Introduction
In an age where mobile applications are integral to daily life, the importance of securing these platforms cannot be overstated. As threats evolve and become more sophisticated, developers must navigate a complex landscape of vulnerabilities that could compromise user data and brand trust. From insecure data storage to code injection attacks, the risks are numerous and varied.
By understanding the common threats and adopting best practices for security, developers can significantly enhance the resilience of their applications. This article delves into the critical aspects of mobile application security, offering insights into effective strategies, the necessity of rigorous testing, and the financial implications of security breaches.
As the industry shifts towards a more security-centric approach, the insights presented here serve as a vital guide for developers aiming to protect their software and users in an increasingly perilous digital environment.
Understanding Mobile Application Security
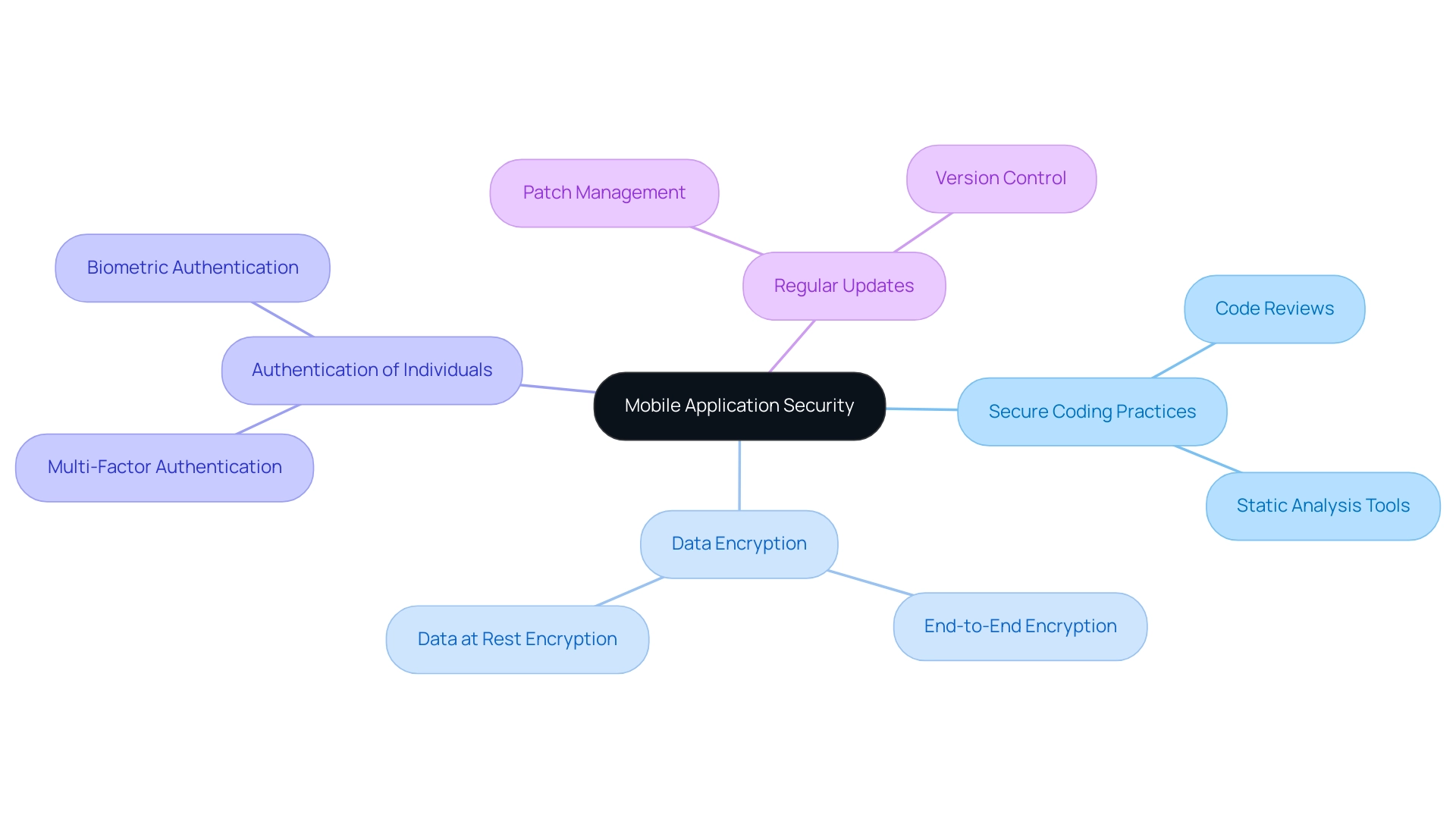
The protection of mobile apps and security is a vital component of safeguarding programs from various threats that may endanger their confidentiality, integrity, and availability. Essential elements of this protection framework include:
- Secure coding practices
- Data encryption
- Authentication of individuals
- Implementation of regular updates
These measures are essential not only for creating software that functions efficiently but also for protecting user data and fostering trust in the brand.
As emphasized by IBM, 'The average total cost of a mega breach (50-60 million records) was $332 million,' underscoring the financial implications of insufficient protective measures. Moreover, with 58 percent of organizations anticipated to shift their software portfolios to a public cloud in the upcoming two years, comprehending mobile apps and security becomes increasingly vital. To navigate the complexities of portable device protection, developers should engage with industry standards such as the OWASP Mobile Security Project.
This initiative provides extensive guidelines aimed at assisting in the implementation of strong protective measures in handheld software, ensuring that developers are well-prepared to reduce risks and improve the overall resilience of their programs. Additionally, the Application Protection market is projected to generate approximately $6.97 billion in 2024, with a forecasted annual growth rate of 14.14% from 2024 to 2028, indicating a significant and growing focus on application protection.
Identifying Common Mobile App Security Threats
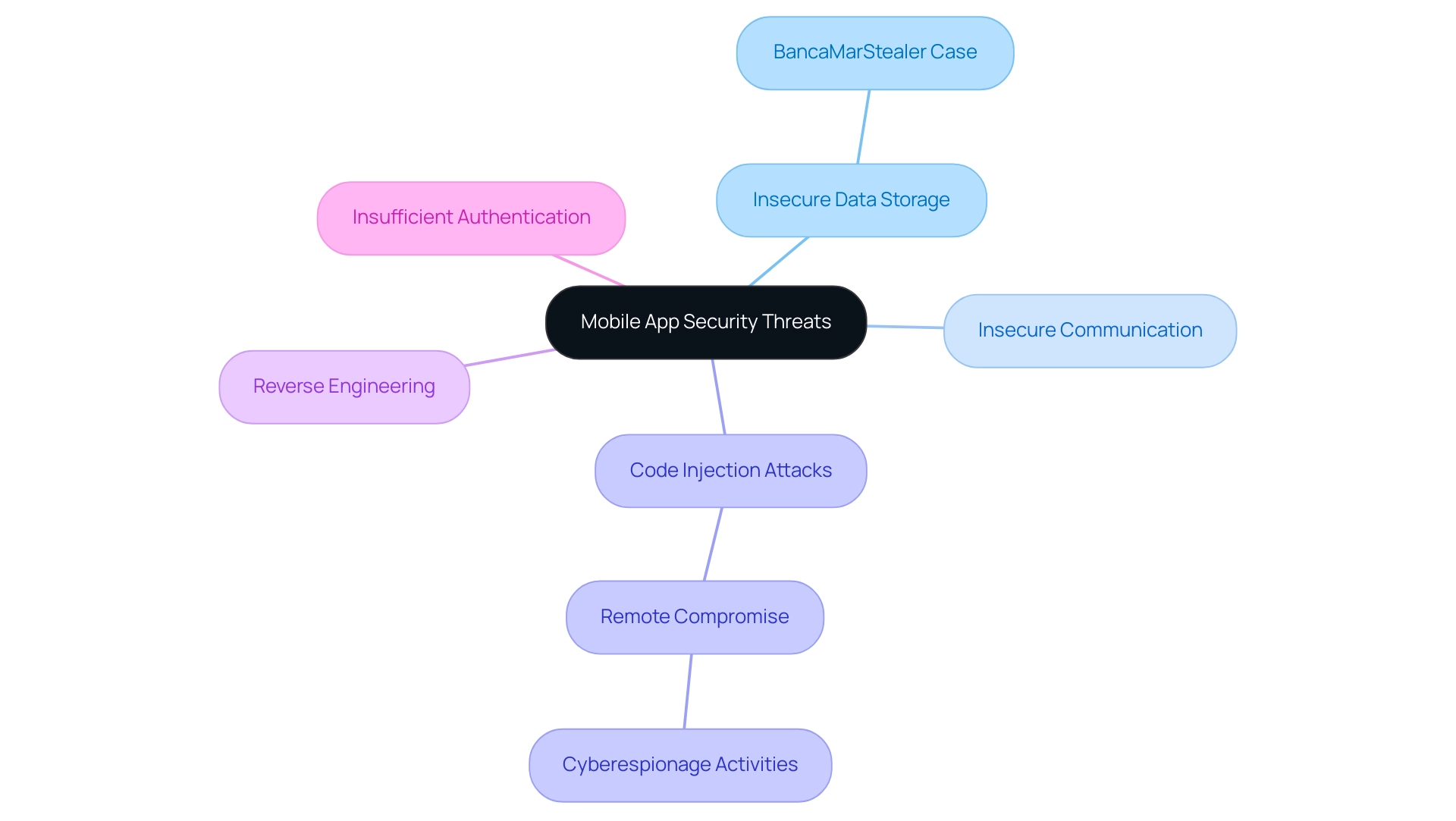
As the digital environment progresses, threats to mobile apps and security continue to present considerable dangers to both developers and consumers. Key vulnerabilities include:
-
Insecure Data Storage: When sensitive information such as passwords or personal details is stored without encryption, it becomes vulnerable to breaches. This risk is underscored by the recent BancaMarStealer case, where a mobile trojan specifically targeted insecure storage to phish for banking credentials, demonstrating the high severity of such threats.
-
Insecure Communication: The failure to encrypt data during transmission leaves it exposed to interception by malicious actors. This can lead to unauthorized access to confidential information, significantly undermining trust.
-
Code Injection Attacks: Attackers may exploit vulnerabilities within a program’s code to inject malicious scripts, which can compromise app functionality and data integrity. The potential for remote compromise is a concern, particularly as advanced threat actors employ sophisticated techniques to turn devices into surveillance tools, as seen in various cyberespionage activities.
-
Reverse Engineering: By decompiling software, cybercriminals can uncover vulnerabilities or extract sensitive data. This practice not only exposes the app to further exploitation but also puts personal data at risk.
-
Insufficient Authentication: Weak authentication protocols can enable unauthorized users to gain access to the application, further heightening risks.
Furthermore, recent reports of a zero-day vulnerability in the V8 engine, which supports Chromium and versions of Google Chrome for handheld devices, highlight the evolving nature of app security threats. Given the rapid increase in threats related to mobile apps and security, with Lookout's Security Cloud ingesting over 325 million apps and app versions, understanding these vulnerabilities is crucial. As Milan Singh Thakur aptly noted in his final review, "[insert specific context or use of the quote here]".
Developers must implement strong protective strategies to secure their software effectively and safeguard data from emerging threats.
Best Practices for Securing Mobile Applications
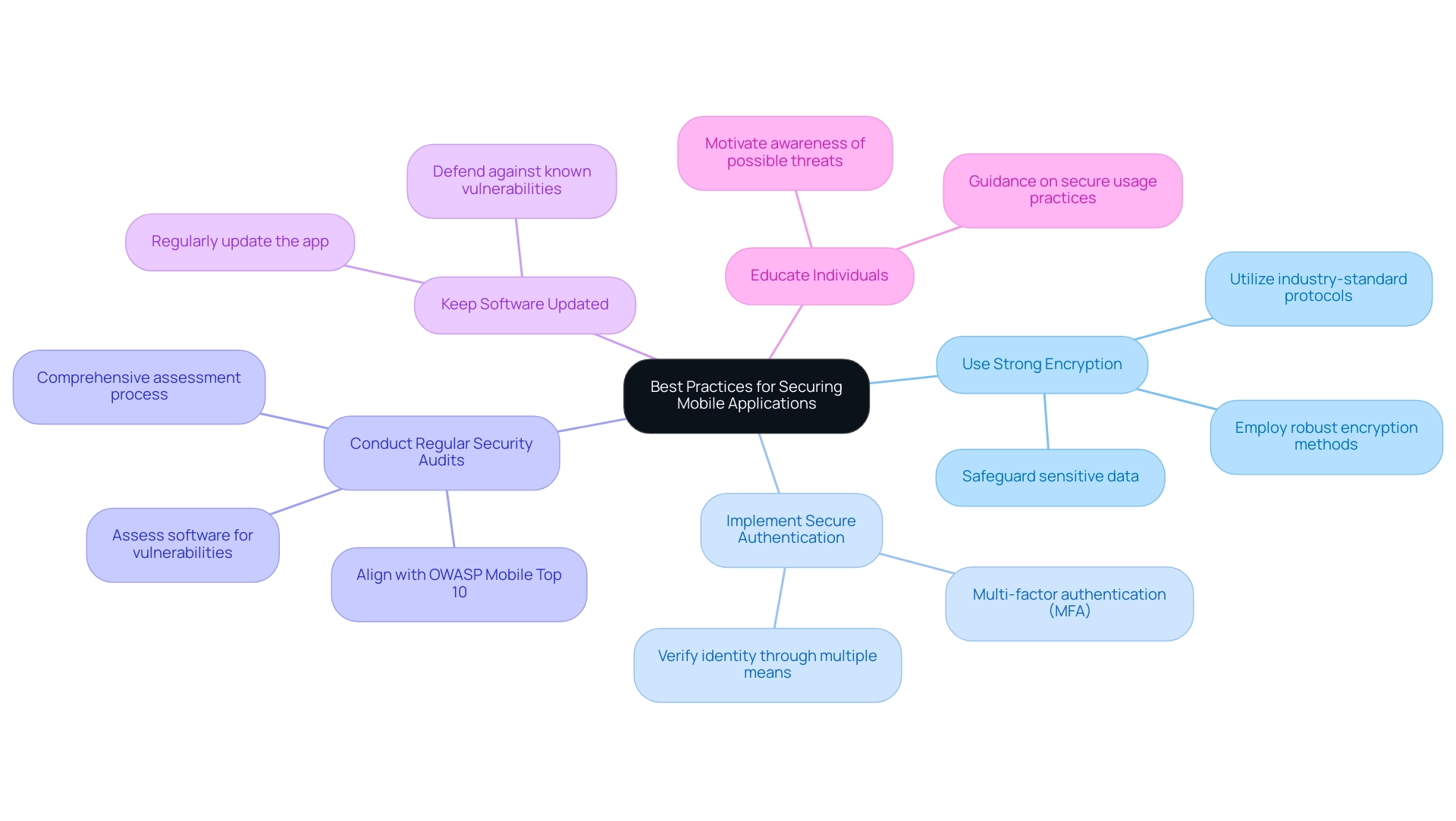
To strengthen the protection of mobile applications, developers must prioritize the following best practices:
-
Use Strong Encryption: Safeguard sensitive data by employing robust encryption methods for data both at rest and in transit, utilizing industry-standard protocols to prevent unauthorized access.
-
Implement Secure Authentication: Multi-factor authentication (MFA) is a crucial approach to improve protection for account holders. As Build38 aptly states, mobile apps and security are no longer optional considerations; they are critical necessities. Implementing MFA can significantly bolster protection against unauthorized access by requiring users to verify their identity through multiple means.
-
Conduct Regular Security Audits: It is vital to periodically assess the software for vulnerabilities and rectify any identified issues. Regular audits help ensure that the application remains resilient against emerging threats and aligns with the latest OWASP Mobile Top 10 list of vulnerabilities, which is determined through a data-driven and unbiased approach. The OWASP Mobile Top 10 Methodology emphasizes the importance of a comprehensive assessment process, ensuring that the most common and impactful vulnerabilities are addressed effectively.
-
Keep Software Updated: Regularly updating the app and its dependencies is crucial for defending against known vulnerabilities. Keeping up with updates can reduce the risk presented by newly discovered exploits.
-
Educate Individuals: Providing individuals with guidance on secure usage practices is paramount. Motivate them to maintain their devices current and aware of possible threats to improve overall application safety.
By applying these best practices, developers can greatly reduce the chance of breaches and ensure mobile apps and security to safeguard user data. The recent OWASP Top 10 list emphasizes the most significant vulnerabilities in portable software, reinforcing the need for continuous vigilance. Moreover, as penalties for violations of EU privacy regulations have risen to $1.2 billion, the repercussions of ignoring app protection are severe, making it essential for e-commerce directors to embrace these suggested practices.
The Importance of Security Assessments and Testing
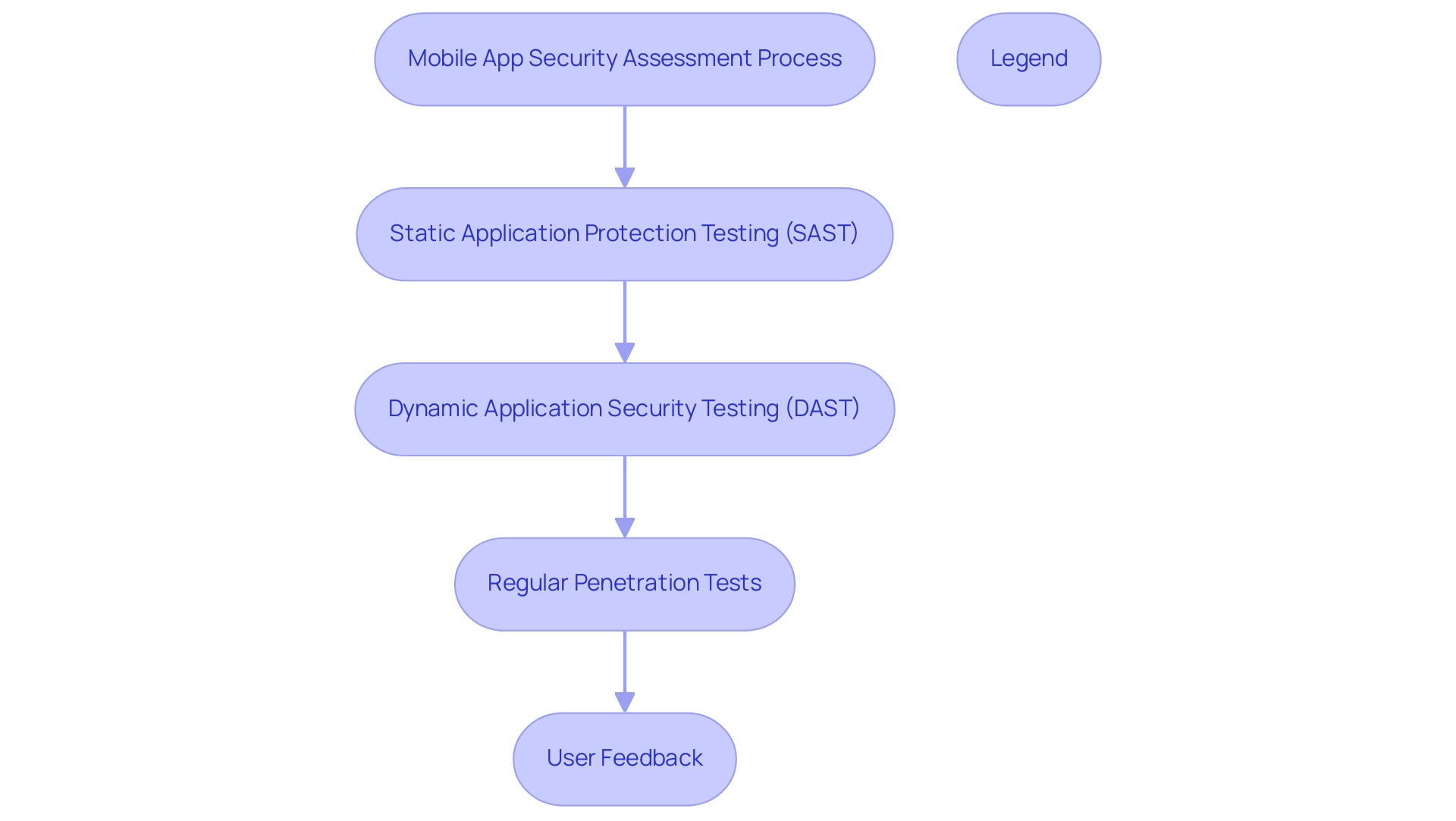
Efficient evaluations and testing techniques are essential to maintaining the integrity of mobile apps and security. As the industry faces increasing threats, developers must implement a multifaceted approach that includes:
- Static Application Protection Testing (SAST): This technique involves analyzing source code for weaknesses before the system is deployed, allowing for early detection of potential vulnerabilities.
- Dynamic Application Security Testing (DAST): By evaluating the application in a runtime environment, DAST identifies vulnerabilities that may not be evident in static analysis, providing a comprehensive view of the application’s protection stance.
- Regular Penetration Tests: Conducting simulations of real-world attacks enables developers to evaluate the app's defenses and uncover weaknesses that could be exploited by malicious actors. Shreya Bose, a community contributor, emphasizes that
Exhaustive app testing is the only way to guarantee such consistency,
reinforcing the necessity of rigorous testing protocols. - User Feedback: Encouraging users to report issues related to safety fosters a proactive culture and creates a feedback loop that enhances overall awareness.
Additionally, it is crucial to consider online payment protection measures like ASC for Issuers and the 3DS Server for Acquirers, especially in relation to mobile apps and security. These elements play an essential part in safeguarding sensitive transaction information, further emphasizing the necessity for thorough risk evaluations in mobile apps and security.
Incorporating these evaluations into the development lifecycle of mobile apps and security is essential for promptly identifying and addressing vulnerabilities. The case study titled 'Application Protection Overview' illustrates how adopting software protection practices helps mitigate risks, ensuring systems are safe and minimizing potential financial losses and reputational harm.
Considering that 80% of users depend on widely used browsers such as Google Chrome and Mozilla Firefox, ensuring program compatibility across these platforms further highlights the significance of strong protective measures. As we move into 2024, the relevance of security assessments becomes increasingly clear, particularly regarding mobile apps and security, as organizations face heightened scrutiny over data privacy. By adopting these methodologies, companies not only mitigate risks but also safeguard their reputation and financial integrity.
Conclusion
The significance of mobile application security cannot be overstated in today's digital landscape. As highlighted throughout this article, developers face a myriad of threats, from insecure data storage to sophisticated code injection attacks. Understanding these vulnerabilities is essential for creating applications that not only function well but also protect user data and enhance brand trust. The financial repercussions of inadequate security are staggering, emphasizing the need for a proactive approach to safeguarding applications.
Implementing best practices such as:
- Strong encryption
- Secure authentication
- Regular security audits
can significantly reduce the risks associated with mobile applications. Moreover, embracing comprehensive security assessments and testing methodologies ensures that vulnerabilities are identified and addressed promptly. As the market for application security continues to grow, it is imperative for developers to stay informed about evolving threats and adopt industry standards to fortify their applications.
In conclusion, prioritizing mobile application security is not just a technical necessity; it is a critical component of maintaining user trust and safeguarding brand reputation. By adopting a security-centric mindset and implementing robust security measures, developers can effectively mitigate risks, enhance the resilience of their applications, and ultimately contribute to a safer digital environment for all users.





