Introduction
In an age where digital threats loom larger than ever, the significance of web application penetration testing cannot be overstated. As organizations increasingly rely on online platforms to conduct business, the potential for vulnerabilities to be exploited by malicious actors becomes a pressing concern. This article delves into the multifaceted world of penetration testing, exploring its critical role in identifying weaknesses, safeguarding sensitive data, and ensuring compliance with stringent regulations.
By examining key methodologies, essential tools, and best practices, readers will gain a comprehensive understanding of how to fortify their web applications against an ever-evolving landscape of cyber threats. With staggering statistics highlighting the financial ramifications of security breaches, the urgency for robust testing strategies is clear—organizations must act decisively to protect their digital assets and maintain the trust of their customers.
Understanding Web Application Penetration Testing
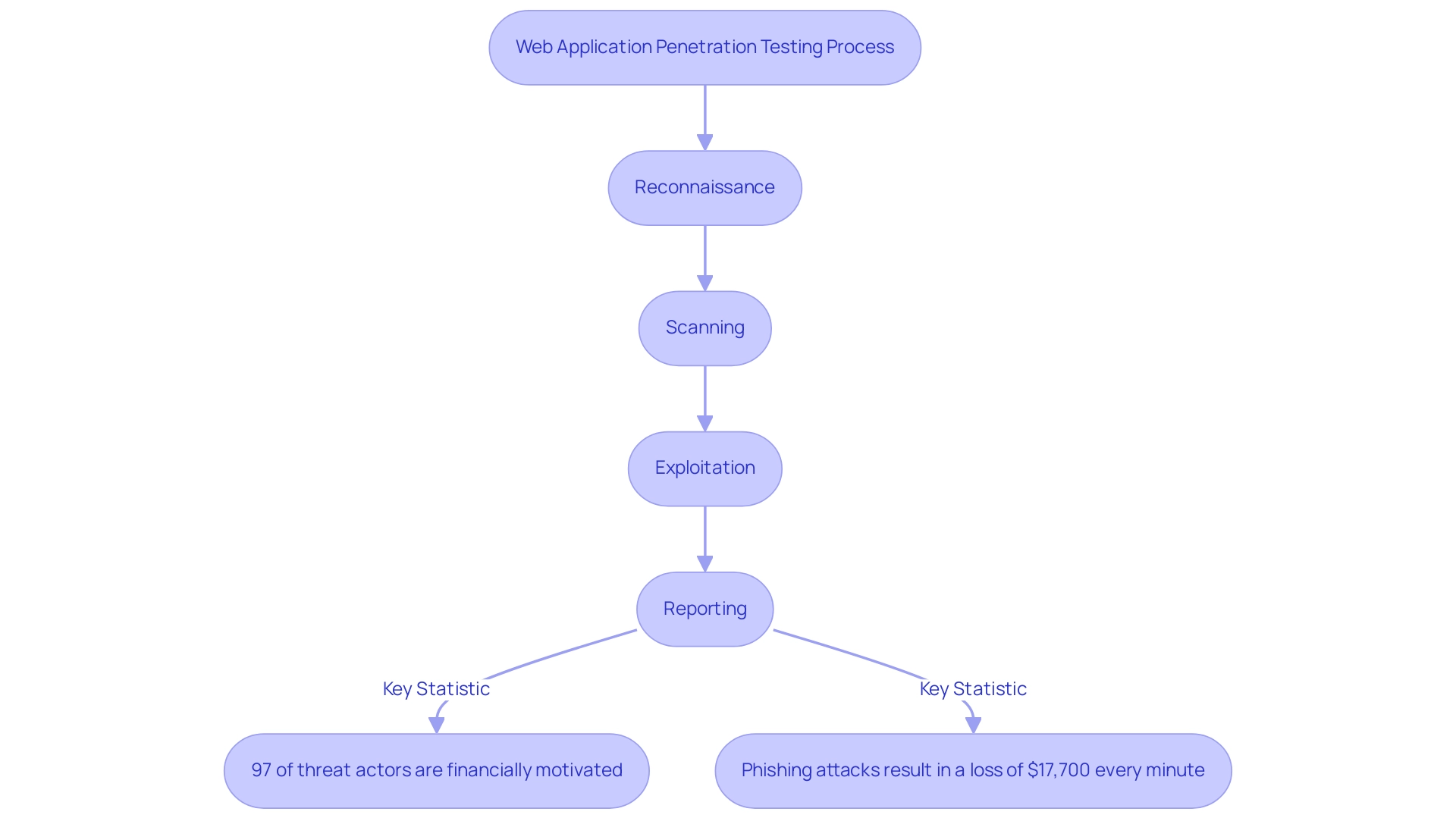
Web application security assessments, including penetration testing of web applications, serve as a crucial line of defense in identifying vulnerabilities within web applications through simulated cyber attacks. This systematic approach employs a range of techniques to assess the protective stance of the application, concentrating on potential exploit weaknesses. The fundamental elements of vulnerability assessment, which encompass reconnaissance, scanning, exploitation, and reporting, are crucial for developing effective protective strategies.
As emphasized in a recent data breach investigation report, 97 percent of threat actors are financially motivated, underscoring the necessity for strong protective measures. Furthermore, 48% of organizations have reported incidents of information theft due to malware, making it imperative for e-commerce platforms to prioritize penetration testing as a means of safeguarding sensitive customer data and upholding trust. The growing dependence on secure online transactions requires a proactive strategy for identifying weaknesses, especially as phishing attacks represent over 80 percent of reported security incidents, with organizations encountering attempts weekly or daily—57% of which are documented.
Significantly, 52% of individuals who clicked on phishing links thought they were from a senior executive in their organization, emphasizing the critical need to tackle weaknesses related to social engineering. The financial implications are staggering, with phishing attacks resulting in a loss of $17,700 every minute. Eoin Keary, CEO & Founder, emphasizes that society must focus on addressing the 'right vulnerabilities' swiftly to mitigate exposure in the ever-evolving landscape of cybersecurity.
Considering these challenges, comprehending and applying effective security assessment techniques is crucial for sustaining a secure digital environment.
The Importance of Penetration Testing for Web Applications
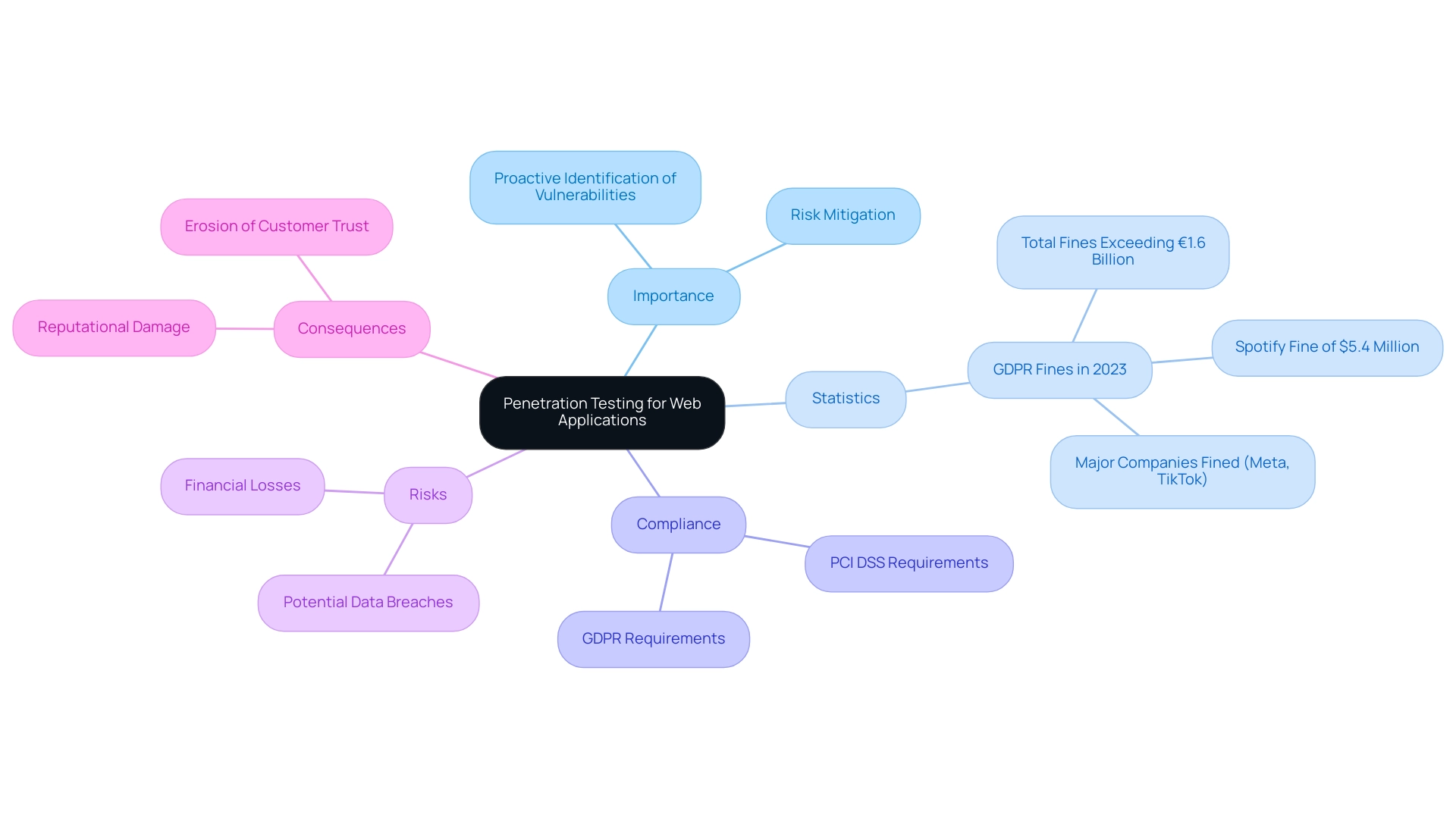
In the rapidly changing landscape of cybersecurity, the practice of penetration testing of web applications has emerged as an essential method for safeguarding them. By proactively identifying vulnerabilities, organizations can effectively mitigate risks before they escalate into severe data breaches or lead to significant financial losses. Recent statistics underscore the urgency of this need; in 2023 alone, GDPR enforcement resulted in record fines exceeding €1.6 billion, surpassing total fines from 2019 to 2021, with major corporations like Meta and TikTok facing substantial penalties.
Additionally, Spotify was fined $5.4 million in 2023, further illustrating the critical nature of adhering to regulations such as GDPR and PCI DSS, which require regular evaluations. Beyond compliance, the repercussions of data breaches extend to reputational damage, eroding customer trust. Routine vulnerability assessments not only protect sensitive data but also strengthen customer trust in a brand's dedication to safety.
As highlighted in the Crime Ransomware and Data Leak Site Report 2023, sectors like construction were notably impacted by ransomware, emphasizing that all industries must prioritize robust security measures. This statistic demonstrates that ransomware is not selective by sector, emphasizing the need for security assessments as a universal requirement. In this context, security assessments serve not just as a protective measure but as a strategic necessity for any organization aiming to thrive in today’s digital marketplace.
Key Methodologies for Effective Penetration Testing
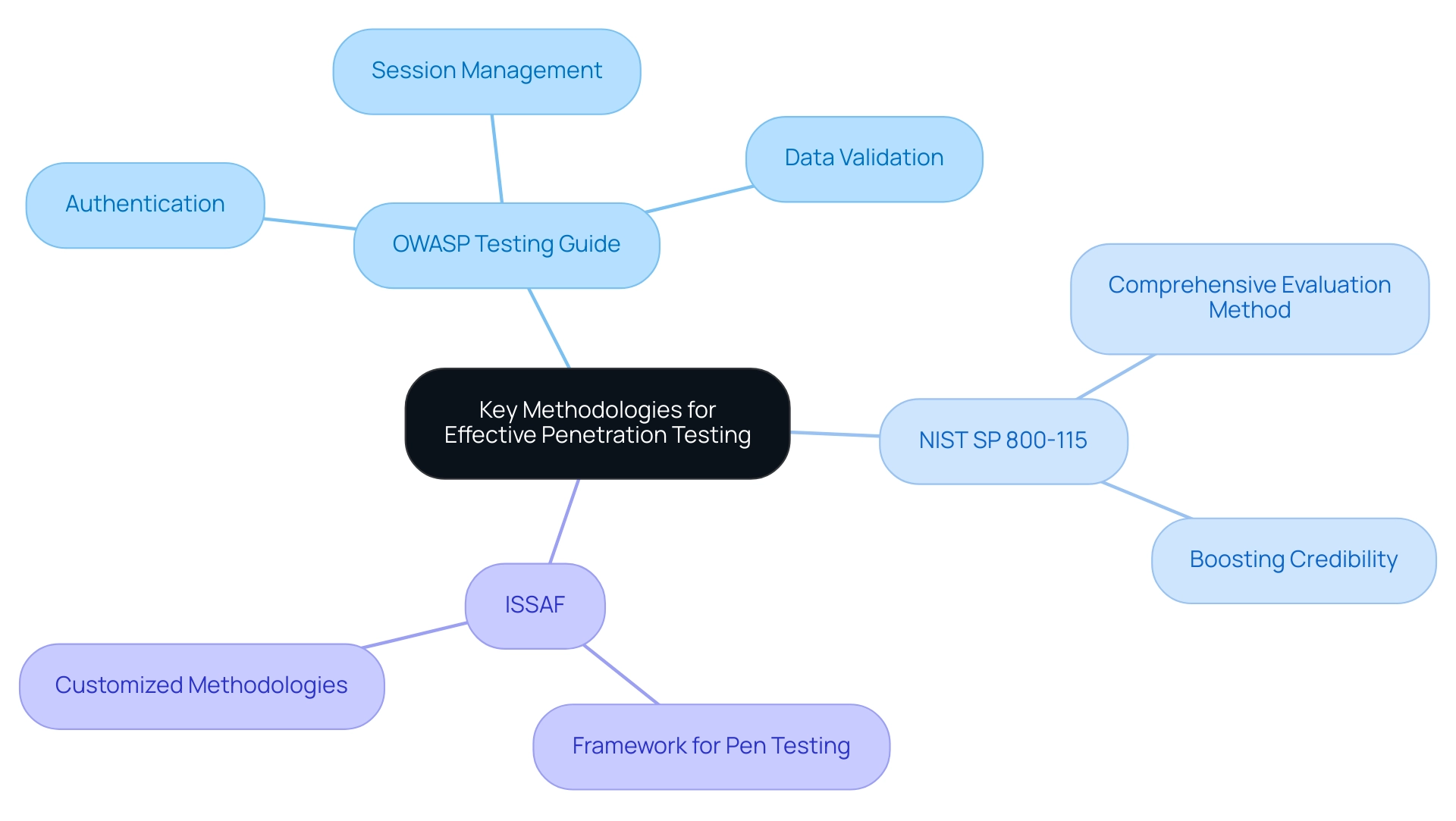
Efficient security assessments are fundamentally grounded in established methodologies that simplify the evaluation process. The OWASP Testing Guide serves as a critical resource, offering a structured framework for penetration testing of web applications, focusing on essential components such as:
- Authentication
- Session management
- Data validation
Significantly, statistics show that among vulnerabilities recognized in 2020,
- 11% were categorized as critical
- 19% as important
- 20% as medium
This highlights the necessity of comprehensive evaluation in high-risk areas.
Additionally, the NIST SP 800-115 offers a comprehensive method for performing security evaluations, boosting the credibility and efficiency of intrusion assessment efforts. As a quote highlights, 'Penetration assessment for the public sector is likely to boost future growth by 2028,' reinforcing the significance of these methodologies. Adhering to these frameworks enables penetration testers to ensure comprehensive evaluations through penetration testing of web applications, significantly increasing the likelihood of uncovering vulnerabilities.
Additionally, the Information System Security Assessment Framework (ISSAF) serves as a practical example of a framework for penetration testing of web applications that, despite being outdated, provides a foundation for developing tailored methodologies. Testers must adjust their methods to the particular context and technology framework of the application in question, ensuring that the evaluation process is both pertinent and efficient in today’s changing landscape of safety. As we approach 2024, staying informed on the latest updates to the OWASP Testing Guide and emerging methodologies will be essential for maintaining a robust protection stance.
Essential Tools for Web Application Penetration Testing
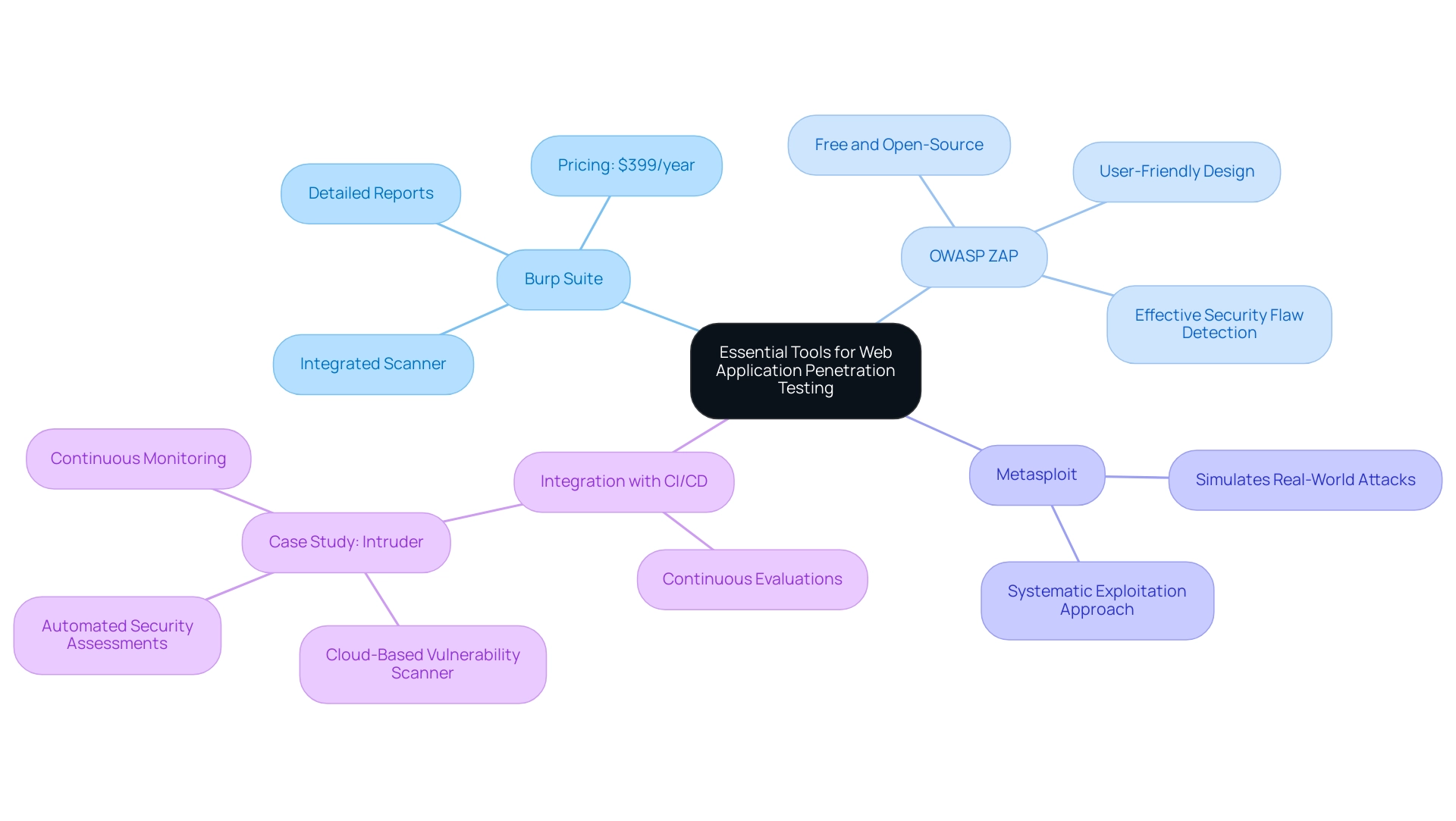
A variety of essential tools can significantly enhance the efficiency and effectiveness of the penetration testing of web applications. Among the most prominent are Burp Suite and OWASP ZAP, both renowned for their robust scanning capabilities and intuitive user interfaces. Burp Suite, starting at $399 per year, features an integrated scanner that identifies common security issues while providing detailed reports and recommendations for remediation.
This functionality enables testers to efficiently tackle weaknesses as they arise. OWASP ZAP, conversely, provides a free and open-source option that is widely embraced for its effectiveness in security flaw detection and user-friendly design.
As Gowsika, an avid reader and storyteller, aptly puts it, "Your guide through cyber jungles, with a serene soul and a sharp pen!" This highlights the importance of having reliable tools in navigating the complexities of cybersecurity.
In addition to these tools, Metasploit remains a favored option due to its systematic approach to exploiting identified vulnerabilities. It enables professionals to evaluate the resilience of applications by simulating real-world attacks. Each tool serves a distinct purpose in the penetration testing of web applications, ranging from automated scanning to manual testing, which allows testers to choose the right one based on their project’s specific needs.
To further enhance protection, integrating these tools into continuous integration/continuous deployment (CI/CD) pipelines is highly recommended. This practice ensures that applications undergo ongoing evaluations, allowing organizations to maintain a robust defense posture throughout the development lifecycle. For instance, the case study of Intruder demonstrates how a cloud-based vulnerability scanner improves protective measures through continuous vulnerability scanning and incident analysis.
As the landscape of web application security continues to evolve, leveraging these tools effectively is crucial for safeguarding digital assets.
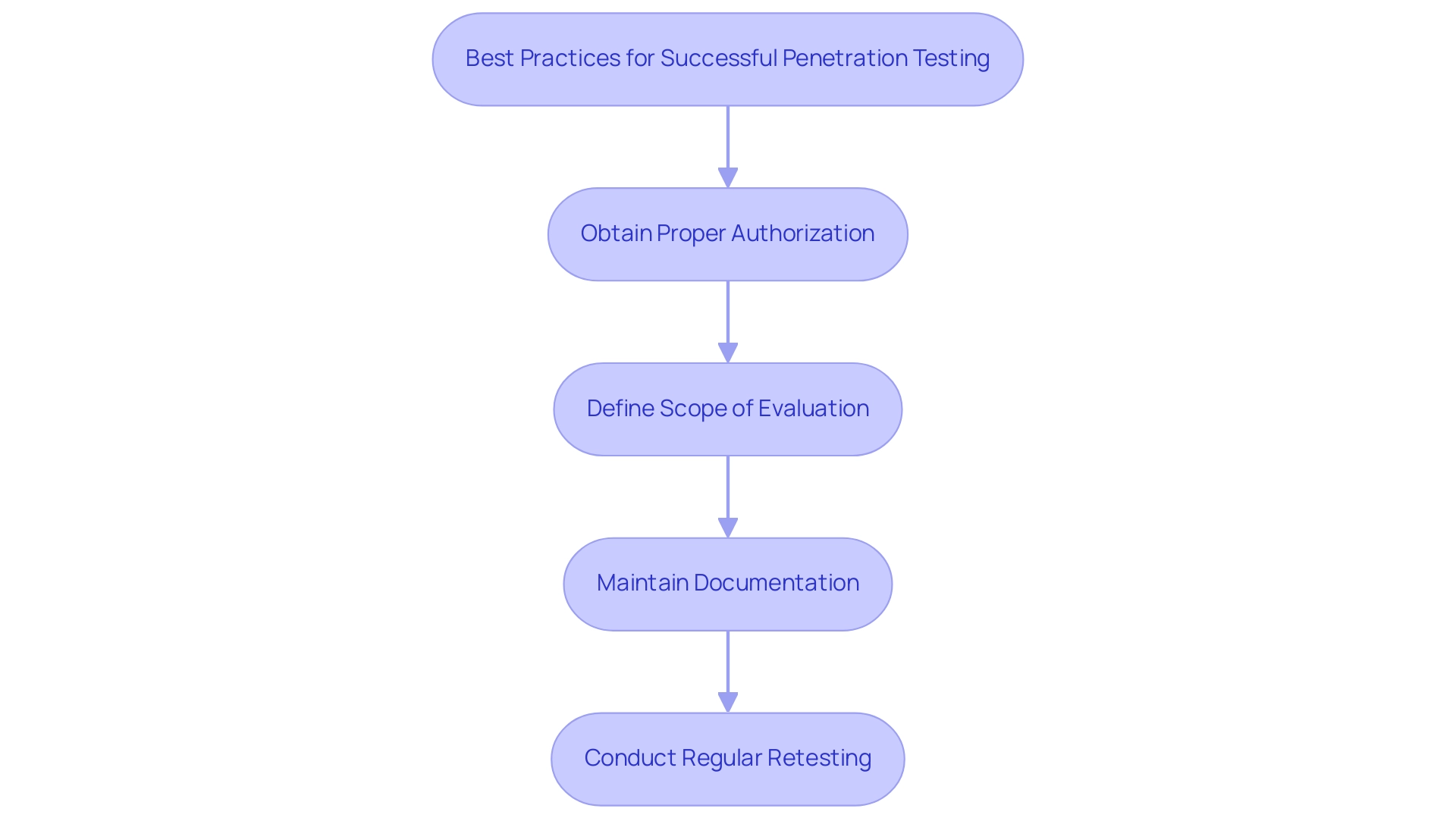
Best Practices for Successful Penetration Testing
To achieve successful penetration testing of web applications assessment outcomes, practitioners must adhere to several essential best practices. First and foremost, obtaining proper authorization is crucial to avoid potential legal ramifications, as unauthorized evaluation can lead to significant legal issues for organizations. Furthermore, defining the scope of evaluation with precision is vital; it allows teams to concentrate on relevant areas while minimizing unnecessary disruptions to operations.
Common techniques employed by penetration testers include:
- Password spraying (49%)
- Password guessing (33%)
These reflect current practices in the field. Maintaining meticulous documentation throughout the evaluation process serves as a cornerstone for effective reporting and remediation, ensuring that all findings are thoroughly recorded and actionable. Regular retesting after weaknesses have been addressed is equally important; it confirms that the implemented fixes are effective and that the organization's security posture is robust.
The oldest vulnerability identified in 2020, CVE-1999-0517, highlights the importance of continuous vigilance in security assessments. By diligently following these best practices, organizations can significantly bolster their defenses against cyber threats through effective penetration testing of web applications, thereby reducing the likelihood of successful attacks. Notably, penetration testing for the public sector is likely to boost future growth by 2028, emphasizing the importance of these practices in a broader context.
Conclusion
Web application penetration testing is an indispensable element in the cybersecurity framework of any organization. By employing systematic methodologies and utilizing essential tools, businesses can proactively identify and address vulnerabilities before they can be exploited by malicious actors. The staggering statistics surrounding data breaches and the financial repercussions of security failures underscore the pressing need for robust penetration testing practices. This proactive approach not only protects sensitive data but also reinforces compliance with regulations that are increasingly stringent in the digital age.
Moreover, adhering to best practices in penetration testing ensures that organizations can navigate the complexities of cybersecurity effectively. From obtaining proper authorization to defining testing scopes and maintaining thorough documentation, these practices are essential to building a resilient security posture. As the landscape of cyber threats continues to evolve, the integration of continuous testing within development processes becomes crucial for maintaining ongoing security.
Ultimately, the message is clear: organizations must prioritize web application penetration testing as a foundational strategy in their cybersecurity efforts. By doing so, they not only safeguard their digital assets but also foster trust with their customers, positioning themselves for success in an increasingly competitive and risk-laden digital marketplace. Taking decisive action today can mitigate risks and pave the way for a secure tomorrow.





