Introduction
In an increasingly interconnected world, the security of web applications has emerged as a critical concern for organizations of all sizes. As businesses pivot to online platforms for e-commerce and data management, they face a growing array of cyber threats that can jeopardize sensitive information and financial stability.
The staggering projection of $10.5 trillion in global cybercrime costs by 2025 underscores the urgent need for robust security measures. This article delves into the complexities of web application security, exploring:
- Common vulnerabilities
- Best practices for safeguarding applications
- The essential role of security assessments and user education
By understanding and addressing these challenges, organizations can fortify their defenses and navigate the digital landscape with greater confidence.
Understanding Web Application Security: An Overview
The security of web applications is a crucial foundation of any online enterprise, serving as the primary line of defense against numerous cyber threats. With e-commerce and data management increasingly reliant on web applications, it is crucial to comprehend the vulnerabilities affecting the security of web applications. A recent report indicated that by 2025, global cybercrime expenses could rise to an astonishing $10.5 trillion each year, highlighting the necessity of implementing strong protective measures.
Furthermore, proactive security integration during the development and deployment phases is necessary for ensuring the security of web applications. Organizations must acknowledge that a single data breach can incur significant financial repercussions, with a reported average cost of $173,074 higher when remote work is a factor. This vulnerability was underscored during the pandemic, as 91% of cybersecurity professionals noted a rise in cyber attacks due to the shift to remote work.
The challenges in securing web systems are exacerbated by funding issues, as 31% of CISOs report projects delayed or removed due to lack of funding. The need for a resilient security framework that protects the security of web applications and adapts to evolving threats has never been clearer. With 97% of threat actors recognized as financially driven, as noted in a 2023 study, the security of web applications is essential not only for protecting sensitive information but also for maintaining a company’s reputation and financial stability.
Identifying Common Web Application Vulnerabilities
Web-based systems are prone to various weaknesses that present considerable dangers to the security of web applications for both organizations and users. Among these, SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and insecure deserialization are the most prevalent. SQL injection allows attackers to manipulate databases directly, potentially leading to the exposure of sensitive data.
Recent reports indicate that SQL injection attacks continue to be a major concern, with a notable increase in their frequency and sophistication in 2024. As cybersecurity experts warn,
SQL injection remains a critical threat, enabling unauthorized data access and manipulation.
Additionally, XSS weaknesses can threaten the security of web applications by allowing the insertion of harmful scripts into web pages, which are subsequently executed in the browsers of unaware users, leading to data theft or session hijacking.
CSRF takes advantage of the inherent trust that a web system has in a user's browser, enabling unauthorized actions to be performed on behalf of the user without their agreement. This kind of weakness in the security of web applications can lead to severe consequences, such as data manipulation and unauthorized transactions. Insecure deserialization poses an additional risk, as it can enable remote code execution, giving attackers full control over the application server.
The prevalence of these weaknesses is highlighted by alarming statistics: organizations using content management systems like WordPress are particularly at risk, emphasizing the need for improved security of web applications, as these sites are three times more likely to host malware than non-CMS websites. In fact, 18% of WordPress sites contain at least one weakness, commonly including SQL injection, CSRF, and XSS. This statistic highlights the necessity for developers and safety teams to remain vigilant and proactive in implementing robust protective measures to enhance the security of web applications and effectively mitigate these risks.
Additionally, it is important to note that Malicious File Upload accounted for 7.25% of high/critical vulnerabilities in 2023, further emphasizing the diverse range of threats facing web systems. The case study titled 'Risks of Content Management Systems' illustrates these challenges, revealing that entities using platforms like WordPress must carefully manage their plugins to reduce security risks.
Best Practices for Securing Web Applications
To effectively secure web platforms, organizations must adopt a multifaceted approach that includes the following best practices:
- Regular Updates: It is essential to keep all software—encompassing libraries and frameworks—up to date. This proactive measure is crucial, as statistics reveal that phishing-related breaches can take up to 206 days to detect and contain, leaving systems vulnerable during that time.
- Input Validation: Validating all user inputs is a critical step in preventing injection attacks, thereby safeguarding the application against unauthorized access and data breaches.
- Secure Coding Practices: Adhering to secure coding standards significantly minimizes the risk of vulnerabilities. Organizations should prioritize training developers in these practices to foster a culture of security from the ground up.
- Web Application Firewalls (WAF): Implementing WAFs is vital for filtering and monitoring HTTP traffic to and from applications. These firewalls serve as a barrier against harmful traffic, particularly relevant considering that WordPress sites are three times more prone to harbor malware than non-CMS websites, with 18% of them displaying at least one flaw. Effective web protection methods, such as those highlighted in the case study titled 'Invest In A Web Protection Solution,' categorize these methods into filtering and isolation, demonstrating how WAFs can be instrumental in preventing data loss.
- Data Encryption: Utilizing encryption for sensitive data, both in transit and at rest, ensures confidentiality and protects against unauthorized access. This is particularly important as the sophistication of attacks increases; advances in artificial intelligence are expected to make Business Email Compromise (BEC) attacks more nuanced in 2024, as highlighted by Armor Resources. Organizations must recognize the importance of robust encryption practices in the face of these evolving threats.
- Access Control: Strict access controls and permissions must be implemented to limit user access to sensitive functionalities. This best practice prevents unauthorized users from exploiting vulnerabilities and helps maintain the integrity of the software. The insights from Armor Resources highlight the necessity for strict access controls as part of a thorough protective strategy.
By adhering to these best practices, organizations can greatly improve the security of web applications, minimizing the chance of data breaches and ensuring a more secure online environment. Furthermore, firms such as Savvycom are committed to developing customized solutions for different sectors, ensuring that protective measures align with specific organizational needs.
The Role of Security Assessments in Web Application Protection
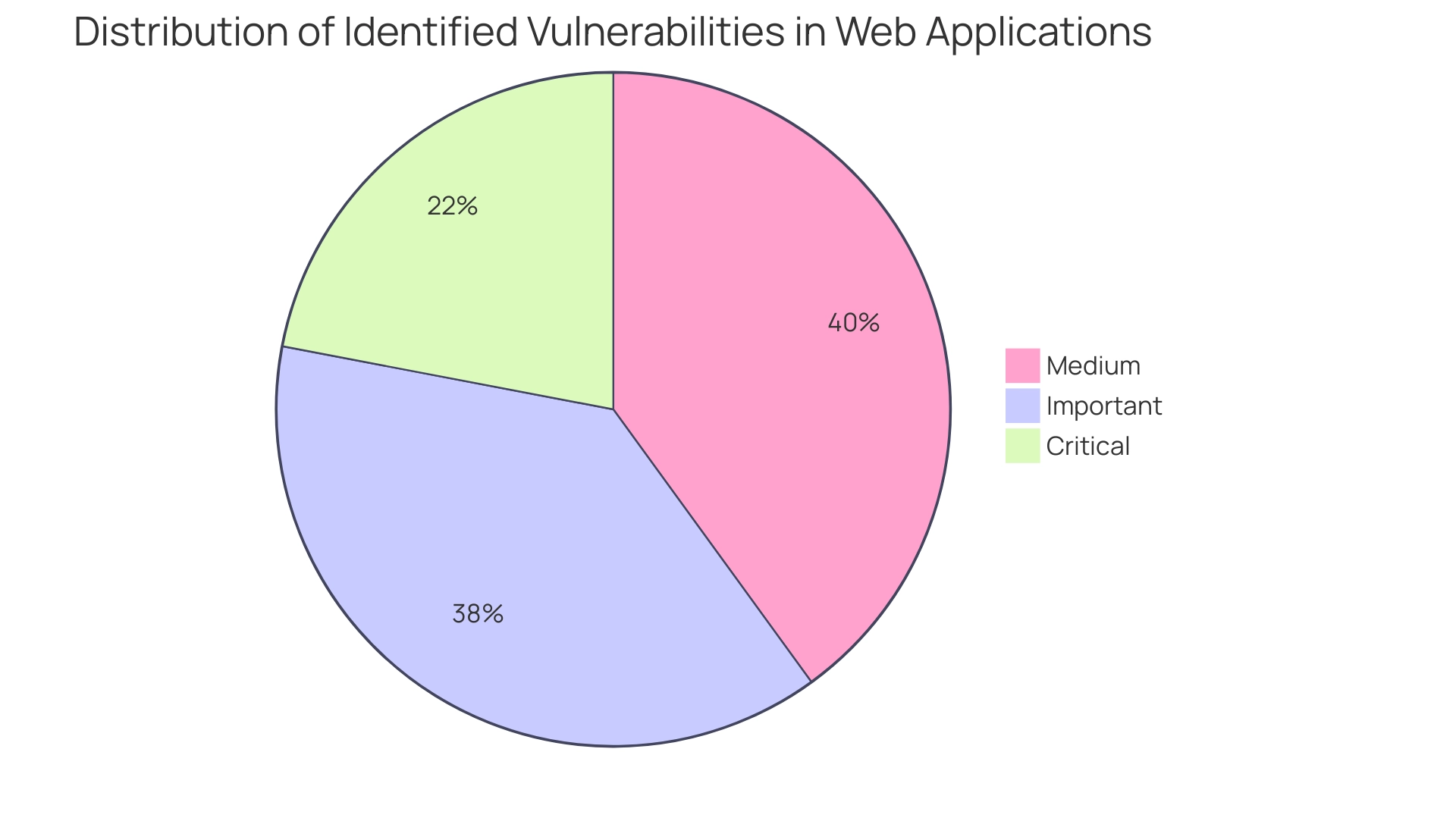
Security assessments, including penetration testing and weakness scanning, are essential for revealing flaws within the security of web applications. Consistently performing these evaluations allows entities to pinpoint vulnerabilities proactively, before harmful individuals can take advantage of them. Recent statistics reveal that:
- 11% of identified weaknesses are deemed critical
- 19% are important
- 20% are medium
This highlights the urgency for organizations to prioritize these evaluations.
Collaborating with outside specialists for third-party assessments provides an unbiased viewpoint on current protective measures, improving the overall evaluation process. Automated tools can also play a pivotal role in scanning for vulnerabilities, ensuring adherence to compliance standards such as:
- SOC 2
- PCI DSS
- HIPAA
- ISO 27001
As highlighted in the Crime Ransomware and Data Leak Site Report 2023, the construction sector was the most affected by ransomware in 2023, demonstrating the need for strong protective measures across all industries.
Furthermore, entities in the Asia-Pacific region have reported a 97% increase in cyber threats due to geopolitical tensions, prompting 51% to update their business continuity and enterprise risk plans. This emphasizes the need for organizations to establish a routine for evaluations to enhance the security of web applications by promptly addressing any identified issues to strengthen their defenses against evolving cyber threats.
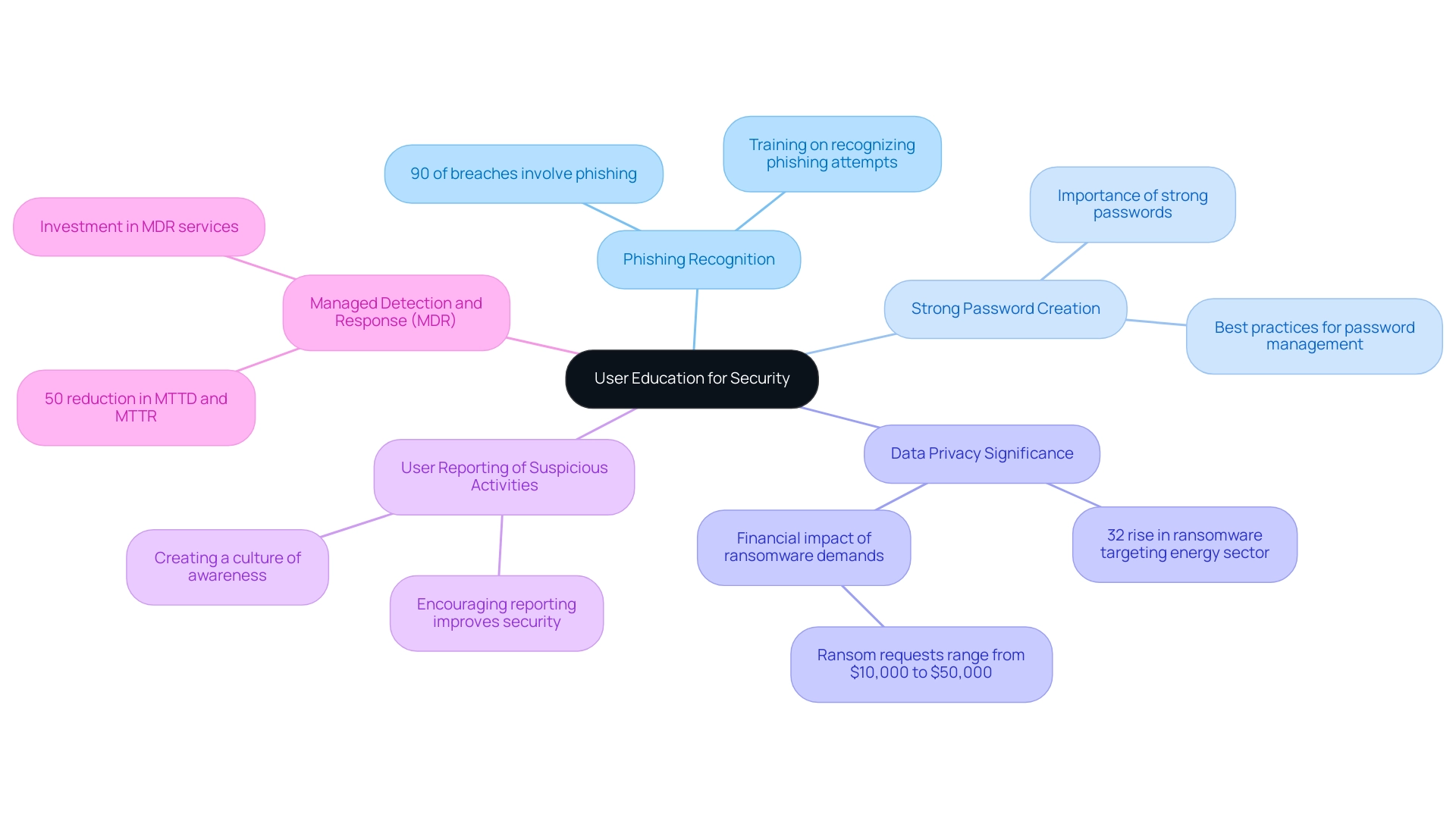
Enhancing Security Through User Education and Awareness
Informing users about the security of web applications is crucial in reducing the risk of breaches arising from human error. Organizations must prioritize regular training sessions that encompass crucial topics such as:
- Recognizing phishing attempts
- Creating strong passwords
- Appreciating the significance of data privacy
Considering the increase in phishing attacks, it is estimated that 90% of incidents and breaches involved a phishing component in 2019, highlighting the necessity of promoting a culture of awareness.
Motivating users to report suspicious activities can greatly improve the entity's overall protective stance. Moreover, entities investing in Managed Detection and Response (MDR) services have observed a 50% decrease in the delta of Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), emphasizing the effect of thorough protective measures, including user education. Implementing practical workshops and simulated phishing exercises not only reinforces learning but also prepares employees to respond adeptly to potential threats.
The recent surge in ransomware incidents, especially a 32% rise targeting energy and utilities sectors in early 2020, demonstrates the significant financial effect of insufficient user education, with ransom requests varying from $10,000 to $50,000. By investing in user education, organizations empower their workforce to serve as the first line of defense against cyber threats, significantly reducing vulnerabilities and enhancing the security of web applications.
Conclusion
In the face of escalating cyber threats, the importance of web application security cannot be overstated. Organizations must recognize that their online platforms are prime targets for attackers, making the understanding of common vulnerabilities such as:
- SQL injection
- XSS
- CSRF
essential. With projected cybercrime costs reaching $10.5 trillion by 2025, the urgency for robust security measures is clear. Implementing best practices like:
- Regular updates
- Secure coding
- Data encryption
can significantly enhance an organization's defense against potential breaches.
Moreover, the role of security assessments is integral in identifying and addressing vulnerabilities before they can be exploited. Engaging in regular penetration testing and vulnerability scanning allows organizations to stay ahead of threats, ensuring compliance with necessary standards. Equally important is fostering a culture of security awareness through user education. By equipping employees with the knowledge to recognize phishing attempts and develop strong security habits, organizations can bolster their defenses against human error—the leading cause of many security incidents.
Ultimately, a comprehensive approach to web application security, combining technical measures, regular assessments, and user education, is vital for safeguarding sensitive information and maintaining organizational integrity. As the digital landscape continues to evolve, organizations that prioritize these strategies will be better positioned to navigate the complexities of cyber threats, ensuring a secure environment for their operations and customers alike.





