Introduction
In the digital age, where online interactions are integral to personal and professional life, browser extensions have emerged as powerful tools that enhance the web browsing experience. These lightweight software programs offer a myriad of functionalities—from ad blocking to password management—allowing users to customize their online activities.
However, as the popularity of these extensions grows, so does the complexity of managing them safely. With statistics revealing that a significant portion of data breaches involves authenticated users, understanding the risks associated with browser extensions is crucial.
This article delves into the multifaceted world of browser extensions, exploring their benefits, the security challenges they present, and best practices for effective management, ensuring that users can navigate this landscape with confidence and security.
Understanding Browser Extensions: Definition and Purpose
Web add-ons are lightweight software applications created to enhance the capabilities of internet navigators, enabling individuals to customize their surfing experience. These add-ons can introduce a variety of features, including:
- Ad blocking
- Password management
- Productivity tools
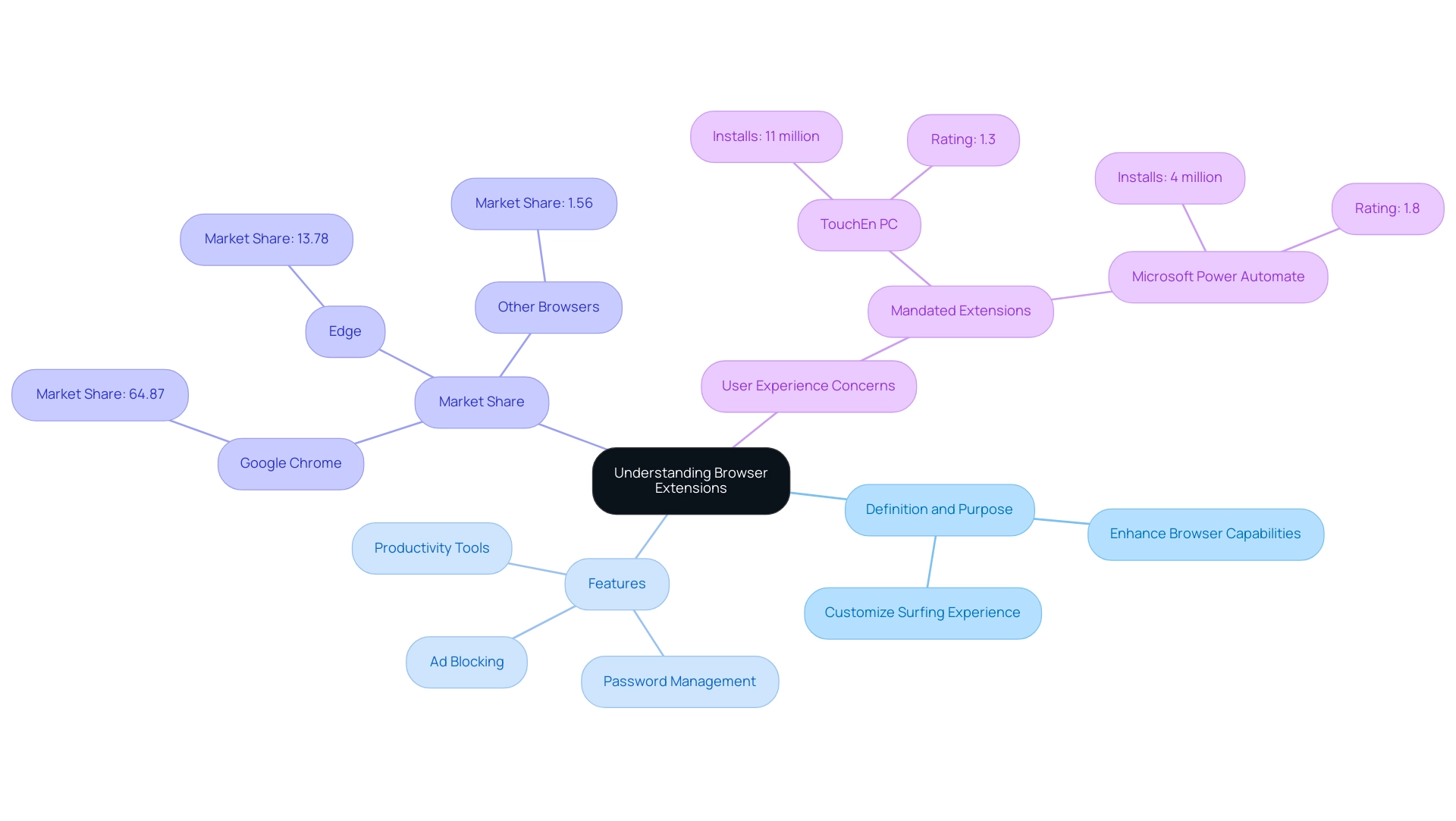
Ultimately enhancing both efficiency and engagement. As of 2024, the landscape of browser add-ons is evolving, with statistics indicating that Google Chrome continues to dominate the global desktop browser market, holding a remarkable 64.87% share, while Edge holds 13.78% and other browsers collectively account for just 1.56%.
This popularity highlights the importance and usefulness of add-ons among individuals. However, it's essential to recognize that while these tools provide considerable advantages, such as enhanced productivity and streamlined workflows, they can also introduce vulnerabilities if we do not manage browser extensions with care. For example, case studies show that additions required by organizations, such as TouchEn PC and Microsoft Power Automate, have high installation counts but low ratings from individuals, suggesting possible concerns with experience.
Naveen Kumar, a data and statistical expert at DemandSage, emphasizes the importance of understanding these tools, stating that insights into emerging technologies are essential for effective data-driven decision-making. Furthermore, a detailed analysis of recent advancements in browser add-on safety uncovers continuous initiatives to improve individual protection, emphasizing the necessity for alertness among individuals and developers equally.
Identifying Risks: The Threat Landscape of Browser Extensions
Browser add-ons present significant security challenges, including data breaches, malware infections, and privacy violations. Alarmingly, statistics indicate that 30% of data breaches involve authenticated individuals, which underscores the critical need for vigilance among individuals. Numerous add-ons request permissions that go beyond their primary functionality, unintentionally exposing sensitive information.
For instance, the Android/LokiBot malware targeted over 100 financial institutions, generating nearly $2 million in revenue by exploiting such vulnerabilities. This emphasizes the importance for individuals to carefully inspect the permissions requested by add-ons and to assess reviews prior to installation. As the environment of online add-ons continues to develop, comprehending these risks enables users to adopt a proactive approach to manage browser extensions and their digital resources.
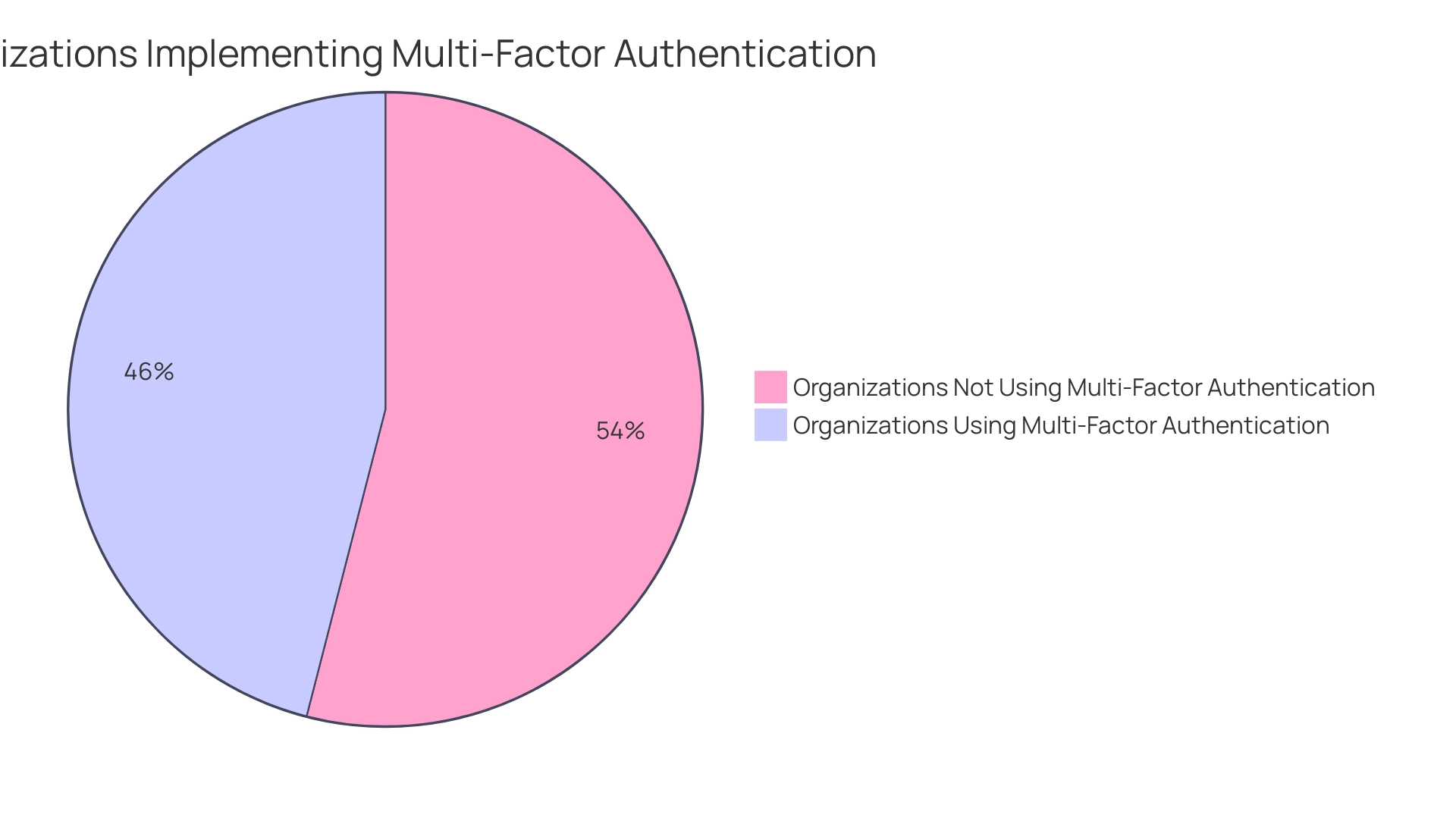
With 46% of organizations implementing multi-factor authentication for securing remote access, it’s evident that strong protective measures are essential in safeguarding against potential threats. Moreover, the cloud security software market, which attained a size of $29 billion in 2020, highlights the increasing economic consequences of security threats associated with plug-ins. As we encounter a rise in cyber dangers from web add-ons, a careful and knowledgeable strategy is essential.
Best Practices for Safe and Effective Extension Management
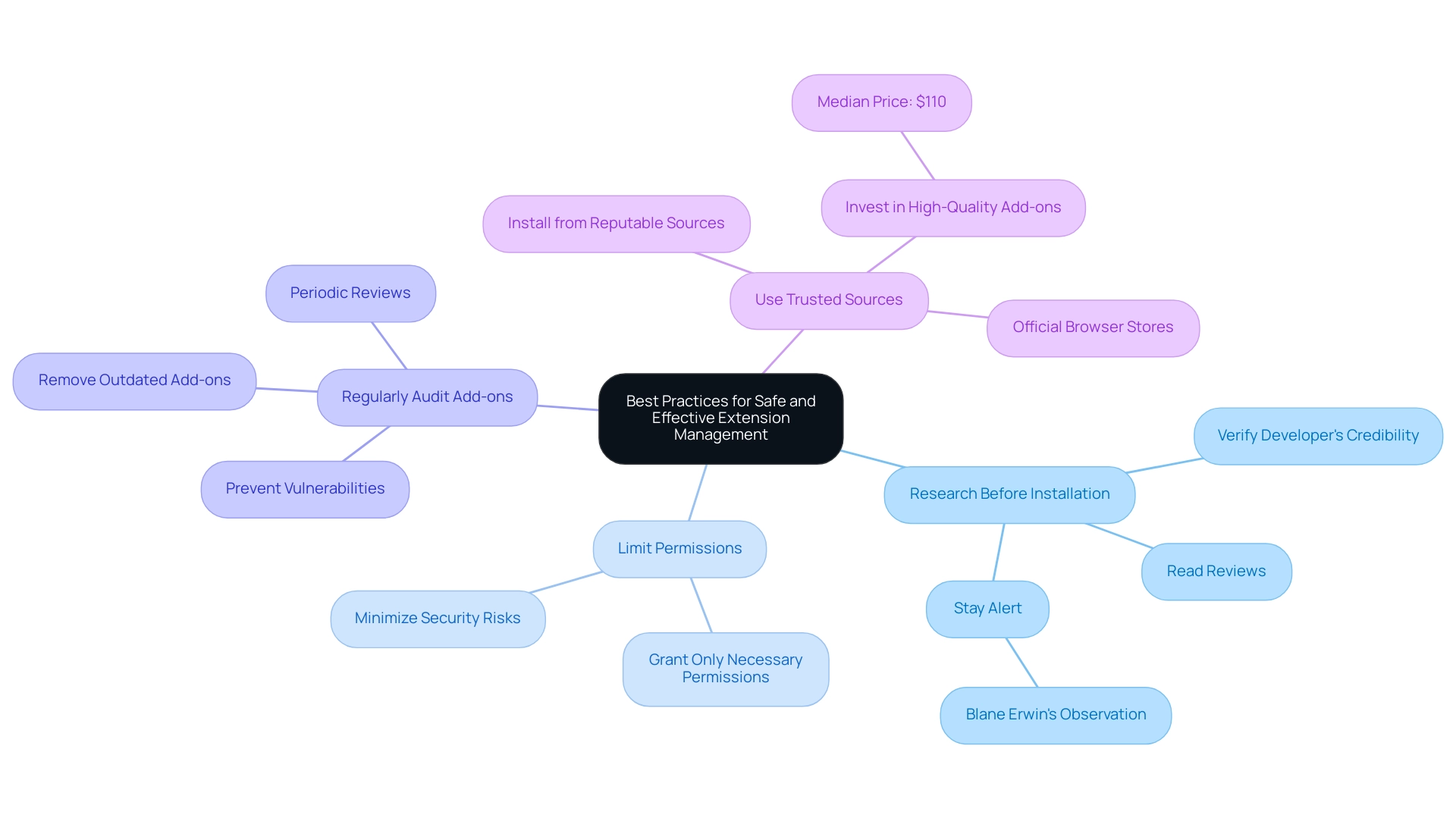
Efficiently managing browser extensions is vital for preserving online safety and improving the experience, particularly in collaborative settings. Here are essential best practices to consider:
-
Research Before Installation:
Prioritize thorough research by reading reviews and verifying the developer's credibility. Understanding their reputation can reduce risks associated with harmful add-ons. As Blane Erwin observes,Microsoft appears to be adopting the same hands-off strategy to management as Chrome,
emphasizing the need for users to stay alert. -
Limit Permissions:
Be judicious with the permissions you grant; only provide what is absolutely necessary for the application to function effectively. This minimizes exposure to potential security risks. -
Regularly Audit Add-ons:
Conduct periodic reviews of your installed add-ons, removing those that are outdated or unnecessary. This proactive approach can prevent vulnerabilities from remaining add-ons. -
Use Trusted Sources:
Always install add-ons from reputable sources, such as official browser stores. This significantly reduces the risk of encountering harmful software. With the median price in the News & Weather category hitting $110, investing in high-quality, secure add-ons is essential.
Moreover, with at least 1.69 billion installs for Chrome add-ons, the significance of how to manage browser extensions effectively cannot be overstated. Groups should collaborate to exchange insights and strategies, ensuring that everyone is aware of best practices to manage browser extensions effectively. By following these best practices and utilizing the insights from the case study on Chrome add-on development, teams can significantly improve their online safety and optimize their use of web tools.
Step-by-Step Guide to Managing Browser Extensions
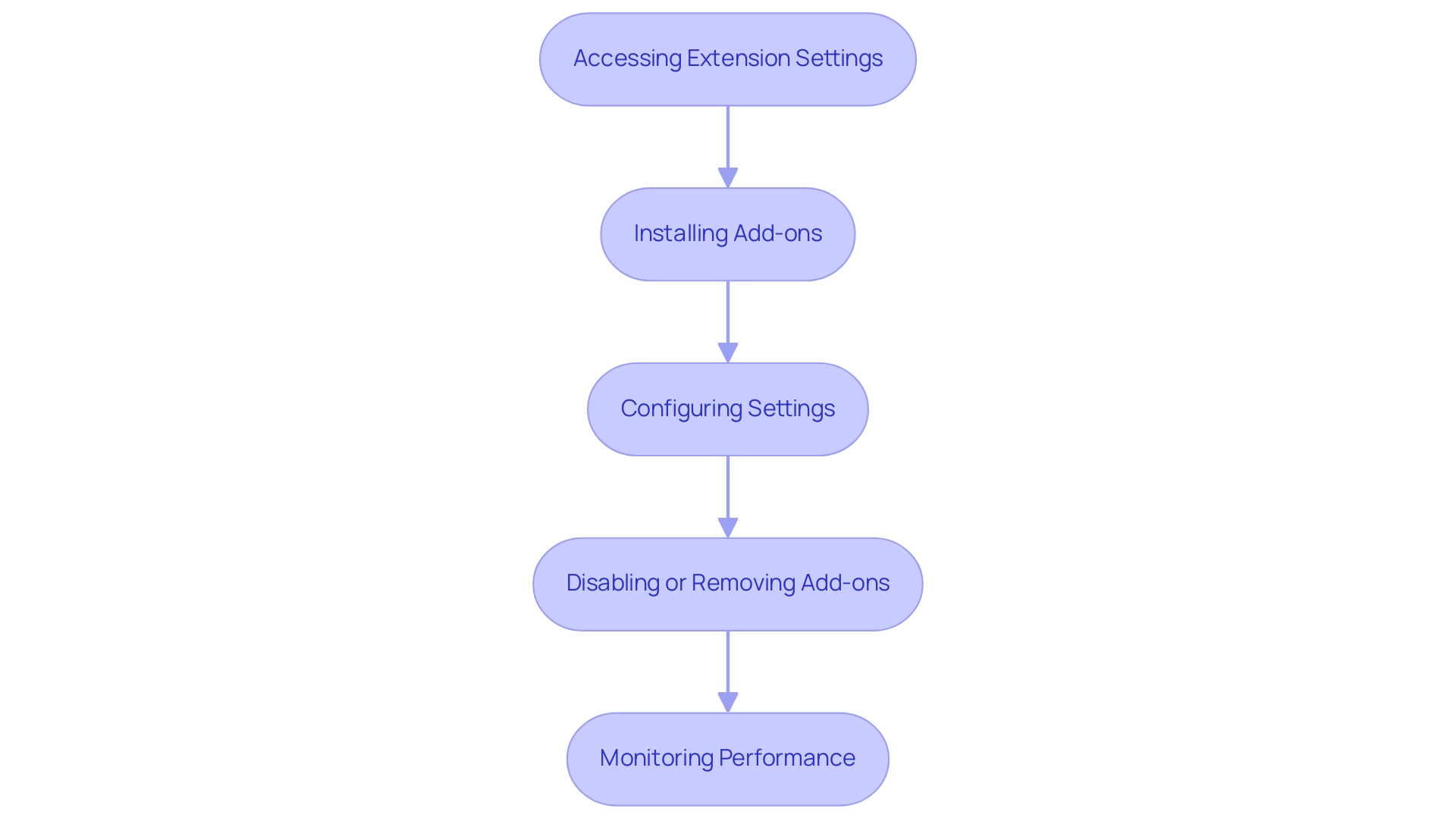
Efficiently managing browser extensions is essential for enhancing your e-commerce experience. Here’s a step-by-step guide to help you navigate the process:
-
Accessing Extension Settings:
Begin by launching your web application and locating the settings menu.
Look for the 'Add-ons' section to manage browser extensions and your installed tools. -
Installing Add-ons:
To add a new add-on, search for it in your browser’s store, click 'Add to Browser', and follow the installation prompts to integrate it seamlessly. -
Configuring Settings:
After installation, click on the icon to access its settings. Here, you can adjust permissions, preferences, and configurations to tailor functionality to your needs.
As Allisa Boulette wisely notes,Productivity is deeply personal, so ensure you discover the tools that suit you—not for me.
-
Disabling or Removing Add-ons:
If you choose to temporarily deactivate an add-on, simply toggle it off in the settings.
To remove it completely, click 'Remove' next to the add-on name. -
Monitoring Performance:
Regularly observe your browser’s performance; disable add-ons that may be causing slowdowns or conflicts.
Additionally, stay proactive by checking for updates to ensure optimal functionality.
For example, the Merlin add-on demonstrates effective application of visual hierarchy and whitespace, improving interaction without overcrowding. This considerate design can significantly enhance your productivity as you handle your selected tools.
Furthermore, consider using Todoist, which is lightweight and easy to use, but keep in mind it requires sign-up and has a limited free plan.
Remember, when you manage browser extensions, it is important that pop-ups typically restrict their dimensions to 600x800px to prevent interrupting your workflow, as this can improve experience and sustain concentration.
Maintaining Security: The Importance of Updates and Monitoring
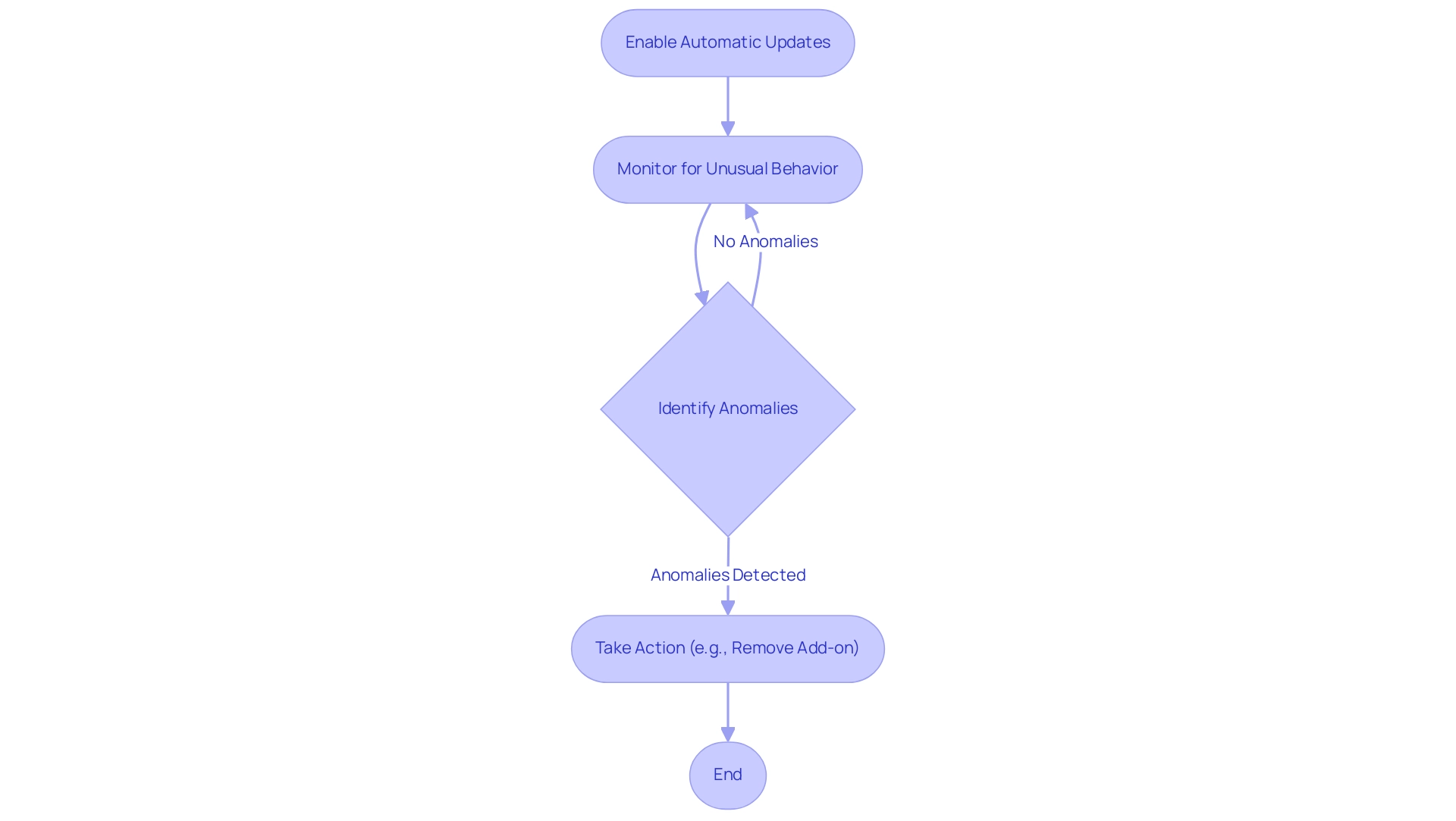
To manage browser extensions effectively, maintaining their security and functionality hinges on regular updates and vigilant monitoring. With the ever-evolving threat landscape, developers routinely issue updates not only to patch vulnerabilities but also to enhance performance. Significantly, a report shows that 31.25% of add-ons created by Google have exceeded 1 million users, highlighting the extent to which monitoring must take place.
Additionally, popular add-ons like Adblock for YouTube™ boast an impressive 10,000,000 downloads, highlighting the potential risks associated with widely used tools. To facilitate this, you can manage browser extensions by enabling automatic updates in your browser settings, ensuring that you benefit from the latest security patches without having to manually intervene. Furthermore, to manage browser extensions effectively, keep an eye on your add-ons for any unusual behavior—signs such as unexpected requests for permissions or noticeable performance issues warrant immediate attention.
If any anomalies occur, consider removing the add-on to safeguard your data. For instance, the VPN add-on highlighted in a recent case study achieved only 207 downloads, illustrating that even less popular tools demand diligent oversight. Reference to experiences shared using RAPL for power measurements further emphasizes the technical aspects of monitoring and managing these extensions.
By remaining proactive, you not only protect your data but also enhance your overall browsing experience.
Conclusion
In the intricate landscape of browser extensions, understanding both their advantages and potential risks is paramount. These tools significantly enhance the browsing experience by offering functionalities such as ad blocking, password management, and productivity enhancements. However, as their usage expands, so do the security challenges they pose. With data breaches often involving authenticated users, it is clear that vigilance and informed decision-making are essential to navigate this digital terrain safely.
Implementing best practices for managing browser extensions can greatly mitigate risks. Conducting thorough research before installation, limiting permissions, and regularly auditing installed extensions are critical steps that users should adopt. Utilizing trusted sources for downloads further ensures that security is prioritized, safeguarding sensitive information from potential threats. By following these guidelines, users can enjoy the benefits of browser extensions while minimizing vulnerabilities.
Ultimately, staying proactive about updates and monitoring extension behavior is crucial in maintaining both security and functionality. As the digital environment evolves, so too must the strategies employed by users to protect themselves. Through careful management and ongoing vigilance, individuals can confidently harness the power of browser extensions, enhancing their online experience without compromising their security.





