Introduction
In a digital landscape where cyber threats are ever-evolving, web application penetration testing has emerged as a critical line of defense for organizations seeking to safeguard their sensitive data and maintain customer trust. This proactive approach simulates cyber attacks to uncover vulnerabilities that could be exploited by malicious actors, highlighting the necessity for regular security assessments.
With alarming statistics revealing that a significant percentage of web applications, including popular platforms like WordPress, harbor vulnerabilities, the stakes have never been higher. As businesses navigate the complexities of modern security challenges, understanding the common pitfalls and employing effective tools and methodologies becomes essential for fortifying their defenses.
This article delves into the intricacies of web application penetration testing, offering insights into best practices, common vulnerabilities, and the latest tools to ensure robust security measures are in place.
Understanding Web Application Penetration Testing
Testing web applications for vulnerabilities serves as a crucial simulated cyber attack designed to uncover weaknesses within your web application that malicious actors could exploit. This comprehensive analysis evaluates the application’s protective stance, focusing on potential weaknesses in its design, implementation, and configuration. Significantly, recent data shows that 18% of WordPress sites have at least one weakness, highlighting the essential need for organizations to prioritize risk evaluations.
Regular security assessments, particularly testing web applications for vulnerabilities, are not just a precaution; they are a vital strategy for safeguarding e-commerce platforms and protecting sensitive customer information. By proactively identifying security flaws through testing web applications for vulnerabilities, businesses can implement corrective measures before these vulnerabilities are exploited in real-world scenarios. As highlighted by industry specialists, organizations should invest in regular security assessments to ensure their systems and networks remain secure and their data protected.
With around 5,600 ransomware incidents documented between January 2023 and February 2024, the need for efficient security assessment methods cannot be overstated. Additionally, it is essential to consider mobile risks, such as reverse engineering and compromised services, which can pose significant threats to applications. The influence of emerging technologies, such as cloud computing, also plays a vital role in shaping testing practices, as organizations must adjust their protective measures to guard against evolving cyber threats.
Staying ahead of the latest trends in web application security weaknesses is crucial for maintaining robust defenses and ensuring customer trust.
Preparing for a Successful Penetration Test
To ensure a successful security assessment, it is crucial to begin with a well-defined scope. This entails clearly identifying the applications that will be evaluated, the specific methods to be employed, and any particular weaknesses that should be prioritized. According to Brian Tant, chief penetration assessment officer at Axis, "If not addressed within 7-8 months, these weaknesses remain and align with the next yearly pen evaluation."
Therefore, addressing these weaknesses promptly is essential. Gathering a group equipped with the necessary expertise and tools is essential for effective execution in testing web applications for vulnerabilities, including:
- Vulnerability scanners
- Recognized evaluation frameworks
Furthermore, it is important to engage all stakeholders early in the process to secure the required permissions for conducting the test.
A relevant case study is the Payment Card Industry Data Security Standard (PCI DSS), which outlines security requirements for organizations handling payment card data. Penetration testers must align their activities with PCI DSS compliance requirements to avoid compromising cardholder data and facing fines. Keeping comprehensive documentation of the evaluation environment and objectives not only streamlines the assessment process but also improves communication among team members.
Following these best practices is crucial for enhancing assessment results in 2024.
Identifying Common Web Application Vulnerabilities
Comprehending typical web application weaknesses is crucial for efficient testing web applications for vulnerabilities. Key weaknesses include:
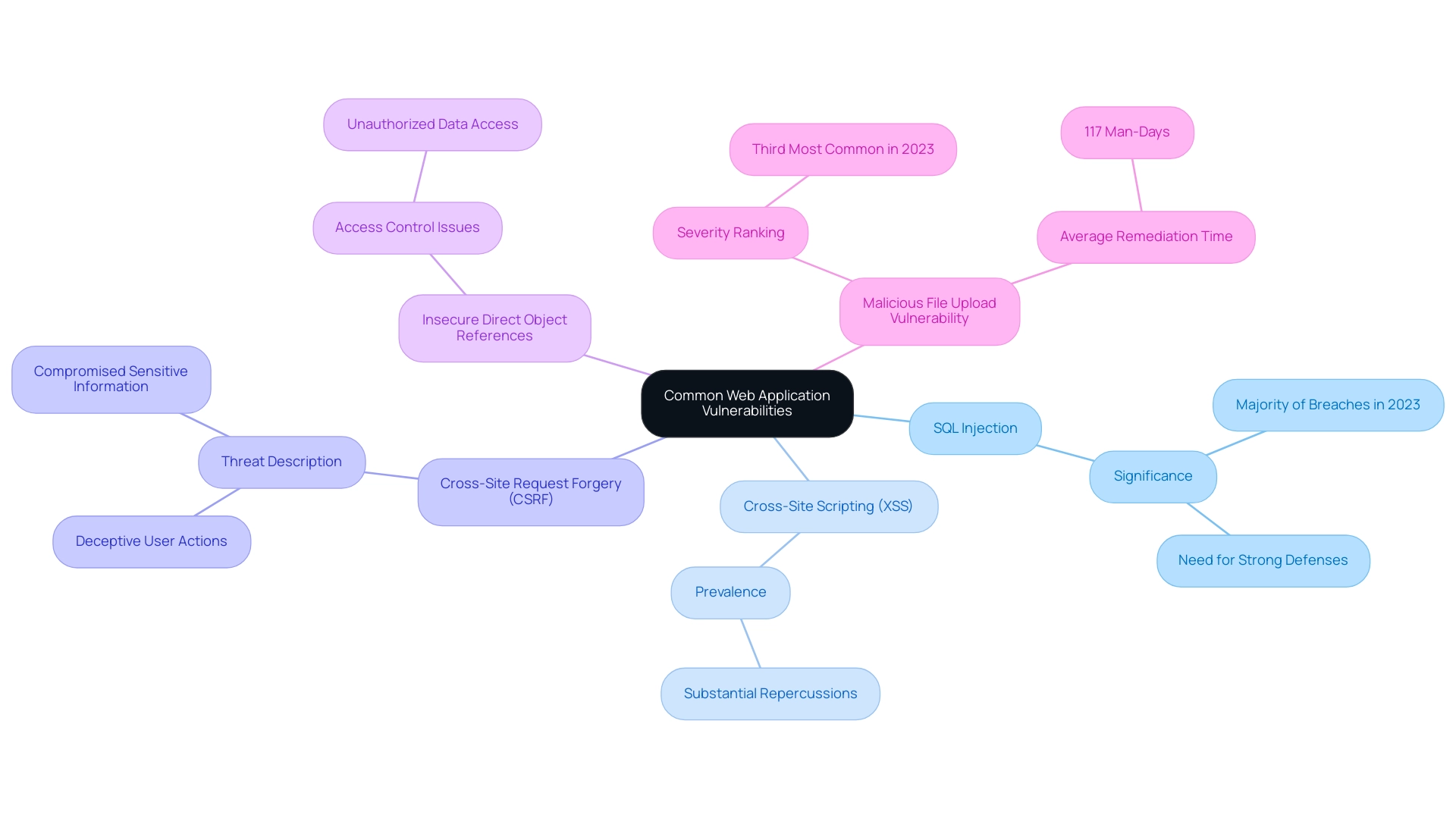
- SQL Injection: This occurs when attackers manipulate SQL queries, enabling unauthorized access to sensitive data. In 2023, SQL injection attacks represented a significant portion of breaches, emphasizing the necessity for strong defenses against this threat.
- Cross-Site Scripting (XSS): Malicious scripts are injected into web pages, targeting users to steal data or hijack sessions. Recent reports indicate that XSS remains a prevalent threat, with organizations experiencing substantial repercussions from such attacks.
- Cross-Site Request Forgery (CSRF): In this scenario, attackers deceive users into executing unwanted actions on web applications where they are authenticated, potentially compromising sensitive information.
- Insecure Direct Object References: This issue arises from inadequate access controls, allowing users to access unauthorized data easily.
Knowledge of these weaknesses is not only advantageous but essential for testing web applications for vulnerabilities, as it helps in recognizing possible threats and applying effective protective measures. The context of web application threats is highlighted by the approximately 5,600 reported ransomware incidents between January 2023 and February 2024, indicating a growing concern for organizations. As Malwarebytes points out, remote employees have led to security breaches in 20 percent of organizations during the pandemic, stressing the urgency for organizations to tackle these weaknesses proactively. Furthermore, the case study on Malicious File Upload Issues, which ranked as the third most common high/critical severity threat in 2023, illustrates the real-world impact of such dangers, with an average remediation time of 117 man-days, showcasing the substantial challenge organizations face in managing these risks.
Tools and Methodologies for Effective Testing
To effectively enhance your penetration evaluation efforts, leveraging a combination of robust tools and established methodologies is crucial. Among the most effective tools are:
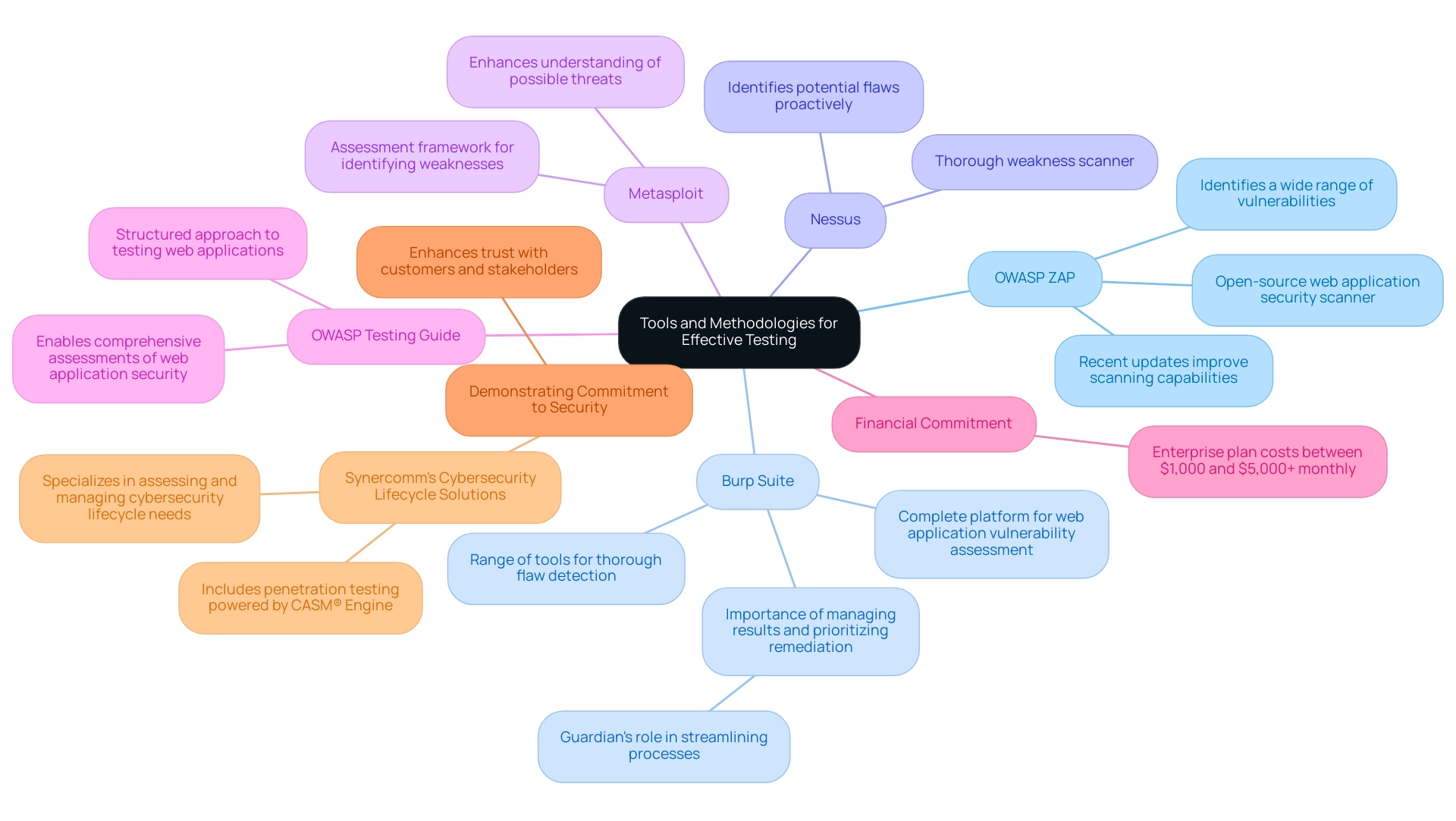
- OWASP ZAP: This open-source web application security scanner is acclaimed for its ability to identify a wide range of vulnerabilities, making it an indispensable asset in any security toolkit. Its recent updates have further improved its scanning capabilities, ensuring that it remains relevant in the face of evolving threats.
- Burp Suite: Known for its adaptability, Burp Suite provides a complete platform for web application vulnerability assessment. It offers a range of tools designed for various facets of security evaluation, including practical applications that enable thorough flaw detection. Expert insights stress the importance of managing results and prioritizing remediation efforts, highlighting the role of solutions like Guardian, which can streamline this process. Guardian notes, "While web application security assessment tools are essential for detecting weaknesses, handling the outcomes and prioritizing remediation actions can be difficult."
- Nessus: As a thorough weakness scanner, Nessus excels at identifying potential flaws within web applications, enabling teams to address issues proactively before they can be exploited.
- Metasploit: This assessment framework enables professionals to identify and exploit weaknesses, enhancing comprehension of possible threats to applications.
Integrating methodologies like the OWASP Testing Guide guarantees a structured approach to testing web applications for vulnerabilities, enabling comprehensive assessments of web application security. Investing in these tools can vary from $1,000 to $5,000+ monthly for enterprise plans, highlighting the financial commitment necessary for effective security assessments. Additionally, Synercomm's Cybersecurity Lifecycle Solutions exemplify how organizations can utilize testing web applications for vulnerabilities as an integral part of a comprehensive cybersecurity management strategy.
By utilizing these tools in tandem, organizations can demonstrate a commitment to security that enhances trust among customers and stakeholders, ultimately contributing to a more resilient cybersecurity posture.
Post-Test Reporting and Remediation Strategies
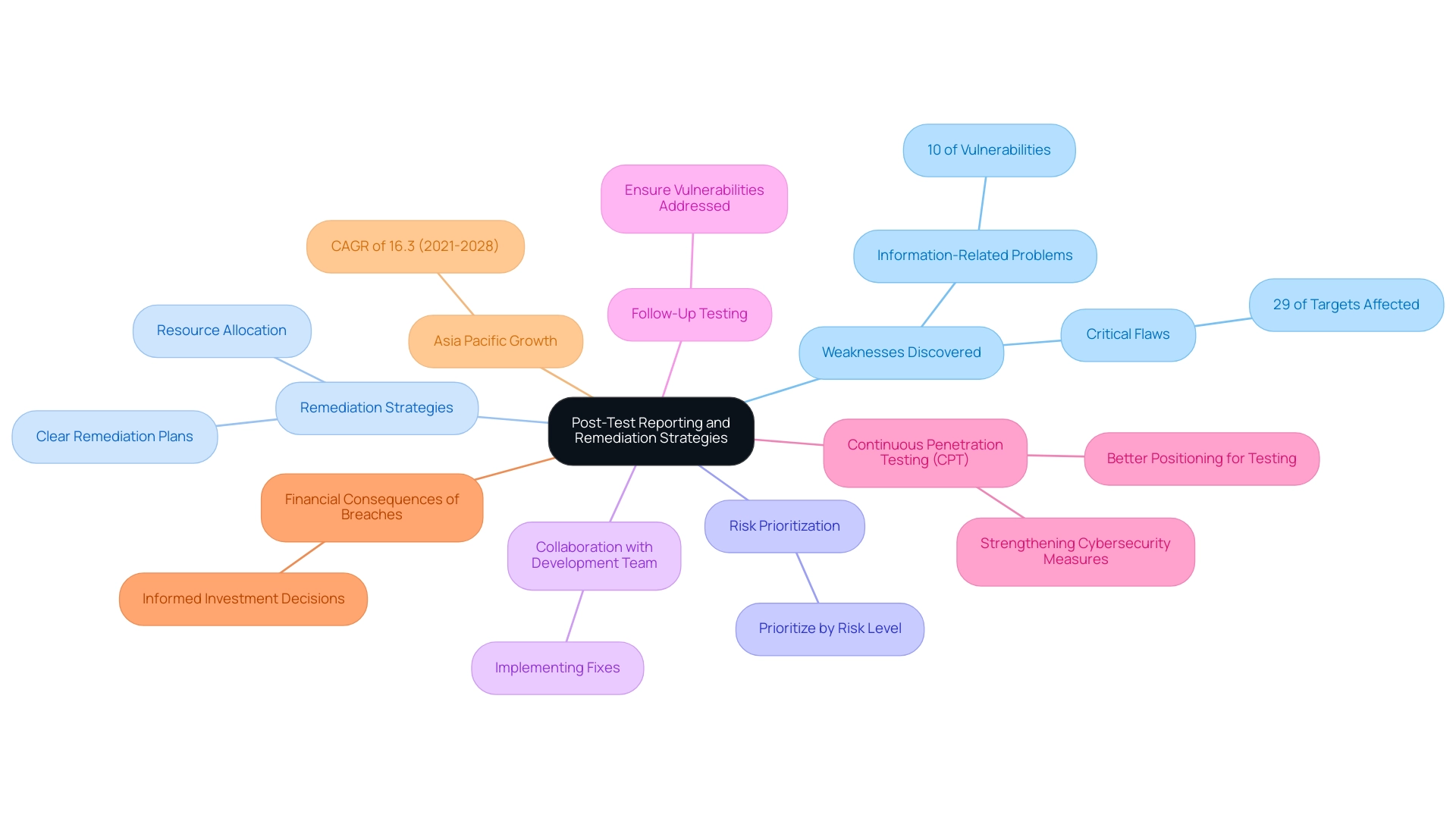
After a security assessment, it is essential to create an extensive report that outlines the weaknesses discovered, the techniques used to exploit them, and their possible effect on the organization. In 2020, it was reported that 29% of penetration test targets had at least one critical flaw, and notably, 10% of issues found were information-related problems. This underscores the necessity for thorough documentation and analysis.
Each weakness should be paired with clear remediation strategies, prioritized by risk level to facilitate effective resource allocation. Collaboration with your development team is essential for implementing these fixes, and conducting follow-up tests is vital to ensure that vulnerabilities have been adequately addressed. Recent trends indicate that organizations adopting continuous penetration testing (CPT) are better positioned for testing web applications for vulnerabilities, which is crucial for maintaining a robust defensive posture for their e-commerce applications.
As the Asia Pacific region anticipates a compound annual growth rate (CAGR) of 16.3% from 2021 to 2028, the urgency of adapting protective practices in light of this growth cannot be overstated. By understanding the financial consequences of breaches, organizations can make informed decisions regarding investments in new protective tools and protocols. A case study titled 'Mitigating Risks with Continuous Penetration Testing' illustrates how testing web applications for vulnerabilities helps organizations identify and prioritize security risks, enabling better resource allocation and strengthening cybersecurity measures.
Conclusion
Web application penetration testing is not just a necessary practice; it is a critical component of an organization's overall cybersecurity strategy. By simulating potential cyber attacks, businesses can uncover vulnerabilities that may otherwise remain hidden, allowing them to take proactive measures to protect sensitive data and maintain customer trust. The alarming statistics surrounding web application vulnerabilities, particularly in widely used platforms like WordPress, highlight the urgent need for regular security assessments.
Preparation is key to successful penetration testing. Establishing a clear scope, engaging stakeholders, and utilizing the right tools and methodologies are fundamental steps that lead to effective outcomes. Understanding common vulnerabilities such as SQL Injection and Cross-Site Scripting equips organizations to better defend against these prevalent threats. The incorporation of advanced tools like OWASP ZAP and Burp Suite further enhances the testing process, ensuring comprehensive coverage and robust security measures.
Post-test reporting and remediation strategies are equally important. Thorough documentation, collaboration with development teams, and the implementation of follow-up tests are vital for addressing identified vulnerabilities. As organizations face an ever-evolving landscape of cyber threats, adopting continuous penetration testing practices can significantly bolster their defenses, enabling them to stay ahead of potential risks.
In summary, investing in web application penetration testing is essential for any organization that values its security posture. By prioritizing regular assessments, utilizing effective tools, and implementing robust remediation strategies, businesses can not only protect their data but also reinforce the trust of their customers. As cyber threats continue to grow in sophistication, proactive measures in web application security are no longer optional; they are imperative for long-term success.





