Introduction
The integration of the Industrial Internet of Things (IIoT) in e-commerce operations has revolutionized the industry, offering enhanced efficiency, real-time data analytics, and actionable insights. However, with increased connectivity and data sharing comes the heightened risk of cybersecurity threats. IIoT systems have become attractive targets for cybercriminals, leading to increased vulnerability to cyberattacks. Addressing these risks requires a comprehensive understanding of IIoT cybersecurity and the implementation of robust security measures. In this article, we will explore the importance of IIoT cybersecurity in e-commerce operations and discuss key strategies and best practices to enhance cybersecurity. We will also delve into real-life case studies that highlight successful implementations of IIoT cybersecurity measures and discuss future trends and predictions in IIoT cybersecurity. By understanding and prioritizing IIoT cybersecurity, businesses can protect their operations, maintain customer trust, and drive growth in the digital landscape.
1. Understanding the Importance of IIoT Cybersecurity in E-commerce Operations
The integration of the Industrial Internet of Things (IIoT) in e-commerce operations has been a significant game changer, offering real-time data streams, analytical capabilities, and actionable insights. These advantages can translate into enhanced efficiency, superior product quality, quick decision-making, and reduced equipment downtime and operational costs. However, the increased connectivity and data sharing that comes with IIoT technologies also bring along a host of cybersecurity risks.
IIoT systems, due to their extensive attack surface and often lax security measures, have become attractive targets for cybercriminals, leading to increased vulnerability to cyberattacks. These attacks often infiltrate operational technology (OT) equipment, starting from IT systems through social engineering techniques like phishing emails. The consequences of these cyberattacks can range from financial losses to damage to critical infrastructure, with losses accruing at an alarming rate of $1,000 per minute.
Addressing these risks requires e-commerce operations to not only understand but prioritize IIoT cybersecurity. This involves conducting a cybersecurity risk assessment to identify and prioritize security concerns in OT and IIoT environments. The risk assessment process includes defining the system, identifying the consequences of unintended access or behavior, enumerating known vulnerabilities, identifying threats, estimating likelihood, ranking risks, and developing a risk mitigation strategy.

Implementing a robust system monitoring and redundancy strategy can help mitigate the risks of system disruptions in e-commerce operations. By continuously monitoring the performance and availability of the system, potential issues can be identified and addressed proactively. Additionally, having redundant infrastructure in place, such as backup servers and failover mechanisms, can ensure uninterrupted operation in case of hardware or software failures.
Network segmentation, strong authentication, regular patching and updates, secure communication, intrusion detection and prevention systems, regular security audits, and employee training are all best practices to be implemented to secure e-commerce platforms.
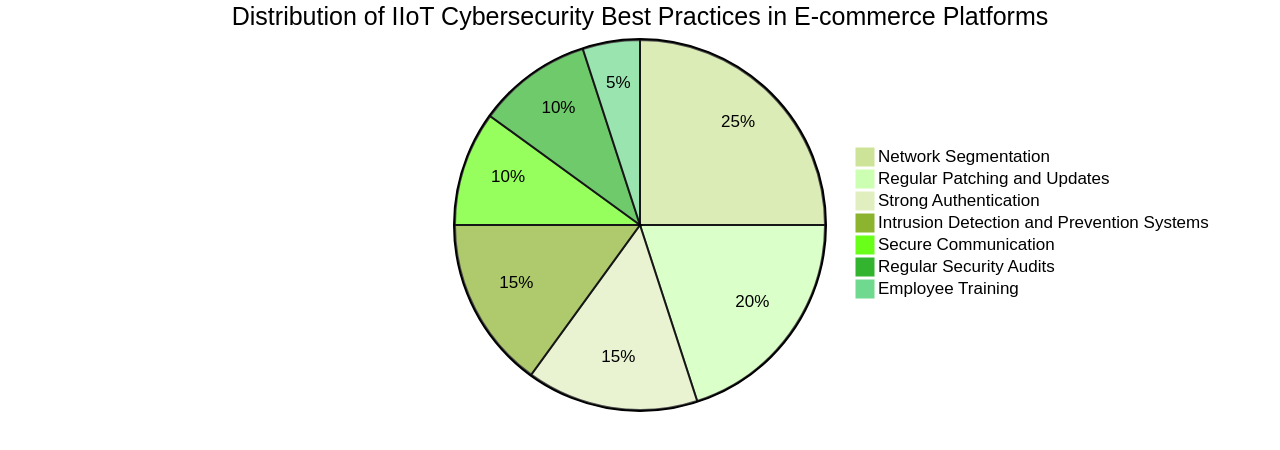
Additionally, ensuring secure access control mechanisms are in place, such as strong passwords, multi-factor authentication, and proper user roles and permissions is crucial. Implementing encryption protocols, such as SSL/TLS, can help protect sensitive customer data during transmission. Regularly updating and patching the platform's software and plugins is essential to address any vulnerabilities that may be exploited by hackers.
Governments, standards organizations, and semiconductor companies are also playing a proactive role in fortifying IIoT security. For example, the International Electrotechnical Commission (IEC) has developed standards (IEC 62443) to address cybersecurity for OT. Semiconductor companies like NXP provide security features for integrated circuits (ICs) used in industrial systems, such as secure boot mechanisms and secure key storage. Secure elements (SEs) are standalone ICs that provide the same level of security as on-chip solutions and can be integrated with microcontrollers (MCUs) used in IoT applications.
While IIoT technologies offer numerous benefits to e-commerce operations, they also introduce significant cybersecurity risks. To ensure the stability and success of e-commerce operations, it is imperative to understand and prioritize IIoT cybersecurity. This involves conducting comprehensive cybersecurity risk assessments, implementing robust security measures, and staying abreast of the latest cybersecurity standards and best practices.
2. Key Strategies for Enhancing IIoT Cybersecurity in E-commerce
As part of the e-commerce landscape, it's crucial to have a comprehensive, multi-pronged approach to enhance Industrial Internet of Things (IIoT) cybersecurity. This approach should include robust security protocols, data encryption, and routine system updates and patching to address vulnerabilities.
A key aspect of this strategy is data encryption. It is advisable to implement SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols for data protection. These protocols encrypt the communication between the user's browser and the e-commerce site, ensuring secure transmission of sensitive data like credit card information. Additionally, encryption algorithms can be employed to store and transmit data securely within the e-commerce system, preventing unauthorized access and maintaining data confidentiality and integrity.
Regular updating and patching of systems are equally important in ensuring the security and stability of the online platform. A systematic approach to software updates and patches, including regular monitoring for security vulnerabilities, is crucial. Establishing a schedule for regular system updates can help minimize disruptions, and testing updates and patches in a controlled environment before deployment ensures stability. Automated update procedures can also streamline the process and ensure prompt installation of critical security patches.
To address the human factor in security breaches, businesses should invest in advanced security tools capable of real-time threat detection and response. A team of software developers, designers, and engineers, such as those at BestToolbars.net, can provide tailored solutions to meet specific needs and questions, offering innovative solutions to protect your e-commerce platform from potential threats.
Creating a culture centered on security involves fostering open discussions about security breaches and creating an environment conducive to addressing security issues. This can be achieved by providing employee training on best practices and techniques to prevent cyber threats and protect sensitive data. Topics such as identifying phishing emails, using strong passwords, implementing two-factor authentication, and understanding the importance of regular software updates can be included in this training. Employees should also be trained to recognize and report any suspicious activities or potential security breaches.
In the context of IIoT, the risks and threats associated with connecting operational technology (OT) and information technology (IT) are significant. The removal of the air gap between OT and IT systems in IIoT has made industrial systems more susceptible to cyberattacks due to an expansive attack surface and often lack comprehensive security policies. Cyberattacks on industrial systems can lead to substantial financial losses, downtime, and damage to critical infrastructure.
Software running on OT equipment often lacks regular updates and security patches, making it vulnerable to attacks. These attacks often begin with social engineering tactics aimed at IT systems, which are then used to escalate the attack into the OT environment. To mitigate these risks, implementing robust email security measures, such as secure email gateways and email authentication protocols like SPF, DKIM, and DMARC, can help. Regular security audits, strong password policies, and regular software updates can also strengthen overall security.
In response to the security risks associated with attacks on public infrastructure, governments and standards organizations have taken measures to address these concerns. These include the EU Cybersecurity Act and the US National Industrial Security Program. Semiconductor vendors such as NXP have also stepped up by offering security features and services aimed at meeting the security challenges of IIoT. These include secure boot mechanisms, secure key storage, and secure elements.
Secure elements (SEs) are standalone integrated circuits (ICs) that provide the same level of security as on-chip solutions and can be integrated with microcontrollers (MCUs) to enhance security. However, managing keys and certificates for SEs is a significant challenge for original equipment manufacturers (OEMs), and semiconductor vendors offer services to support pre and custom provisioning of SEs and device identity management.
Given the severe consequences of poor security in IIoT systems - including safety risks, environmental damage, revenue loss, and damaged reputation - it is imperative that the right technical solutions, guidance, and support are in place to overcome these security challenges. Proactive cybersecurity measures provide several benefits. By implementing these measures, businesses can enhance the security of their online platforms and protect sensitive customer data from potential cyber threats. This not only instills trust in customers but also helps businesses comply with relevant data protection regulations.
3. Best Practices for Implementing IIoT Cybersecurity Measures
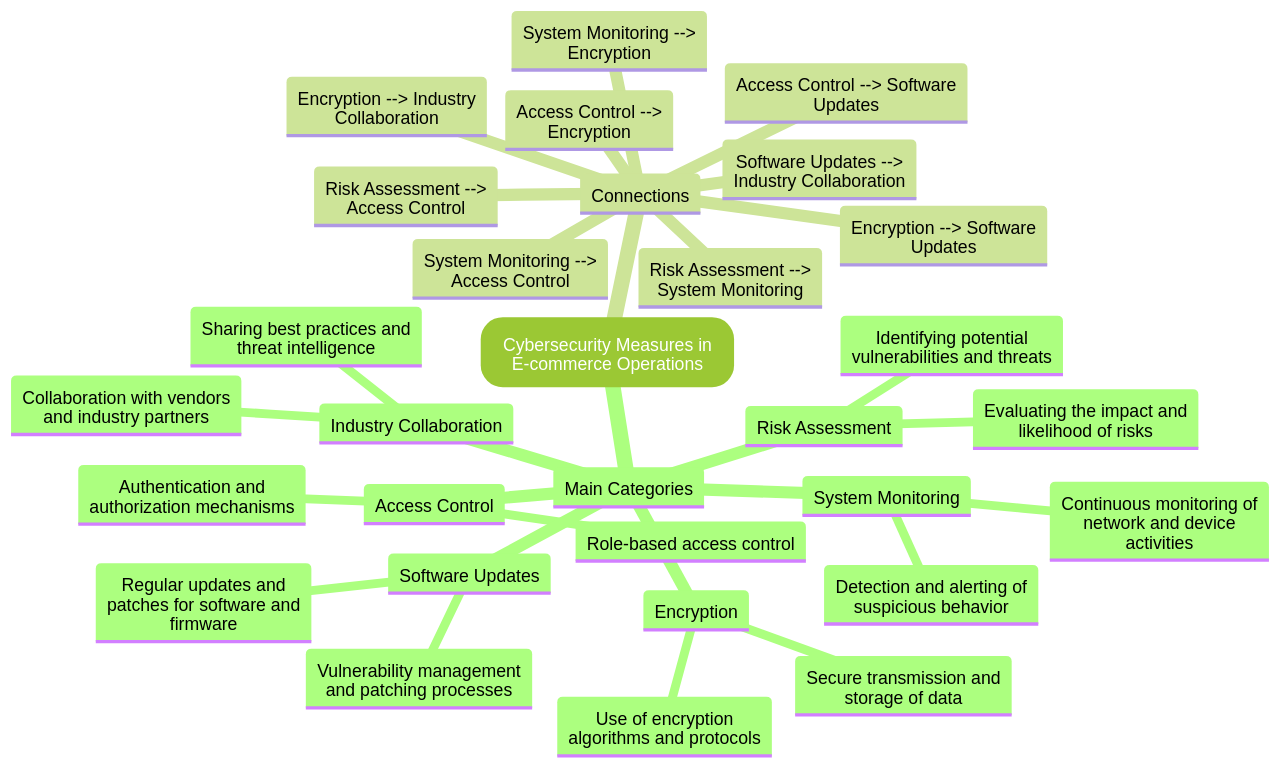
The integration of Industrial Internet of Things (IIoT) principles into e-commerce necessitates a robust and well-structured cybersecurity strategy. A meticulous risk assessment forms the foundation of this strategy, helping businesses identify potential vulnerabilities and threats. The process involves deploying sensors and connected devices across key infrastructure sectors, such as transport and energy.
In the energy sector, for instance, Distributed Energy Resources (DERs), like solar photovoltaics, are networked with sensors, data transfer systems, and communication systems to manage energy flow in the distribution grid. To safeguard information exchanges between commercial and utility-scale DERs and electric distribution grid operations, cybersecurity threats and vulnerabilities need to be proactively addressed.
The National Cybersecurity Center of Excellence (NCCoE) offers a practical solution for this. They have developed a reference architecture using commercially available products that demonstrates how to apply cybersecurity capabilities such as communications, data integrity, malware detection, network monitoring, authentication, access control, and cloud-based analysis. These measures aim to secure distributed endpoints, reduce the attack surface for DERs in the IIoT, and ensure the secure and reliable operation of DERs and the overall energy distribution grid.
After the risk assessment, businesses should create a cybersecurity strategy encompassing firewalls, intrusion detection systems, and data encryption. The Industry IoT Consortium's Industrial Internet of Things Security Framework (IISF) is a helpful resource in this context. It offers architectures and best practices for building trustworthy systems and addresses crucial considerations such as security, safety, reliability, privacy, and resiliency. The IISF is a collaborative endeavor that brings together security experts from various organizations to safeguard ICS/SCADA systems.
To ensure the effectiveness and currency of these security measures, regular audits and penetration testing are crucial. Additionally, a response plan should be in place for potential security incidents. This plan should include identifying, containing, and resolving the issue, as well as communicating with stakeholders. The IISF update underlines that cybersecurity is a non-discriminatory threat that poses a significant risk to global safety and security. Hence, industry collaboration and consensus are paramount in addressing cybersecurity threats.
In essence, the successful integration of IIoT cybersecurity measures in e-commerce operations necessitates careful planning, robust strategies, regular audits, and a well-prepared response plan for potential security incidents. Resources such as the NCCoE's reference architecture and the IISF can significantly assist businesses in constructing resilient and secure e-commerce platforms.
When strategizing IIoT cybersecurity risk assessment, it's essential to follow a systematic approach. Start by identifying the assets and systems that make up the IIoT infrastructure. Then, assess the potential threats and vulnerabilities that could affect these assets. Next, determine the likelihood and impact of each threat, and prioritize them based on their risk level. Once the risks are prioritized, implement appropriate security controls to mitigate or manage these risks. Regularly monitor and review the effectiveness of the controls, and make necessary adjustments as needed. It's also critical to stay updated on the latest cybersecurity threats and best practices to ensure ongoing protection.
Effective cybersecurity measures for IIoT are crucial to guarantee the security and integrity of the connected devices and networks. It's essential to protect against potential cyber threats and unauthorized access to critical systems and data. Implementing strong authentication mechanisms, such as two-factor authentication or biometric authentication, is one important measure. Regularly updating and patching the software and firmware of the IIoT devices is another crucial step. Implementing encryption protocols can help secure the communication between IIoT devices and the backend systems. Regular monitoring and logging of IIoT devices and systems is also crucial. Lastly, educating employees and users about cybersecurity best practices is essential. Training them on how to identify and report potential security threats can help prevent successful cyber attacks.
By implementing these cybersecurity measures, organizations can enhance the security of their IIoT implementation and protect their critical systems and data from potential cyber threats.
4. Case Studies: Successful Implementation of IIoT Cybersecurity in E-commerce
The potential of IIoT cybersecurity measures in e-commerce operations is underscored by the successful practices of leading global companies such as LG Electronics and Coca Cola İçecek (CCI).
LG Electronics introduced the LG ThinQ brand, a line of smart products powered by artificial intelligence. As the number of smart devices connected to their servers surged, LG faced the challenge of securing resources for server development and operations. The solution was the development of an IoT platform for ThinQ appliances. LG migrated its IT platform for home appliances, including over 1000 servers, to Amazon Web Services (AWS) in 2016. This strategic move enabled LG to leverage AWS IoT and its serverless architecture, resulting in a significant reduction in management time for its IoT platform. By adopting AWS for its IoT platform, LG not only saved 80% in development costs but also enabled developers to focus on writing business logic for service scenarios. LG Electronics continues to utilize AWS services for air quality monitoring services, customer service chatbots, and energy solutions.
Coca Cola İçecek (CCI) transformed its 26 bottling plants by building a digital twin using AWS services. This strategy aimed to improve asset optimization, enable sustainability, and avoid downtime in manufacturing processes. The digital twin automated the shop floor and provided CCI with a holistic view of its manufacturing processes. AWS Professional Services helped build a scalable analytics solution using AWS IoT Sitewise, allowing CCI operators to monitor processes in near real-time and make data-driven decisions. The implementation of the digital twin solution resulted in annual savings of 20% on electricity and 9% on water for CCI.
These case studies demonstrate the potential of IIoT cybersecurity measures in e-commerce operations. By leveraging the latest technologies, businesses can significantly enhance their digital security, maintain the trust of their clients, and deliver high-quality projects, all while realizing substantial cost savings.
Implementing IIoT cybersecurity measures requires a careful approach to ensure the protection of connected devices and data. Conducting a comprehensive risk assessment is a key step in identifying potential vulnerabilities and threats specific to your IIoT environment. It's also essential to implement strong access controls, encrypt data in transit and at rest, and regularly update and patch systems. Monitoring for anomalies and conducting regular security audits can help identify weaknesses or gaps in your defenses, and establishing incident response plans ensures a swift and effective response in the event of a cybersecurity incident.
When it comes to cybersecurity in e-commerce, staying up-to-date with the latest technologies is crucial. Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols, Two-Factor Authentication (2FA), Web Application Firewalls (WAFs), Tokenization, Machine Learning and Artificial Intelligence (AI) are some of the advanced technologies and practices that can help protect e-commerce websites and customer data from cyber threats. Regular Security Updates and Patching are also essential for protecting against known vulnerabilities.
To ensure robust security protocols for protecting e-commerce operations, it's important to implement industry best practices. This includes using secure communication protocols such as HTTPS, implementing strong authentication mechanisms such as multi-factor authentication, and conducting regular security audits and vulnerability assessments. Implementing a robust firewall and intrusion detection system can help detect and mitigate any potential security threats.
Regular system updates are crucial to address vulnerabilities in e-commerce platforms. These updates ensure that the e-commerce platform remains secure and protects sensitive customer information, providing a seamless and secure shopping experience for customers.
When crafting innovative solutions for specific needs, a proactive approach to cybersecurity is crucial. This includes conducting thorough security assessments, implementing secure coding practices, and regularly updating and patching software to address any vulnerabilities. By taking a proactive approach to cybersecurity, businesses can ensure that their applications are built with a strong defense against potential cyber attacks.
Maintaining client trust through cybersecurity measures is essential. This can be achieved by implementing secure communication protocols, encryption techniques, and regularly updating security measures to protect against potential threats. Conducting regular security audits and vulnerability assessments can help identify and mitigate any potential vulnerabilities in the system.
To ensure the delivery of high-quality projects with strong cybersecurity measures, it's important for software developers, designers, and engineers to work harmoniously. Crafting innovative solutions specific to the needs and questions of the project, they can provide a secure and reliable end product. Consulting services and access to top-tier talent can help with testing market fit and ensuring the best cost-effective and flexible solutions.
For e-commerce businesses, implementing robust cybersecurity measures is crucial to protect against potential threats. By ensuring the security of their Internet of Things (IoT) devices and networks, businesses can safeguard customer data, financial transactions, and sensitive information. Strong encryption protocols, regular software updates, secure payment gateways, and multi-factor authentication are some of the key cybersecurity measures that e-commerce businesses should consider implementing to enhance their security posture. Regular security audits, employee training programs, and establishing incident response plans can also help in effectively mitigating and managing cyber threats in the rapidly evolving digital landscape.
5. Future Trends and Predictions in IIoT Cybersecurity
As the sophistication of Industrial Internet of Things (IIoT) continues to grow, so does the complexity and precision of cybersecurity threats. Businesses need to be prepared for these challenges, which are projected to incorporate advanced technologies such as Artificial Intelligence (AI) and Machine Learning (ML). These technologies can be exploited by cybercriminals for intricate attacks, but they can also augment cybersecurity by facilitating real-time detection of threats and automated responses[^1^].
AI and ML are revolutionizing cybersecurity. They are being employed to develop sophisticated threat detection and mitigation systems. AI and ML algorithms can sift through vast amounts of data and identify patterns that may signify a cyber-attack. This enables real-time detection and mitigation of threats. Furthermore, AI and ML can automate security processes like incident response and vulnerability management, making cybersecurity more efficient and effective[^1^].
In the context of AI and ML, software companies like BestToolbars are developing cost-effective and adaptable solutions by leveraging the expertise of developers, designers, and engineers. They provide a variety of consulting services, such as market testing, bug fixes, and full outsourcing, to ensure that products align with market demands and secure their clients' systems[^2^].
One such solution is real-time threat detection that analyzes website traffic and user behavior. AI and ML algorithms are employed to identify patterns and abnormalities that suggest potential threats or malicious activities. This solution can continuously monitor incoming traffic, analyze various data points, and flag potential threats. For instance, if a user suddenly sends a high number of requests within a short period, it could be an indication of a botnet attack[^3^].
To implement an automated response to cybersecurity threats, it is imperative to have a team of software developers, designers, and engineers crafting innovative solutions. BestToolbars offers a range of services that include one-on-one consultations to address specific needs and questions, testing for market fit, and providing consulting services to launch minimum viable products[^4^].
Protecting data and privacy is vital in the realm of cybersecurity. By ensuring the confidentiality, integrity, and availability of data, organizations can safeguard sensitive information from unauthorized access. Effective data protection measures, such as encryption and access controls, help prevent data breaches and mitigate the risk of cyber-attacks[^5^].
The future of IIoT cybersecurity is multifaceted and challenging. Businesses need to stay updated with the latest developments, ensure compliance with evolving regulations, and leverage advanced technologies to enhance their cybersecurity measures. The balance between harnessing the potential of IIoT and ensuring cybersecurity and privacy will be a key factor in the success of e-commerce operations[^9^].
Conclusion
In conclusion, the integration of the Industrial Internet of Things (IIoT) in e-commerce operations offers numerous benefits such as enhanced efficiency, real-time data analytics, and actionable insights. However, it also brings along significant cybersecurity risks. IIoT systems have become attractive targets for cybercriminals due to their extensive attack surface and often lax security measures. Addressing these risks requires a comprehensive understanding of IIoT cybersecurity and the implementation of robust security measures. This involves conducting a cybersecurity risk assessment, implementing strong authentication mechanisms, regular patching and updates, secure communication protocols, intrusion detection systems, and regular security audits. By prioritizing IIoT cybersecurity and implementing these best practices, businesses can protect their operations, maintain customer trust, and drive growth in the digital landscape.
Furthermore, it is crucial for businesses to stay up-to-date with future trends and predictions in IIoT cybersecurity. As the sophistication of cyber threats continues to grow, advanced technologies such as Artificial Intelligence (AI) and Machine Learning (ML) will play a significant role in enhancing cybersecurity measures. AI and ML algorithms can detect patterns that may signify a cyber attack in real-time and automate security processes like incident response and vulnerability management. Businesses should also leverage the expertise of software developers, designers, and engineers to develop innovative solutions tailored to their specific needs. Additionally, protecting data and privacy through effective data protection measures is essential for safeguarding sensitive information from unauthorized access.
To ensure the stability and success of e-commerce operations in the rapidly evolving digital landscape, businesses must prioritize IIoT cybersecurity by implementing robust security measures, staying updated with future trends and predictions, and leveraging advanced technologies. By taking proactive steps to enhance cybersecurity measures, businesses can protect their operations from cyber threats while maintaining customer trust and driving growth in the digital landscape.





