Introduction
The immersion of IoT technologies in e-commerce is transforming operations, yet it brings forth pressing security concerns. The vast array of connected devices expands the potential for cyber-attacks, creating a broad attack surface that's challenging to secure. Each device's unique vulnerabilities necessitate tailored security measures, adding layers of complexity to cybersecurity strategies.
Furthermore, the real-time processing required by IoT systems in e-commerce means that any delay in addressing security threats can escalate into substantial financial and reputational repercussions. Compounding the issue, many IoT devices lack robust built-in security, often released with outdated protocols, making them prime targets for cybercriminals. This absence of standardization across the diverse IoT ecosystem exacerbates the risk, leaving systems vulnerable to data interception and tampering.
As IoT devices proliferate, from seemingly innocuous "smart" toothbrushes to critical infrastructure sensors, the implications for privacy, security, and national stability are profound. The consequences of IoT security breaches are far-reaching, potentially leading to sensitive data loss, unauthorized system access, or even disruption of critical services. Such incidents not only entail legal and regulatory ramifications but also erode customer trust and tarnish a company's reputation, with a direct impact on the bottom line.
Taking proactive security measures is paramount for organizations to shield themselves from these risks and maintain their market position. In light of these developments, it's clear that IoT security is not just a technical issue but a strategic imperative for businesses. As IoT continues to shape the digital landscape, the necessity for vigilant and adaptive security measures becomes increasingly vital to safeguard the future of e-commerce operations.
Challenges in IoT Security for E-commerce Operations
The immersion of IoT technologies in e-commerce is transforming operations, yet it brings forth pressing security concerns. The vast array of connected devices expands the potential for cyber-attacks, creating a broad attack surface that's challenging to secure.
Each device's unique vulnerabilities necessitate tailored security measures, adding layers of complexity to cybersecurity strategies. Furthermore, the real-time processing required by IoT systems in e-commerce means that any delay in addressing security threats can escalate into substantial financial and reputational repercussions.
Compounding the issue, many IoT devices lack robust built-in security, often released with outdated protocols, making them prime targets for cybercriminals. This absence of standardization across the diverse IoT ecosystem exacerbates the risk, leaving systems vulnerable to data interception and tampering.
As IoT devices proliferate, from seemingly innocuous "smart" toothbrushes to critical infrastructure sensors, the implications for privacy, security, and national stability are profound. Cybersecurity experts like Stefan Zuger of Fortinet Switzerland emphasize the urgency of protecting every Internet-connected device to prevent exploitation.
The consequences of IoT security breaches are far-reaching, potentially leading to sensitive data loss, unauthorized system access, or even disruption of critical services. Such incidents not only entail legal and regulatory ramifications but also erode customer trust and tarnish a company's reputation, with a direct impact on the bottom line.
Taking proactive security measures is paramount for organizations to shield themselves from these risks and maintain their market position. The industrial sector is responding to these challenges, as evidenced by Honeywell's acquisition of Scadafence, a cybersecurity firm specializing in safeguarding interconnected devices. This move underscores the critical nature of protecting operational technology (OT) assets beyond individual smart homes. With the growing imperative for IoT security, companies must disclose their preventive strategies, as mandated by new regulatory requirements, ensuring transparency and accountability in their IoT deployments. In light of these developments, it's clear that IoT security is not just a technical issue but a strategic imperative for businesses. As It continues to shape the digital landscape, the necessity for vigilant and adaptive security measures becomes increasingly vital to safeguard the future of e-commerce operations.
Importance of IoT Security in E-commerce
With the proliferation of the Internet of Things (IoT) in e-commerce, the security of connected devices has become a critical issue. E-commerce platforms are repositories of a wealth of personal and financial data, necessitating a robust security framework to protect against breaches that could lead to identity theft, fraud, and a significant erosion of customer trust.
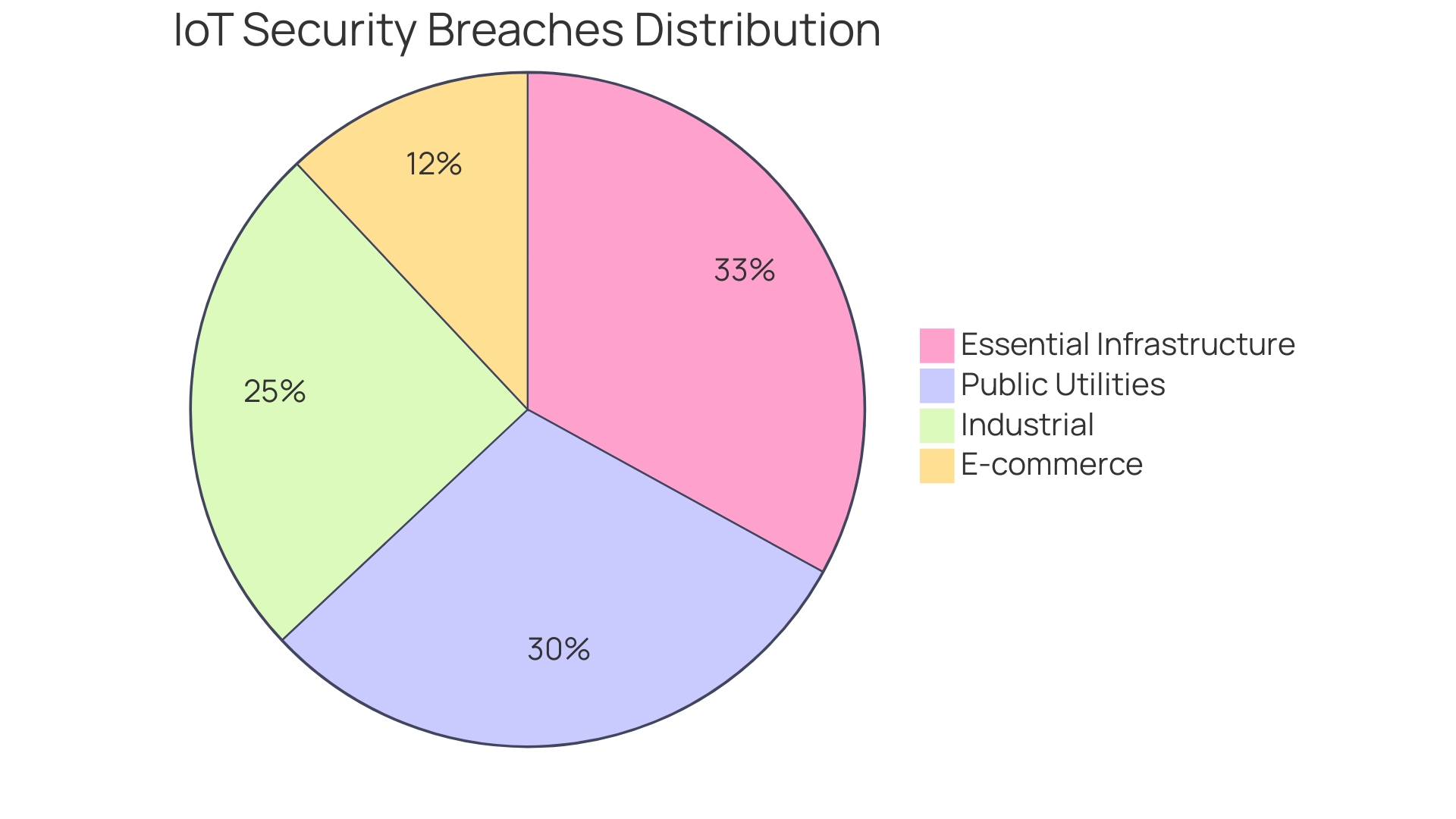
The interconnectedness of IoT devices means that a single vulnerability can be exploited across multiple devices, posing a substantial risk to both personal and infrastructural integrity. For instance, the recent acquisition of Scadafence by Honeywell underscores the gravity of securing large networks of connected devices, particularly those in public utilities and industrial sectors.
Similarly, the Port of Nagoya's encounter with Russian hackers highlights the vulnerability of older systems and the need for enhanced security measures in essential infrastructure. The utilization of platforms like AWS IoT, which provides secure and encrypted connections, is a testament to the industry's efforts in safeguarding data integrity.
Additionally, tools such as Splunk's Enterprise Security and SOAR facilitate the monitoring and rapid response to any anomalies in device behavior, bolstering the overall security posture. According to IBM's 2023 Threat Intelligence Index, although defenders are improving in thwarting ransomware attacks, breaches detected internally result in significantly lower costs and shorter life cycles than those disclosed by attackers or third parties. This emphasizes the value of investment in internal threat detection mechanisms. Furthermore, the financial implications are stark; the average cost of data breaches has soared to $4.45 million in 2023, marking a 15% increase in the past three years. This statistic alone should spur e-commerce directors to prioritize IoT security, not just to protect against immediate threats but as a long-term investment in their brand's reputation and customer loyalty.
Existing Solutions and Technologies for IoT Security
In the rapidly evolving landscape of IoT in e-commerce, securing connected devices is paramount. Robust authentication and access control mechanisms are fundamental, ensuring that only authorized entities engage with the network.
Encryption is pivotal, safeguarding data confidentiality and integrity during transmission. Consider AWS IoT's encryption capabilities, which protect data for devices like the Tamagotchi Uni, allowing secure global interactions for millions of users.
Network segmentation and firewalls serve as a bulwark, isolating IoT devices to mitigate risks in the event of a security breach. This is critical for operations like Bemol, a Brazilian retail giant, where a reliable network is essential due to its vast geographical spread and logistical complexities.
Intrusion detection and prevention systems are the watchful eyes over network traffic, spotting potential threats. This vigilance is underscored by Honeywell's acquisition of Scadafence, highlighting the importance of securing large-scale networks with IoT devices.
Moreover, the integrity of IoT infrastructure cannot be overstated. Regular software updates and patch management are indispensable for maintaining security. The recent vulnerabilities uncovered, with one rated as critical (9.8/10), emphasize the necessity of staying ahead of potential threats through diligent maintenance and updates. The sheer volume of It transactions within manufacturing and retail, accounting for over 50% of total transactions, underscores the critical role It plays in these sectors. It is a testament to the importance of securing these devices, as echoed by Stefan Auerbach, CEO of Utimaco, who advocates for enhanced public trust through superior cybersecurity solutions.
Case Study: Enhancing Application Security and Efficiency in E-commerce with IoT
In the dynamic landscape of e-commerce, the integration of IoT technologies has become a game-changer, particularly in warehouse and supply chain management. A case study highlights how an e-commerce company harnessed IoT-enabled sensors and devices to revolutionize its operations. These tools provided invaluable real-time data, allowing for meticulous monitoring and tracking of inventory, shipments, and equipment.
The secure connection of these devices to the e-commerce platform was achieved through stringent authentication and encryption protocols, ensuring data integrity and security. The result was a notable surge in inventory accuracy and a more seamless order fulfillment process, culminating in heightened operational efficiency. Furthermore, the enhanced visibility into the supply chain not only fortified security but also minimized errors and delays.
This strategic move significantly propelled customer satisfaction, underscoring the transformative potential of IoT in e-commerce. The broader implications of IoT in smart retail are vast, ranging from improved security measures that deter theft and accidents to personalized shopping experiences that captivate consumers. Yet, retailers must navigate the complexities of data security and privacy, balancing the benefits of customer behavior analytics with responsible data stewardship.
The financial aspect of IoT implementation, especially for smaller retailers, demands a thorough cost-benefit analysis to ensure a profitable return on investment. Moreover, the increasing number of connected devices worldwide introduces heightened risks of cyber threats, making robust security measures non-negotiable. As It continues to permeate the retail industry, it promises a future of seamless integration between technology and consumer interaction, driving sustainability, satisfaction, and efficiency to new heights.
Best Practices for Ensuring IoT Security in E-commerce
The rapid expansion of IoT devices in e-commerce operations brings significant benefits but also introduces critical security concerns. A proactive approach to IoT security is not just a technical necessity; it's pivotal to maintaining customer trust and the company's reputation.
Conducting a detailed risk assessment is the first step in understanding and mitigating potential threats. This process should be informed by real-world incident reports and the potential severity of vulnerabilities, as highlighted by the NIST Cybersecurity Framework and the CVSS scores.
For robust protection, multi-factor authentication is indispensable, ensuring that access to IoT devices and networks is tightly controlled. Regular updates and patches are equally crucial, as they address vulnerabilities that could be exploited by cybercriminals.
Network segmentation is a strategic defense, isolating critical systems to contain any damage from security breaches. The importance of continuous monitoring cannot be overstated.
Platforms like Splunk provide powerful tools for real-time analysis and automated responses to security incidents, which can be vital in maintaining a secure IoT environment. The acquisition of Scadafence by Honeywell underscores the industry's commitment to securing large-scale IoT networks, further stressing the need for vigilance in cybersecurity. Lastly, fostering a culture of security within the organization through employee training is fundamental. As IoT devices permeate our daily lives, everyone from the boardroom to the server room must understand the potential risks and the measures required to mitigate them. By implementing these best practices, businesses can build a secure foundation for their e-commerce operations, leveraging IoT technology while safeguarding against cyber threats.
Future Directions and Opportunities for IoT Security in E-commerce
The integration of IoT in e-commerce is transforming the landscape of online transactions, offering both convenience and enhanced security. Imagine the simplicity of purchasing your morning coffee with a tap of your smartwatch—this is the reality of IoT payments.
The inclusion of NFC chips in internet-connected devices eliminates the need for traditional payment methods, streamlining the process and reducing the risk of fraud through encrypted transactions. With billions of devices connected globally, the potential for IoT is immense, but so is the vulnerability to cyber threats.
Data privacy and protection are paramount as these devices handle an array of sensitive information. To safeguard this data, the adoption of machine learning models is crucial for threat detection and response.
In fact, research utilizing the NSL-KDD dataset has shown that machine learning can significantly enhance threat detection accuracy. Moreover, blockchain technology is emerging as a robust solution to secure IoT transactions without third-party interference, addressing the risks of data alteration and single points of failure. As we forge ahead, the collaboration between industry experts and regulatory bodies is vital to establish standardized security measures. The recent initiative by NIST to oversee cybersecurity qualifications for consumer-grade routers and the acquisition of Scadafence by Honeywell underscore the importance of securing the IoT ecosystem. These advancements promise a future where e-commerce operations can leverage IoT with confidence, ensuring both the integrity of transactions and the protection of consumers.
Conclusion
In conclusion, the immersion of IoT technologies in e-commerce has brought about significant transformations, but it has also raised pressing security concerns. The vast array of connected devices expands the potential for cyber-attacks, necessitating tailored security measures.
IoT security breaches can lead to data loss, unauthorized access, and damage to a company's reputation. To address these risks, organizations must take proactive security measures such as authentication, encryption, network segmentation, and intrusion detection.
Regular updates and patch management are crucial. IoT security is not just a technical issue but a strategic imperative for businesses.
The adoption of machine learning and blockchain technology enhances threat detection accuracy and secures transactions. Collaboration between industry experts and regulatory bodies is vital to establish standardized security measures. In conclusion, ensuring IoT security in e-commerce requires a proactive approach with risk assessment, multi-factor authentication, regular updates, network segmentation, continuous monitoring, employee training on cybersecurity best practices, machine learning models for threat detection, and blockchain technology. By implementing these practices, businesses can build a secure foundation for their e-commerce operations while leveraging the transformative power of IoT technology.





