Introduction
In an age where digital interactions dominate, the security of web applications has become paramount for organizations across all sectors. As cyber threats evolve in complexity and frequency, the importance of implementing robust security measures cannot be overstated.
With alarming statistics revealing a staggering rise in cyberattacks, including a 400% increase in scams since early 2020, businesses are compelled to reassess their security protocols.
This article delves into the multifaceted realm of web application security, exploring:
- Common vulnerabilities
- Best practices for protection
- The critical role of continuous testing in safeguarding sensitive data
By understanding these elements, organizations can fortify their defenses and maintain user trust in an increasingly perilous digital landscape.
Defining Web Application Security: An Overview
The protection of web platforms is an essential aspect of web applications security, involving a thorough range of strategies and methods designed to safeguard web systems from various dangers and weaknesses. This protective framework is crucial for safeguarding sensitive data, ensuring the integrity of the system, and maintaining uninterrupted access for users. With the rise of e-commerce and online services, the web applications security has become essential as web platforms have become prime targets for cyberattacks, necessitating the implementation of strong protective measures to counter unauthorized access and data breaches.
In 2023, a significant event involving AT&T revealed personal information of around 9 million customers, highlighting the urgent need for improved protective measures. Cybersecurity challenges encompass various assaults like phishing, malware, social engineering, ransomware, and DDoS attacks, all of which present considerable threats to online platforms. Essential elements of web applications security involve:
- Authentication
- Authorization
- Encryption
- Secure coding practices
These elements are intended to reduce the risks linked with online interactions.
As cybercriminals adopt more sophisticated attack vectors—ranging from phishing and social engineering to AI-driven malware—businesses must prioritize innovative defenses that leverage machine learning and AI for early detection. The case study on 'More Complex Attack Vectors' highlights how cybercriminals have become increasingly creative in their attack methods, reinforcing the urgency for businesses to adopt smarter defenses. Furthermore, the worldwide cybersecurity market demonstrates this urgency, with expenditures on cybersecurity products and services expected to total an impressive $1.75 trillion cumulatively from 2021 to 2025, signifying a rising acknowledgment of the significance of web applications security for protecting businesses in today's digital environment.
Identifying Common Web Application Security Threats
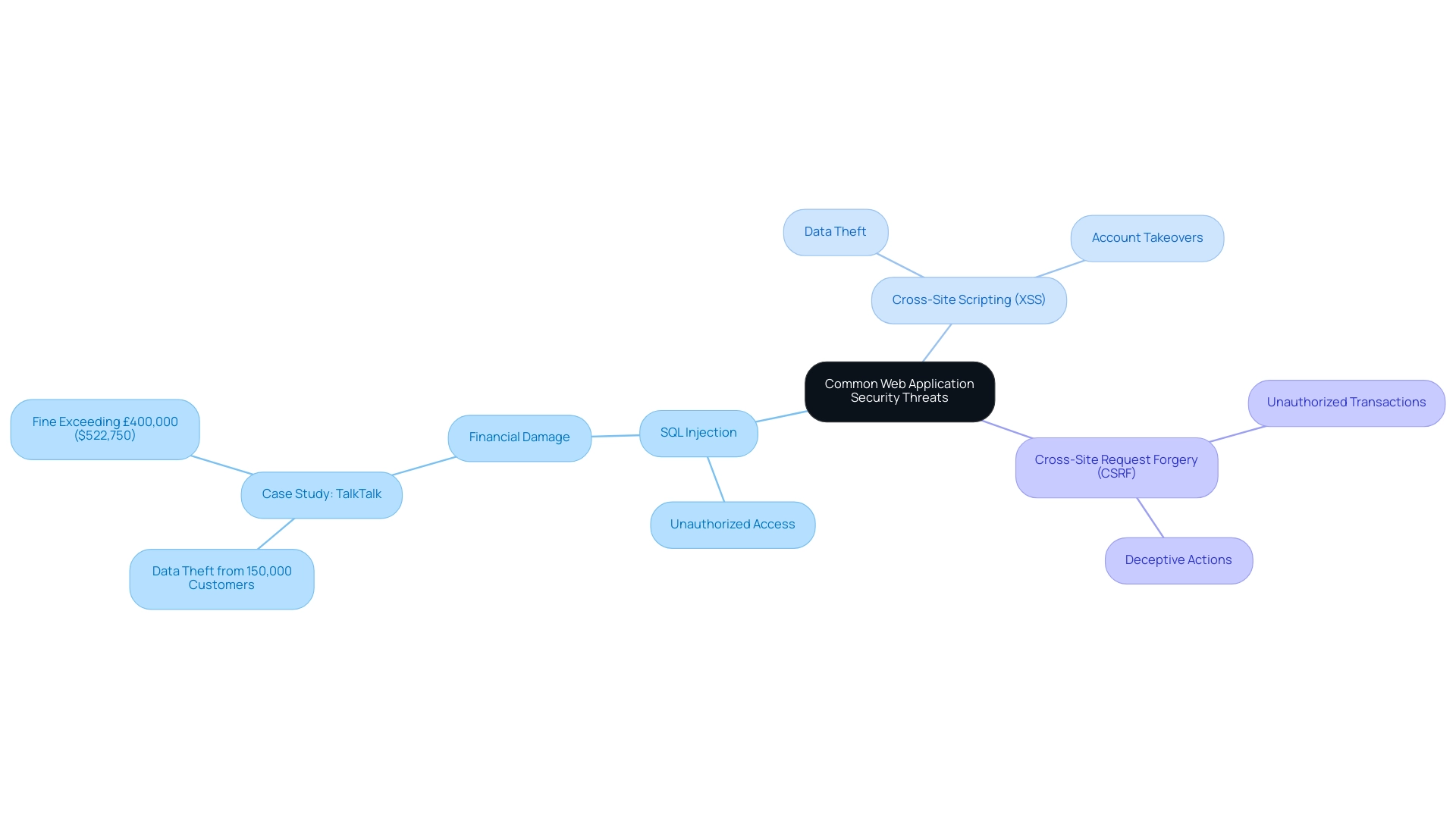
Web applications security is vital as web platforms face a multitude of threats, with SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) being among the most common. SQL injection weaknesses occur when attackers manipulate a web application's database queries, which can lead to unauthorized access to sensitive data. This threat was starkly illustrated in the case of TalkTalk, which suffered an SQL injection attack resulting in the theft of personal data from 150,000 customers and a significant fine exceeding £400,000 ($522,750).
This incident underscores not only the severe financial and reputational damage that can result from SQL injection attacks but also the critical need for effective security measures. Organizations are encouraged to adopt recommended principles and best practices in web applications security to eradicate SQL injection risks, as outlined on CISA's Secure by Design page. Similarly, XSS vulnerabilities enable attackers to embed malicious scripts into web pages, compromising user data and session information.
The repercussions can be dire, as these scripts can lead to data theft and account takeovers. CSRF presents another significant threat, deceiving authenticated users into performing undesirable actions within a web platform, potentially resulting in unauthorized transactions. As cybersecurity experts note, with global spending on cybersecurity products and services expected to reach $1.75 trillion from 2021 to 2025, it is clear that organizations must prioritize awareness and proactive measures in web applications security to protect their assets and maintain user trust.
Best Practices for Securing Web Applications
To effectively secure web applications security, organizations must implement a range of best practices that are vital in today's rapidly evolving cybersecurity landscape. These encompass the adoption of secure coding methods and compliance with established frameworks such as the OWASP framework, which outlines critical areas for developers to concentrate on. Regular code assessments and the use of strict input validation and sanitization procedures are vital to reduce risks linked to user input.
Furthermore, robust authentication methods, particularly multi-factor authentication (MFA), have shown to significantly decrease the likelihood of unauthorized access, addressing a major factor in breaches.
In light of recent reports indicating approximately 5,600 ransomware incidents from January 2023 to February 2024, it becomes evident that proactive measures are necessary. A data breach investigation report from 2023 revealed that 97% of threat actors are motivated by financial gain, emphasizing the need for organizations to remain vigilant. As predicted, worldwide cybercrime costs are expected to reach $10.5 trillion annually by 2025, with cumulative global spending on cybersecurity products projected at $1.75 trillion from 2021 to 2025.
Moreover, remote employees triggered a security breach in 20 percent of organizations during the pandemic, emphasizing weaknesses that organizations may encounter in a hybrid work environment. Regular security assessments and penetration testing are essential in identifying and addressing weaknesses before they can be exploited. Furthermore, keeping software and dependencies up to date is critical in defending against known risks.
By diligently adhering to these optimal procedures, organizations can significantly reduce the threat of breaches and enhance web applications security for their online platforms.
The Role of Continuous Testing in Web Application Security
Continuous testing is an indispensable element of web applications security, crucial for identifying and mitigating vulnerabilities in real-time. The necessity for such proactive measures has been emphasized by the alarming 400% rise in scams since March 2020, a trend that highlights COVID-19 as a significant catalyst for threats. Furthermore, with the global information protection market projected to reach $366.1 billion by 2028, organizations must prioritize investing in robust protective measures.
Incorporating continuous testing for safety within the development lifecycle is essential, utilizing both automated tools and manual testing methods. This integration not only enables early detection of issues but also significantly reduces the potential costs and impacts associated with breaches. As Jacob Fox aptly notes,
This amplifies the need for continuous monitoring and assessment of weaknesses.
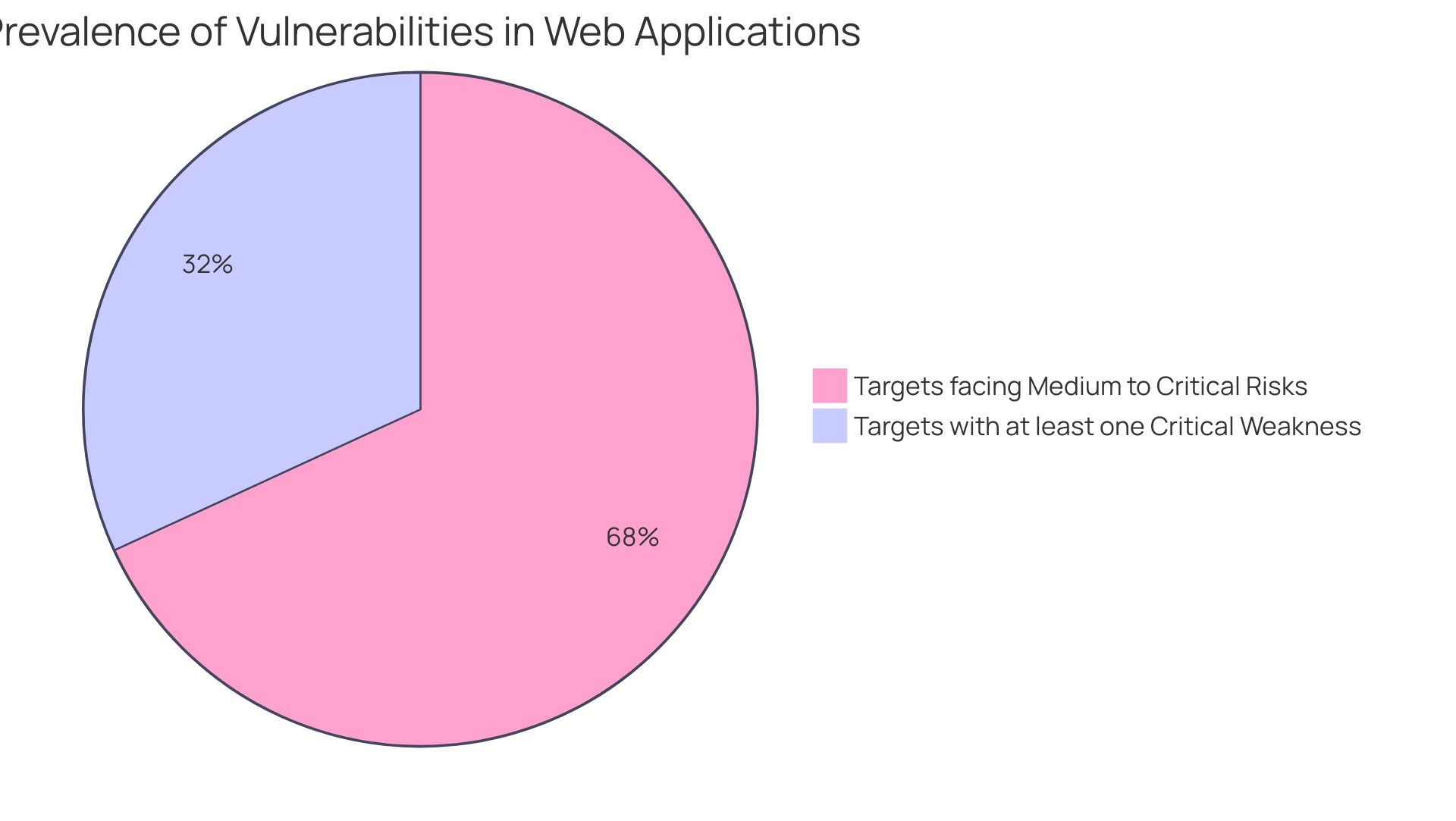
The role of the Software Risk Manager is crucial here, acting as a management layer for protective tools, correlating data for easier interpretation and remediation. Moreover, information from recent penetration tests indicated that:
- 29% of targets had at least one critical weakness
- 62% facing medium to critical risks
These findings highlight the prevalence of vulnerabilities in organizations and reinforce the importance of ongoing testing in maintaining a robust security posture.
In today’s ever-evolving digital landscape, prioritizing continuous testing is essential for safeguarding sensitive information and ensuring swift remediation of potential threats.
Conclusion
The landscape of web application security is increasingly complex, demanding that organizations remain vigilant in their defense strategies. Key vulnerabilities such as:
- SQL injection
- Cross-site scripting
- Cross-site request forgery
present significant risks that can lead to devastating consequences, as seen in high-profile breaches like those involving TalkTalk and AT&T. Understanding these threats is the first step in cultivating a robust security posture.
Implementing best practices is essential for safeguarding web applications. This includes:
- Adopting secure coding techniques
- Utilizing multi-factor authentication
- Conducting regular vulnerability assessments
The staggering statistics surrounding cybercrime underscore the urgency for businesses to prioritize these measures, especially in light of the evolving threat landscape characterized by sophisticated attack vectors.
Equally important is the role of continuous testing in maintaining web application security. As cyber threats proliferate, embedding testing within the development lifecycle allows for real-time detection and remediation of vulnerabilities. Organizations must invest in both automated and manual testing methods to ensure that their defenses are not only reactive but also proactive.
In summary, a comprehensive approach that encompasses awareness of common threats, adherence to best practices, and the integration of continuous testing is vital for protecting sensitive data and maintaining user trust. As cyber threats continue to rise, the commitment to robust web application security is not just a necessity but a critical business imperative.





