Introduction
In an increasingly interconnected world, web applications have become indispensable to business operations and customer interactions. Yet, this essential digital infrastructure is not without its vulnerabilities, as cybercriminals relentlessly target these platforms. With over 40% of cyberattacks aimed at web applications and staggering financial losses attributed to phishing attacks, the urgency for robust security measures has never been more pronounced.
As organizations grapple with the complexities of safeguarding their online assets, understanding the landscape of web application security becomes critical. This article delves into the pressing vulnerabilities that threaten web applications, explores the OWASP Top 10 risks, and outlines proven strategies and tools that can fortify defenses, ensuring that businesses not only survive but thrive in an era of escalating cyber threats.
Understanding Web Application Security: A Critical Overview
In today's digital marketplace, web solutions serve as the backbone for e-commerce, facilitating customer engagement and driving business operations. However, this vital infrastructure also attracts the attention of cybercriminals. Recent statistics show that over 40% of all cyberattacks target web applications, which underscores the necessity for entities to adopt strong security features in web applications.
Alarmingly, businesses lose $17,700 every minute due to phishing attacks, highlighting the significant financial impact of cyber threats. Moreover, worldwide expenditure on cybersecurity products and services is expected to total $1.75 trillion cumulatively over the five-year span from 2021 to 2025, highlighting the increasing demand for investment in protective measures by e-commerce leaders. As the threat landscape continues to evolve, it is imperative that businesses understand the specific vulnerabilities related to the security features in web applications.
Developing a business continuity plan (BCP) is crucial for organizations to maintain essential functions during emergencies, including cyberattacks, illustrating a practical approach to effective strategy implementation. This discussion will establish the groundwork for identifying critical risks and exploring effective strategies to protect online assets.
Identifying Common Vulnerabilities: The OWASP Top Risks
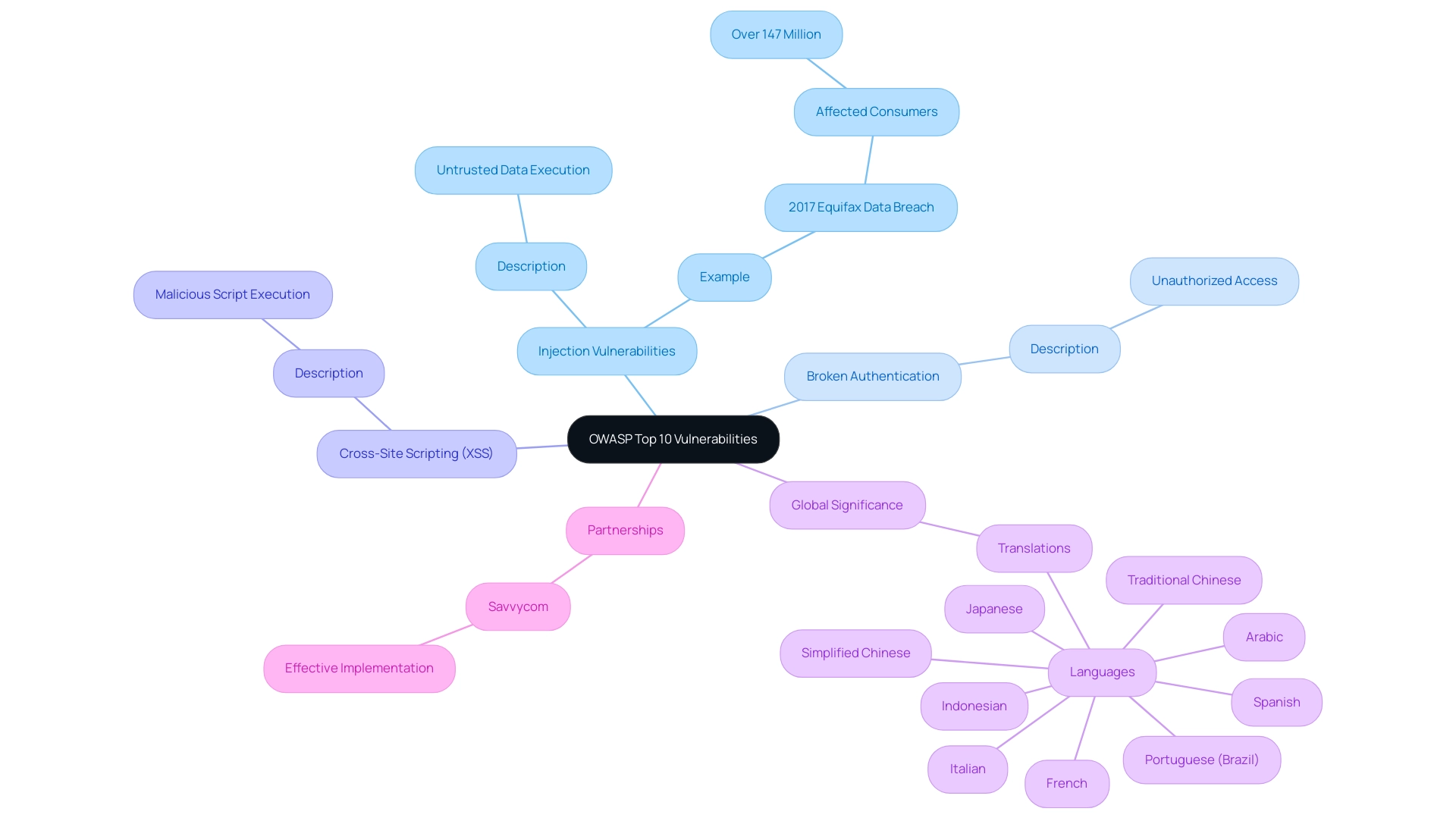
The OWASP Top 10 acts as a vital structure for recognizing the most significant threats to the security features in web applications. Among these, Injection vulnerabilities, Broken Authentication, and Cross-Site Scripting (XSS) are particularly prevalent and dangerous. Injection flaws arise when attackers introduce untrusted data into an interpreter, which can lead to the execution of unauthorized commands.
This vulnerability was starkly illustrated by the 2017 Equifax data breach, which compromised the personal information of over 147 million consumers due to a failure to address a known vulnerability. As Bohdan Serednytsky aptly notes, understanding these common threats is paramount for developers working on security features in web applications. The OWASP Top 10 2021 case study highlights that early detection and resolution of vulnerabilities are essential for preserving application integrity and ensuring the implementation of security features in web applications to safeguard user data.
Additionally, the recent translations of the OWASP Top 10 into various languages, such as Arabic, Spanish, and Japanese, emphasize its worldwide significance and accessibility, facilitating easier engagement for developers globally with these essential guidelines. By prioritizing awareness and implementing robust preventative measures, businesses can significantly enhance their protection stance through security features in web applications. Collaborating with seasoned software development associates, like Savvycom, is essential; these alliances not only enable the efficient execution of required safety protocols but also guarantee that the particular vulnerabilities specified in the OWASP Top 10 are sufficiently managed.
As entities navigate these complexities, the insights gathered from the OWASP Top 10 not only inform security initiatives but also optimize resource allocation to effectively mitigate risks.
Best Practices for Securing Web Applications: Proven Strategies
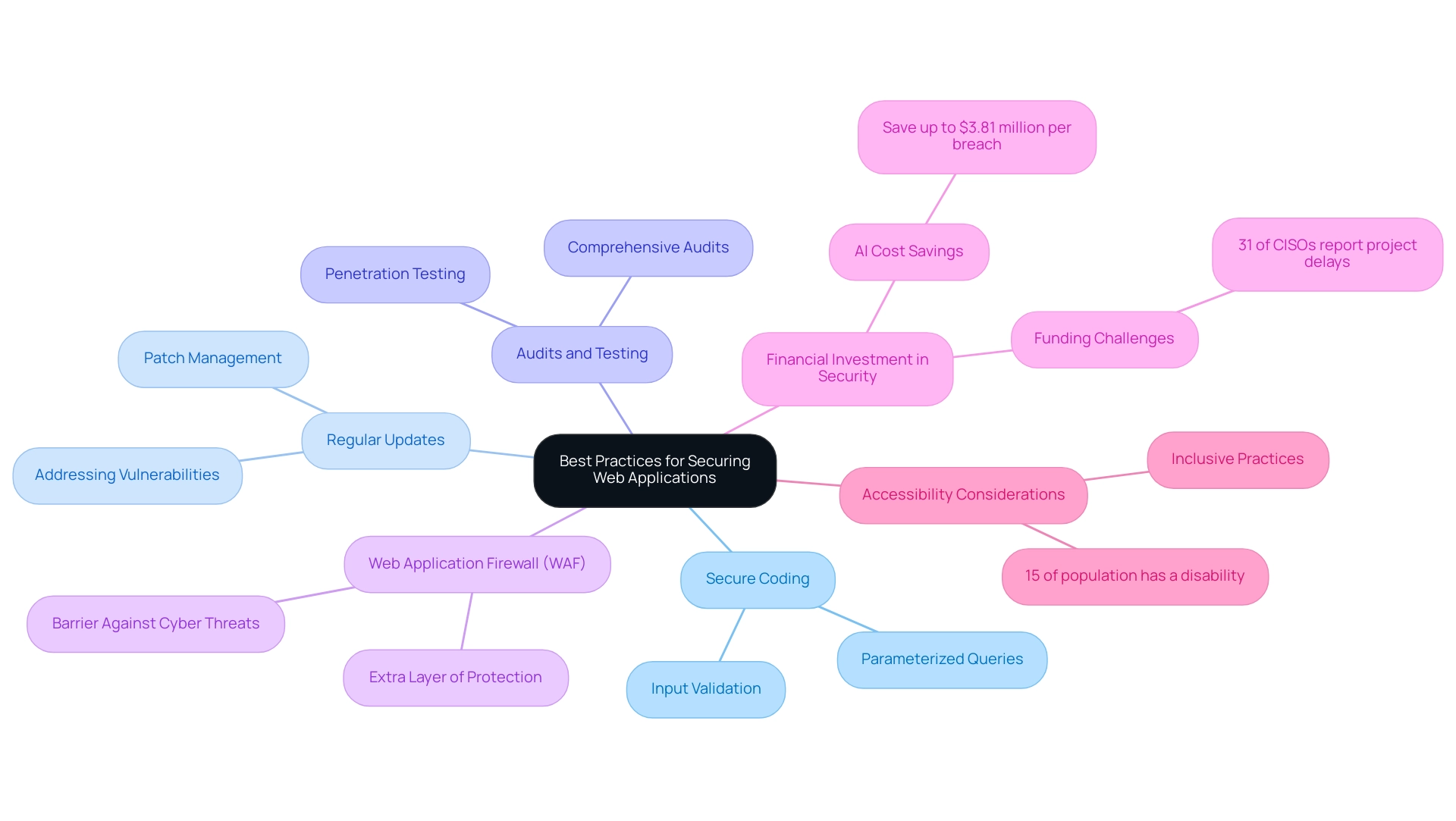
To effectively secure websites, organizations must embrace a range of best practices that are pivotal in incorporating security features in web applications to safeguard sensitive data and maintain user trust. Implementing security features in web applications, such as secure coding practices, is fundamental; for instance, developers should prioritize validating user input to thwart injection attacks and utilize parameterized queries when interacting with databases. This practice not only mitigates risks but also enhances overall application integrity.
Regular updates and patch management are equally vital for maintaining the security features in web applications, as they address known vulnerabilities and strengthen defenses against emerging threats. Conducting comprehensive audits and rigorous penetration testing can further uncover potential weaknesses in the security features in web applications before they can be exploited, ensuring a proactive posture. Additionally, the deployment of a Web Application Firewall (WAF) serves as an essential barrier against various cyber threats, reinforcing the security features in web applications by providing an extra layer of protection.
As Fortune forecasts, the worldwide information protection market is anticipated to hit $366.1 billion by 2028, emphasizing the essential need for entities to embrace these practices as a strategic investment in their digital framework. Moreover, investing in protective measures is financially wise; artificial intelligence can help businesses save up to $3.81 million per data breach. It is also vital for entities to secure sufficient resources for their protection initiatives, as 31% of CISOs report project delays or cancellations due to lack of funding.
Lastly, considering accessibility for individuals with disabilities in web system protection is essential, as 15% of the world’s population has a disability, highlighting the need for inclusive practices that foster user trust and engagement.
Leveraging Security Tools and Technologies for Enhanced Protection
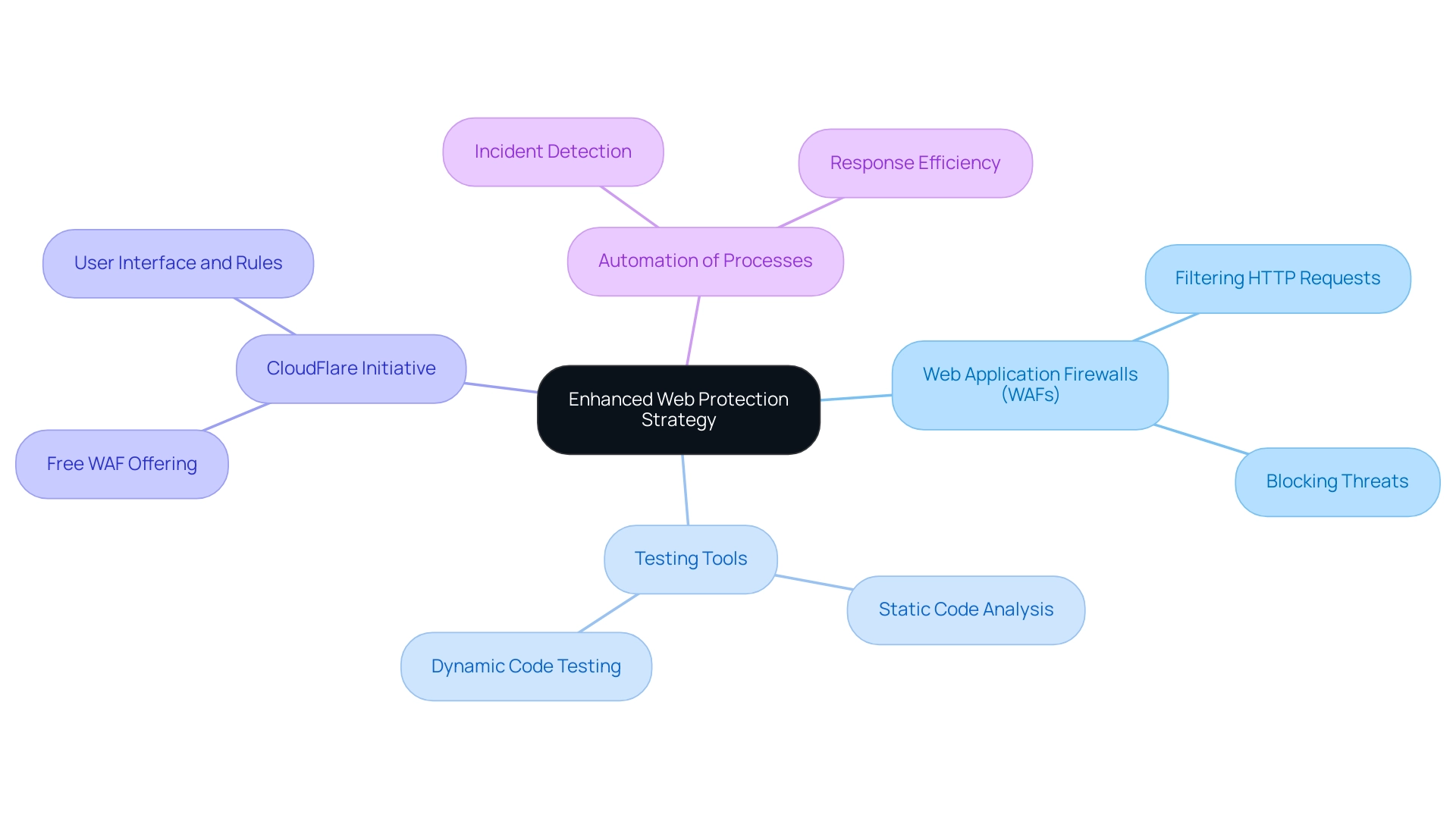
To strengthen protection of web platforms, organizations must implement a comprehensive range of security features in web applications and technologies. Central to this strategy are Web Application Firewalls (WAFs), which provide critical security features in web applications by filtering and monitoring HTTP requests, effectively blocking potential threats before they penetrate the environment. As highlighted by a representative from one of the largest companies in the defense industry,
'Thank you for sending the market report and data.
It looks quite comprehensive and the data is exactly what I was looking for. I appreciate the timeliness and responsiveness of you and your team.'
This highlights the critical need for robust security features in web applications.
The growing demand for such solutions is reflected in the market's projected growth, expected to reach a compound annual growth rate (CAGR) of 18.92% from 2024 to 2031. Incorporating testing tools, particularly static code analysis and dynamic code testing, is essential in identifying vulnerabilities throughout the development lifecycle. These tools enable organizations to identify and address weaknesses early, fostering a more secure software environment.
A concrete example of improving protective measures is CloudFlare's recent initiative to offer a free web application firewall to its subscribers, which includes a user interface and a set of rules to automatically block known threats. This initiative aims to make advanced protection accessible to more users. Moreover, the concerning statistics about web attacks in Latin America, especially in the media entertainment industry, emphasize the urgency of implementing strong web protection measures.
Automating protective processes enhances the efficiency of detecting and responding to potential incidents, enabling organizations to maintain high standards without compromising performance. The latest advancements in security technologies underscore the necessity of integrating these tools into an overarching security strategy, ensuring that security features in web applications remain resilient against evolving threats.
Conclusion
In the face of escalating cyber threats, the importance of web application security cannot be overstated. As outlined, over 40% of cyberattacks target these critical platforms, leading to significant financial losses and underscoring the urgency for businesses to prioritize robust security measures. The insights from the OWASP Top 10 serve as a vital framework for understanding prevalent vulnerabilities, including:
- Injection flaws
- Broken Authentication
These vulnerabilities can have devastating consequences if not addressed.
Implementing best practices such as:
- Secure coding
- Regular updates
- Thorough security audits
is essential for safeguarding sensitive data and maintaining user trust. The deployment of advanced security tools, including:
- Web Application Firewalls
- Automated security testing technologies
enhances an organization’s ability to detect and respond to threats effectively. As the digital landscape continues to evolve, investing in these security initiatives emerges not only as a necessity but also as a strategic advantage.
Ultimately, a proactive approach to web application security is crucial for organizations aiming to thrive in today’s interconnected marketplace. By understanding vulnerabilities, embracing best practices, and leveraging cutting-edge technologies, businesses can significantly fortify their defenses. This commitment to security will not only protect their assets but also foster trust and confidence among users, ensuring long-term success in an era fraught with cyber challenges.





