that remote workers have been implicated in breaches in 20 percent of organizations during the pandemic, highlighting the critical need for robust protection protocols. Regular penetration testing for mobile apps emerges as a vital practice, not only for identifying vulnerabilities but also for demonstrating a proactive stance towards compliance.
According to projections, global spending on cybersecurity products and services is expected to reach $1.75 trillion from 2021 to 2025, highlighting the financial commitment necessary for organizations to maintain compliance and protection. As Gartner notes,
Investment in tools for following rules and being safe will increase by 50% in legal and compliance departments by 2026.
Such investments are crucial for organizations striving to comply with GDPR and PCI DSS standards while improving their overall protection stance.
Furthermore, the recent Build38 rebranding initiative exemplifies a strategic approach to reinforcing compliance and protection in the mobile protection sector. This initiative not only aims to enhance visibility but also positions the company as a leader in addressing compliance challenges. Furthermore, 27% of IT professionals have identified mitigating internal audit fatigue from assessments as a top compliance challenge, underscoring the need for streamlined processes in compliance efforts.
These elements collectively illustrate the critical nature of penetration testing for mobile apps and compliance in the security landscape of today.
Conclusion
Mobile application penetration testing is an indispensable practice in today's cyber landscape, where the stakes for data security are higher than ever. By simulating real-world attacks, organizations can proactively identify vulnerabilities within their apps, thus safeguarding sensitive user data from increasingly sophisticated threats. The article highlights the multifaceted benefits of penetration testing, not only in enhancing security but also in fostering user trust and ensuring compliance with regulatory standards.
The prevalence of common vulnerabilities, such as insecure data storage and inadequate encryption, underscores the urgent need for thorough testing protocols. As the threat landscape evolves, staying informed about these vulnerabilities is crucial for developers and security professionals alike. The structured penetration testing process—encompassing reconnaissance, scanning, exploitation, and reporting—serves as a comprehensive framework for organizations to bolster their security posture effectively.
Moreover, adherence to compliance regulations like GDPR and PCI DSS is vital for maintaining brand integrity and avoiding penalties. As investment in cybersecurity continues to grow, organizations must prioritize penetration testing as a strategic imperative. By doing so, they not only protect their applications but also contribute to a more secure digital environment for all users. Ultimately, the commitment to rigorous mobile app security testing will pave the way for a safer and more trusted digital experience.





