Introduction
In an age where mobile applications have become integral to everyday life, ensuring their security is paramount. With the rapid proliferation of mobile technologies, the risks associated with data breaches and cyber threats have escalated dramatically, necessitating a proactive approach to safeguarding sensitive information.
Organizations are increasingly recognizing that robust mobile app security is not merely an option but a critical necessity that can protect both user data and business integrity. This article delves into the multifaceted realm of mobile application security, exploring common vulnerabilities, best practices for developers, and the importance of continuous security measures as the landscape evolves.
As threats grow more sophisticated, understanding how to fortify mobile applications is essential for any organization aiming to thrive in the digital era.
Understanding Mobile Application Security: An Overview
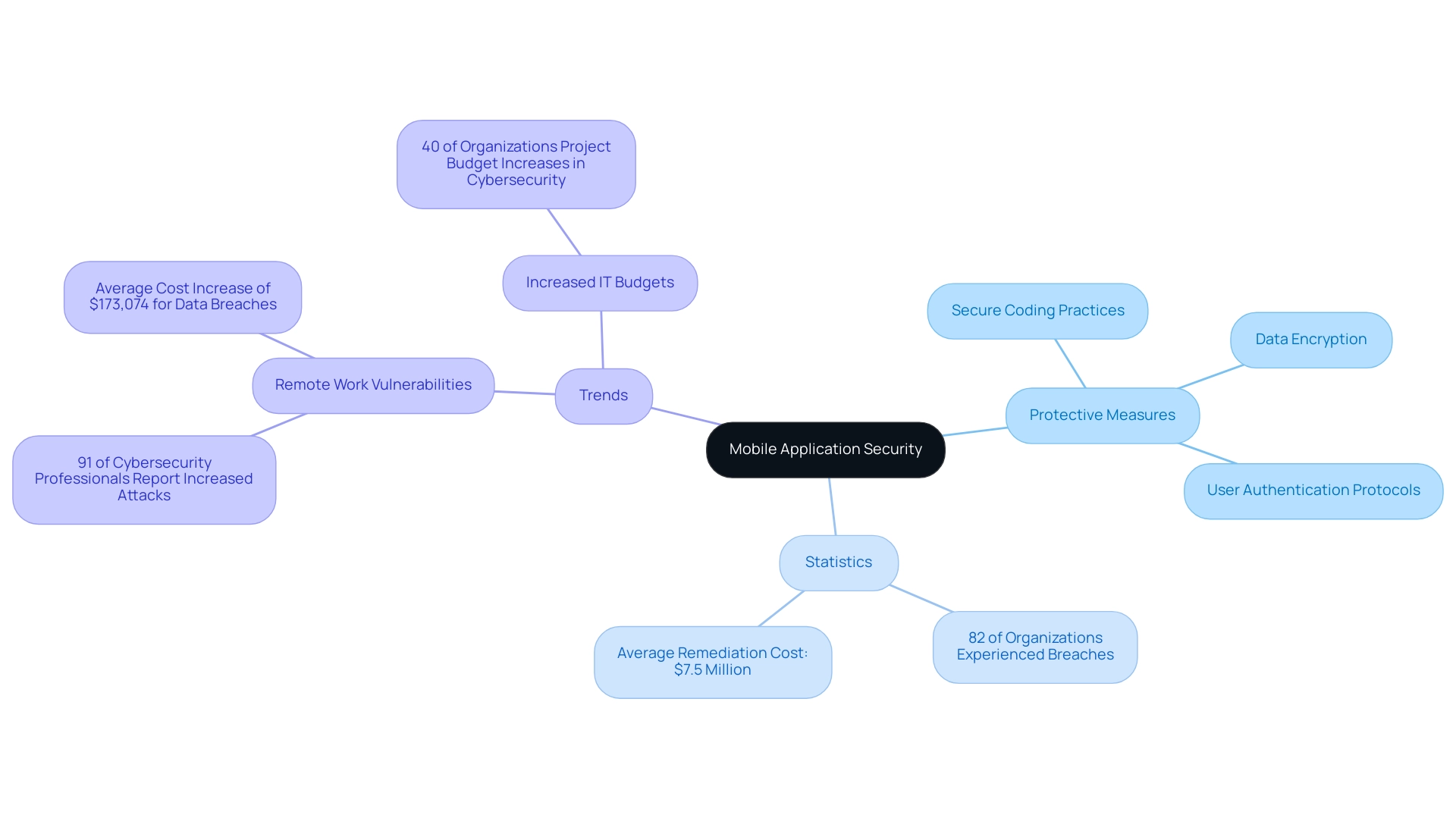
The protection of applications includes a range of measures and strategies designed to ensure the security of mobile apps against different dangers that threaten data integrity, confidentiality, and availability. With application usage skyrocketing across various sectors, ensuring the security of mobile apps has never been more critical. A comprehensive protection strategy must include:
- Secure coding practices
- Data encryption
- Stringent user authentication protocols
As smartphone applications increasingly process sensitive information—ranging from personal data to payment details—the security of mobile apps becomes a critical concern. Remarkably, 82% of organizations have reported experiencing one or more third-party data breaches, with the average remediation cost soaring to $7.5 million. This concerning statistic emphasizes the pressing need for organizations to prioritize the security of mobile apps to ensure application protection.
Build38 aptly states,
Mobile app protection is no longer an optional consideration; it is a critical necessity.
Moreover, with IT budgets projected to rise in 40% of organizations in 2023, the security of mobile apps is emerging as a leading area for heightened investment, highlighting the increasing significance of application protection measures. The shift to remote work during the pandemic has introduced new vulnerabilities, with 91% of cybersecurity professionals reporting an increase in cyber attacks due to remote working.
The average total cost of a data breach escalated by $173,074 when a remote workforce was involved. As we approach 2024, understanding the security of mobile apps is not only advantageous but crucial for protecting both users and businesses from rising dangers.
Identifying Common Security Threats in Mobile Apps
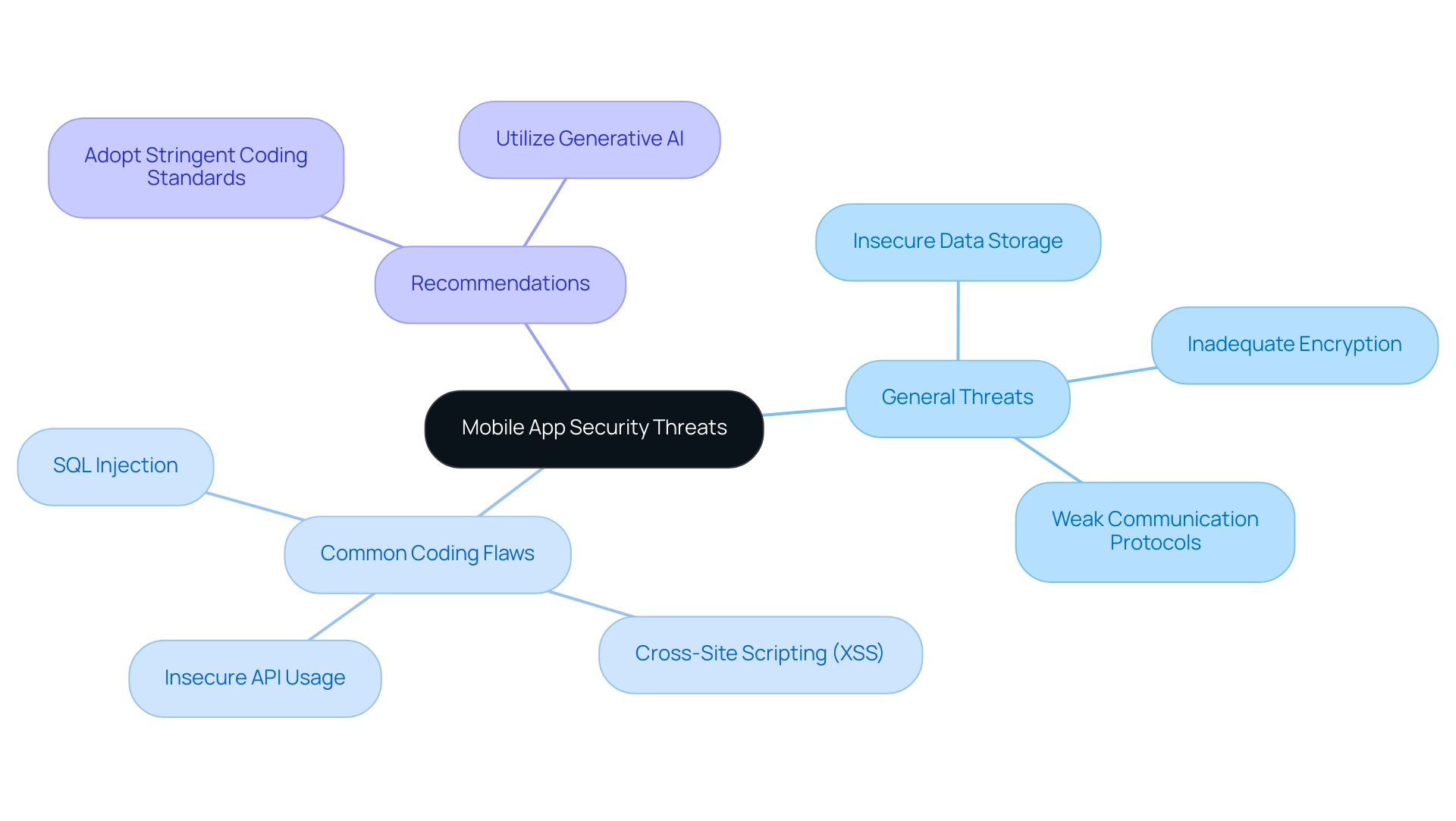
The security of mobile apps is increasingly important as they are vulnerable to a range of threats, including:
- Insecure data storage
- Inadequate encryption
- Weaknesses in communication protocols
A growing body of evidence indicates that poor coding practices significantly contribute to these vulnerabilities. Common coding flaws, such as:
- SQL injection
- Cross-site scripting (XSS)
- Insecure API usage
can leave applications exposed to attacks.
In 2024, it is estimated that these vulnerabilities will continue to be major contributors to breaches, highlighting the necessity for developers to adopt stringent coding standards. Furthermore, many mobile applications store sensitive user data locally on devices, often without adequate protective measures, rendering them susceptible to exploitation. A notable case is that of Igexin, a Chinese advertising SDK that deployed malicious plugins capable of spying on users, posing a medium severity risk with the potential to leak sensitive information.
This highlights the essential requirement for developers to comprehend these dangers and establish strong protective measures to shield user information from harmful individuals. As highlighted in a recent McKinsey study, generative AI can improve development speed by 10-30%, indicating that embracing advanced coding techniques can also strengthen protective measures. Furthermore, input from prominent authorities in the OWASP Mobile initiative, such as Mohammed Junaid Tariq and Steffen Lortz, highlights the significance of remaining aware of new dangers and optimal approaches.
Statistics indicate that in 2024, common threats such as insecure data storage and inadequate encryption will remain prevalent, reinforcing the urgency for developers to proactively address the security of mobile apps. By acknowledging the continuous efforts in the area and applying suggested optimal methods, developers can greatly reduce risks related to application safety.
Best Practices for Ensuring Mobile App Security
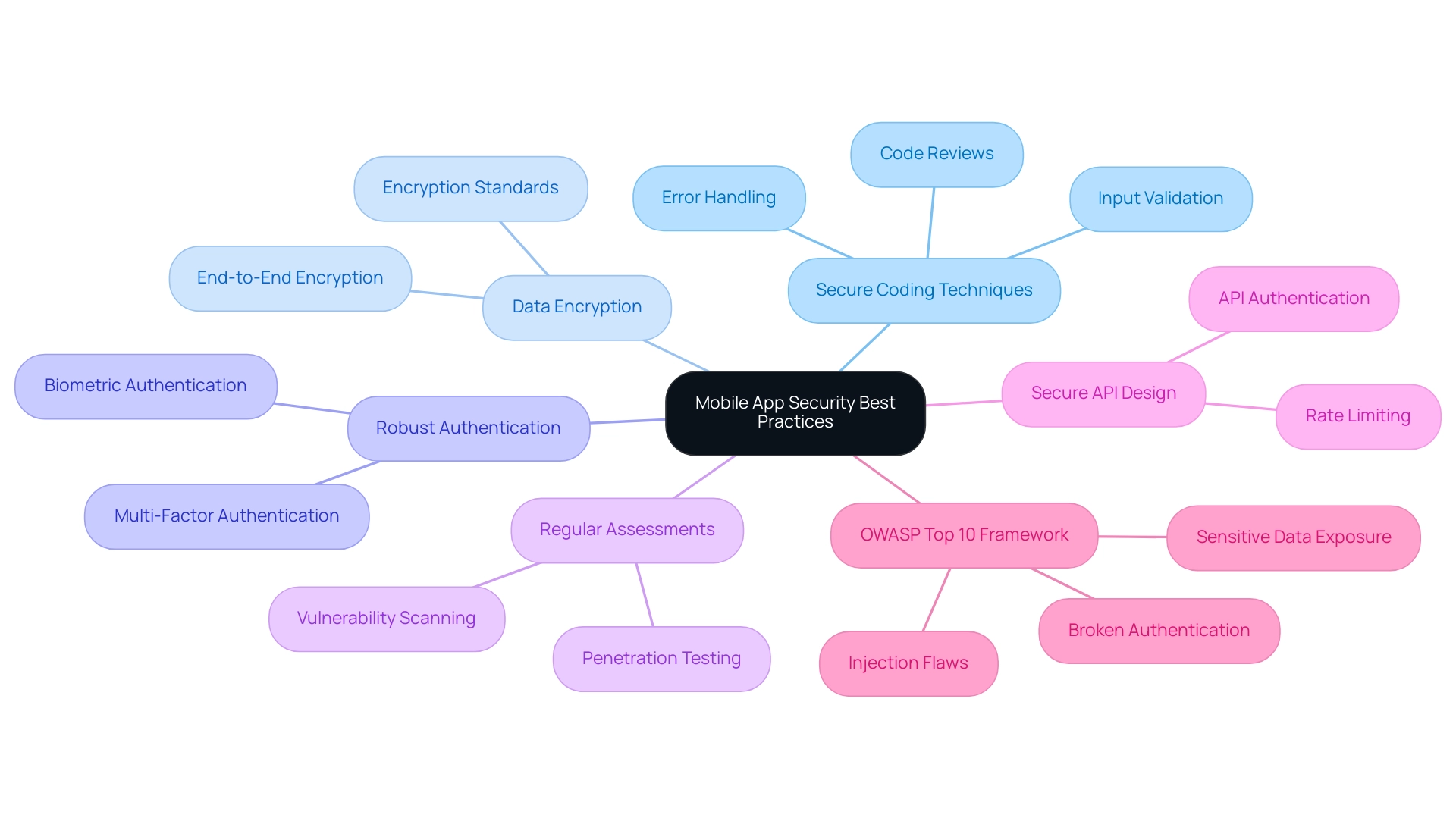
To enhance the security of mobile apps, developers must adopt a range of optimal methods, starting with the application of secure coding techniques that have proven effective in reducing vulnerabilities. Notably, generative AI can increase development speed by 10-30%, making secure coding practices not only effective but also efficient. Utilizing data encryption is essential to safeguard sensitive user information, while robust authentication methods further enhance the security of mobile apps.
Regular assessments and penetration testing are essential for enhancing the security of mobile apps by identifying potential vulnerabilities before they can be exploited. Furthermore, ensuring the security of mobile apps by prioritizing secure API design is essential; developers should handle third-party libraries carefully, ensuring they are regularly updated and thoroughly examined for vulnerabilities. The OWASP Top 10 list serves as an essential framework for understanding the most significant application vulnerabilities, particularly concerning the security of mobile apps, and provides guidance on detection and mitigation.
By diligently following these best practices, businesses can significantly lower the risk of breaches, foster user trust, and improve the security of mobile apps while aligning with evolving standards in application protection for 2024. As Vita Petrovskaya aptly states, 'Understanding the threat landscape is not about inducing fear but fostering preparedness.' This mindset is crucial for navigating the intricacies of application protection.
The Importance of Continuous Security in Mobile App Development
In today’s rapidly evolving digital landscape, the need for ongoing protection and security of mobile apps in development has never been more pressing. With new threats and vulnerabilities emerging regularly, developers must remain vigilant and adaptive in their protective practices to maintain the security of mobile apps. Significantly, fines for violations of EU privacy regulations have increased seven times, totaling $1.2 billion, highlighting the financial consequences of insufficient protective measures.
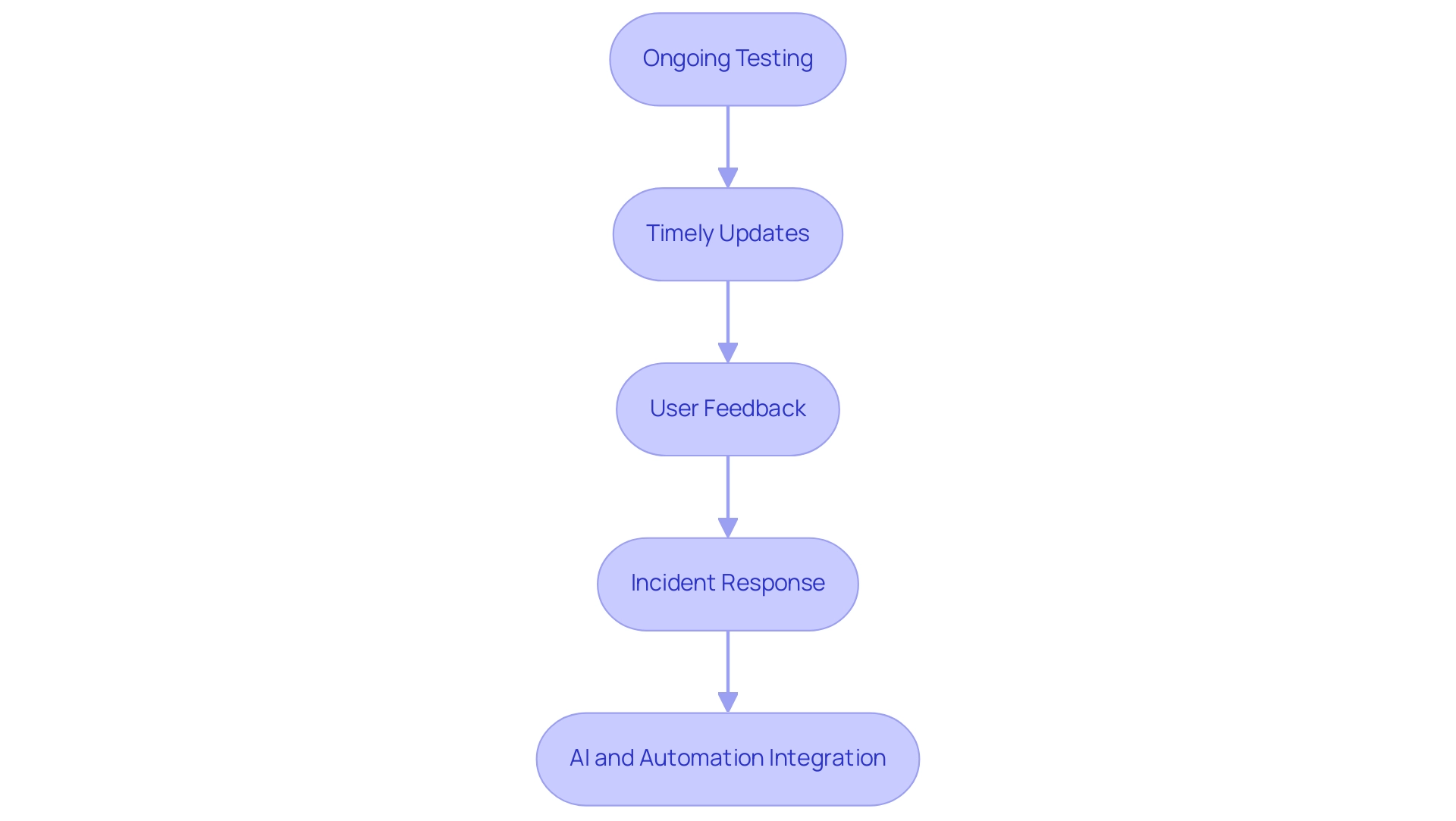
Implementing a robust protection lifecycle is essential for the security of mobile apps, encompassing ongoing testing, timely updates, user feedback, and effective incident response strategies to swiftly address potential breaches. Organizations leveraging AI and automation programs are recognizing significant advantages, as they can identify and contain breaches 28 days faster than those that do not. As Fortune forecasts, the global information protection market is expected to attain $366.1 billion by 2028, rendering investment in ongoing protective measures not merely a compliance requirement but a strategic necessity.
This is especially crucial in a competitive market, where continuous innovation and optimization are vital, as highlighted by a case study showing that an app's functionality and innovative features can differentiate it from competitors. By prioritizing such measures, businesses can ensure the security of mobile apps against emerging threats and foster user trust, thus positioning themselves ahead in a competitive landscape where mobile apps are expected to generate over $613 billion in revenues by 2025. Furthermore, with Build38 announcing a new brand identity as part of a strategic rebranding initiative, it's clear that industry leaders are recognizing the importance of evolving security practices to stay relevant and competitive.
Conclusion
In the realm of mobile application security, the stakes have never been higher. As this article illustrates, the rapid growth of mobile technologies has brought with it a host of vulnerabilities that threaten user data and organizational integrity. Common security threats such as:
- Insecure data storage
- Inadequate encryption
- Poor coding practices
underscore the urgent need for developers to adopt robust security protocols. The statistic that 82% of organizations have faced third-party data breaches serves as a stark reminder of the potential consequences of neglecting mobile app security.
To counter these threats, implementing best practices such as:
- Secure coding techniques
- Data encryption
- Regular security audits
is essential. These measures not only protect sensitive information but also build user trust in a digital landscape where security breaches can have devastating financial repercussions. The importance of continuous security practices cannot be overstated; organizations must remain proactive, adapting to new threats as they emerge. Leveraging advanced technologies, including AI and automation, can significantly enhance an organization's ability to detect and respond to vulnerabilities swiftly.
As mobile applications continue to play a pivotal role in everyday life and business operations, prioritizing security is no longer optional but a strategic necessity. By fostering a culture of security awareness and adhering to best practices, organizations can safeguard their applications and users against the evolving threat landscape. The future of mobile app development lies in its ability to integrate security seamlessly, ensuring that both innovation and protection go hand in hand.





