Introduction
The integration of the Industrial Internet of Things (IIoT) in the manufacturing sector brings about advanced data analytics and interconnected machinery, revolutionizing operational efficiency and Key Performance Indicators (KPIs). However, this technological leap forward is not without its challenges.
IIoT architectures, with their vast web of devices and sensors, can inadvertently become a playground for cybercriminals. Additionally, the extensive data generated by IoT devices raises pressing concerns about data privacy and the methods of collection, usage, and oversight. In this article, we will explore the security challenges faced by IIoT and discuss strategies to address them, with a focus on device vulnerabilities, network vulnerabilities, and the importance of encryption and authentication mechanisms.
Understanding IIoT Security Challenges
In the realm of Industry 4.0, the integration of the Industrial Internet of Things (IIoT) stands as a beacon of modernization, transforming the manufacturing sector with advanced data analytics and interconnected machinery. As manufacturers strive to integrate various data sources to enhance operational efficiency and reduce costs, IIoT emerges as a key player in achieving higher Overall Equipment Effectiveness (OEE) and improving Key Performance Indicators (KPIs).
Yet, this technological leap forward is not without its challenges. The vast web of devices and sensors that characterizes IIoT architectures, especially those with substantial on-premises components such as PLCs and tethered connectivity, can inadvertently become a playground for cybercriminals.
This vulnerability is compounded by data privacy concerns, as IoT devices generate extensive data, often personal in nature. The sheer scale of data collection raises pressing questions about the methods of collection, usage, and oversight, leaving users in a complex privacy landscape where consent mechanisms are frequently inadequate. As such, navigating the IIoT space requires a careful balance between leveraging its potential for efficiency gains and addressing the principled challenges posed by data privacy and cybersecurity threats.
Device Vulnerabilities
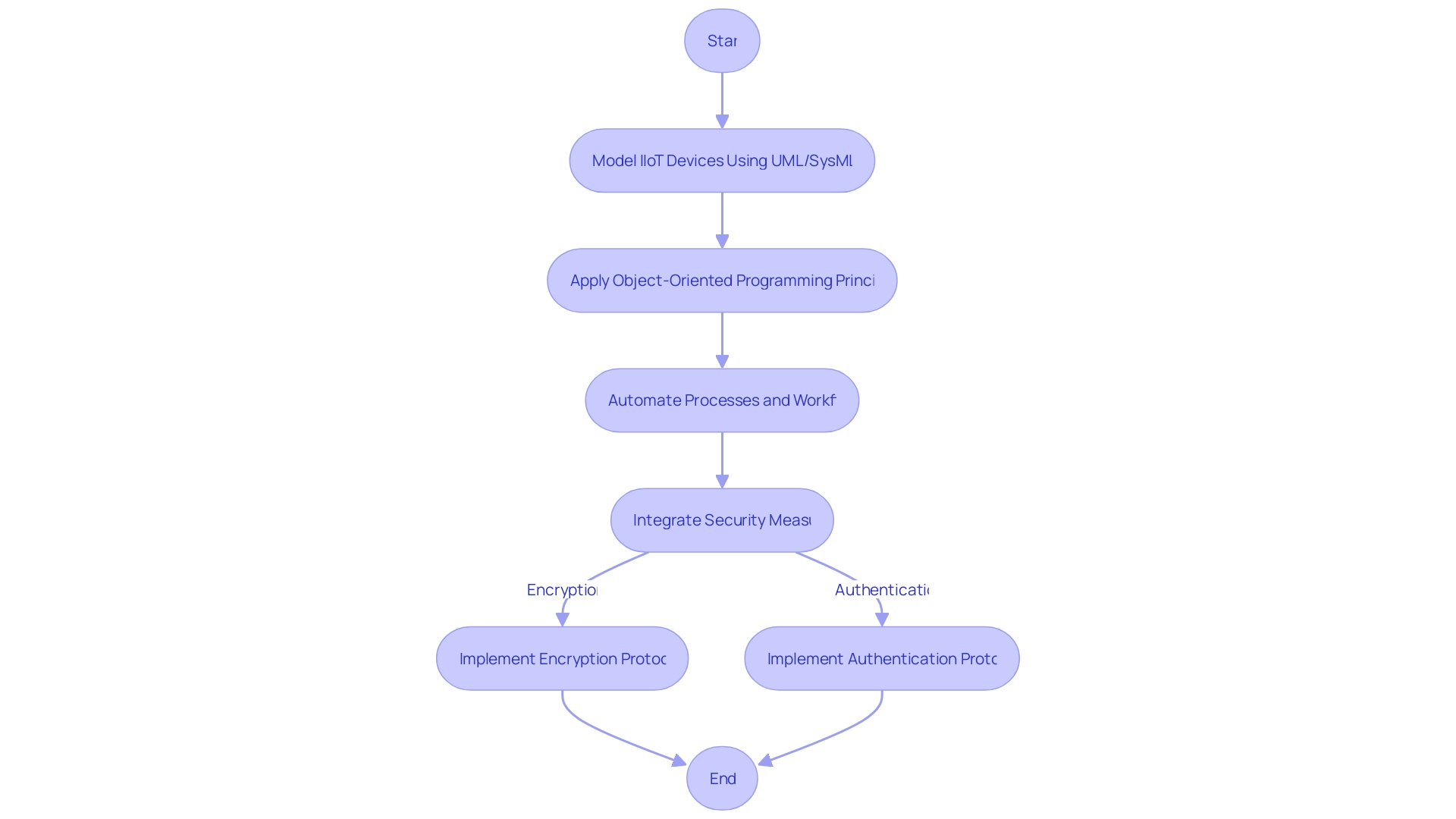
The integration of model-based techniques, such as the Unified Modeling Language (UML) and Systems Modeling Language (SysML), is revolutionizing the way Industrial Internet of Things (IIoT) devices are engineered. Traditionally, IIoT devices have been constrained by limited processing capabilities and memory, posing significant security risks.
However, by adopting object-oriented programming paradigms, which have long been heralded as a panacea for enhancing software quality and reusability in computer science, the resilience of these devices is being fortified. As noted by Mili et al., object orientation is regarded as a key to surmounting a host of software engineering challenges, and its principles are now being applied to automate and control engineering to mitigate vulnerabilities. The future of IIoT device programming is poised to leverage these advanced modeling techniques, ensuring that robust security measures, including sophisticated encryption and authentication protocols, are embedded into the very fabric of IIoT solutions.
Network Vulnerabilities
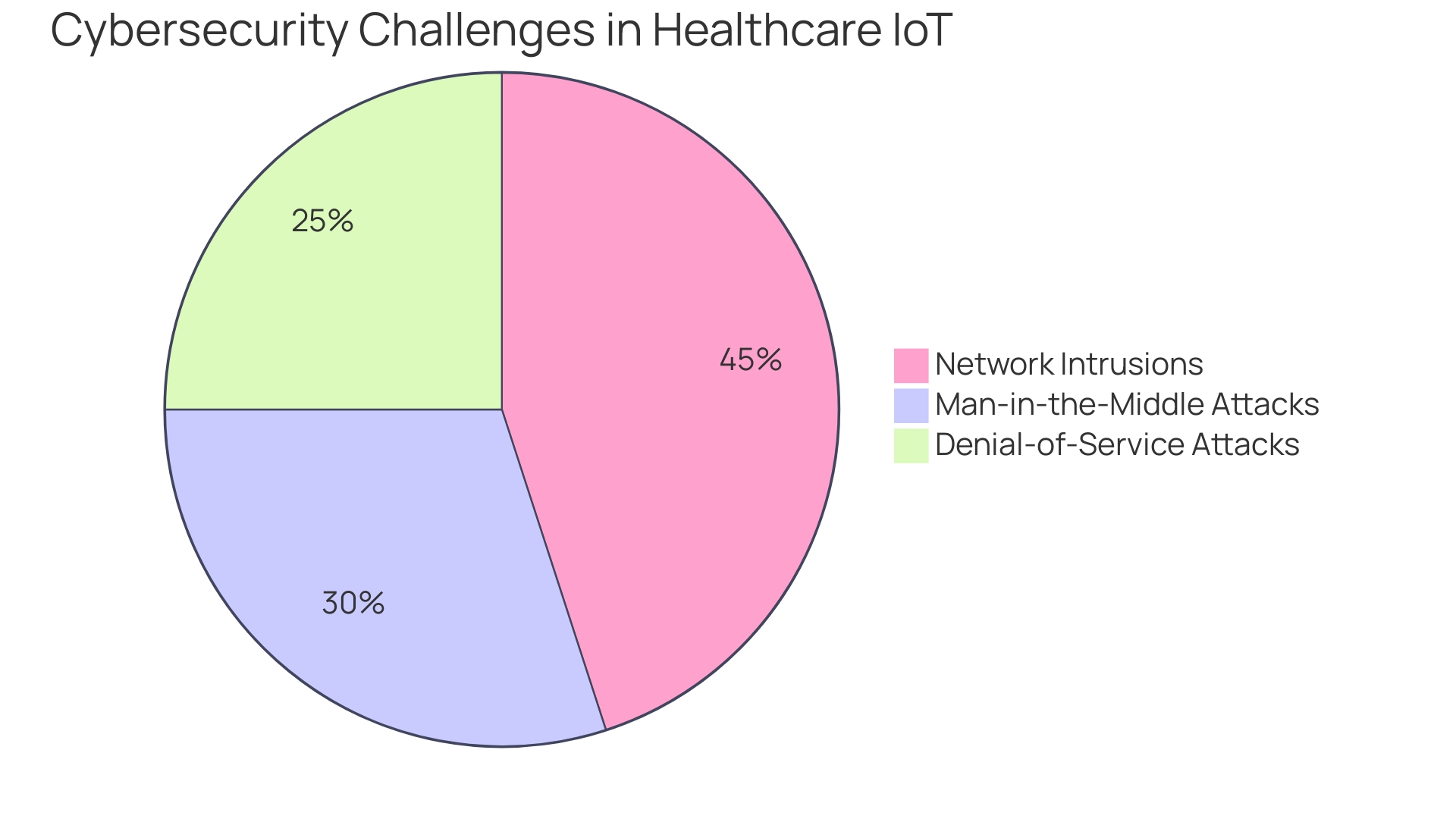
IoT devices have become integral in modernizing diverse sectors, including healthcare, where they significantly boost patient care and operational efficiency. However, the expansion of IoT also presents notable cybersecurity challenges. The healthcare industry, which generates a staggering 30 percent of the world's data, has seen a surge in security breaches coinciding with the adoption of IoT technologies.
These breaches are concerning, particularly because the data involved is often extremely sensitive. Networks within IoT frameworks are vulnerable to a range of cyber attacks, such as man-in-the-middle, denial-of-service, and network intrusions. Such attacks can lead to severe consequences, including unauthorized data access, data tampering, and operational disruptions, underlining the critical need for robust cybersecurity measures in IoT implementations.
Enhancing IIoT Security
Enhancing the security of IIoT operations is a multifaceted endeavor, requiring a strategic blend of human expertise and advanced technologies. Reflecting on industry leaders like Siemens' Electronics Factory Erlangen, we see the profound impact of digitalization.
Here, the convergence of IT and operational technology (OT), alongside the adoption of AI and digital twins, has led to a robust and sustainable Digital Enterprise ecosystem. This holistic approach not only bolsters productivity and quality but is also instrumental in fortifying security measures.
As we embrace November 2023, the technological landscape is abuzz with themes of operational resilience and digital enablement. For those at the helm of IT and operations, the lesson is clear: integrating innovative solutions and fostering industry cohesion are key to advancing not just the security but the overall operational capabilities of their IIoT systems. The Electronics Factory Erlangen serves as a testament to the power of digitalization, where the human element is as crucial as the technology in driving forward a secure and innovative manufacturing paradigm.
Encryption and Authentication
Implementing strong encryption and authentication mechanisms is essential to protect IoT devices and data. This includes using secure protocols, such as Transport Layer Security (TLS), and ensuring that devices are authenticated before accessing the network.
Conclusion
The integration of IIoT in manufacturing revolutionizes operational efficiency but comes with security challenges. Device vulnerabilities can be addressed by adopting advanced modeling techniques and embedding robust security measures. Network vulnerabilities require robust cybersecurity measures to mitigate risks.
Enhancing IIoT security requires a multifaceted approach, combining expertise and advanced technologies. Implementing strong encryption and authentication mechanisms is essential to protect IIoT devices and data. Overall, addressing these challenges allows manufacturers to embrace the potential of IIoT while safeguarding their operations from cyber threats.





