Introduction
In an age where cyber threats are becoming increasingly sophisticated, the imperative for organizations to safeguard their web applications has never been more pronounced. Web application penetration testing emerges as a crucial strategy, enabling businesses to proactively identify and address vulnerabilities before they can be exploited by malicious actors.
With a staggering rise in malware threats, understanding the methodologies, tools, and reporting mechanisms involved in effective penetration testing is essential for maintaining a robust cybersecurity posture. This article delves into the critical components of web application pen testing, exploring best practices and real-world case studies that underline its significance in protecting sensitive data and reinforcing trust in digital platforms.
As the landscape of cyber threats continues to evolve, organizations must remain vigilant and informed, ensuring that their defenses are not only reactive but also strategically proactive.
Understanding Web Application Penetration Testing
Web application security assessments, also known as pen testing web applications, serve as an essential protective measure against cyber threats, specifically designed to identify weaknesses within your web applications that malicious individuals could exploit. This proactive method simulates a cyber attack, enabling organizations to assess their protective stance from an external perspective. With malware-based threats rising by 30% in the first half of 2024 compared to the prior year, the need for strong penetration evaluation has never been more vital.
Key objectives of pen testing web applications include:
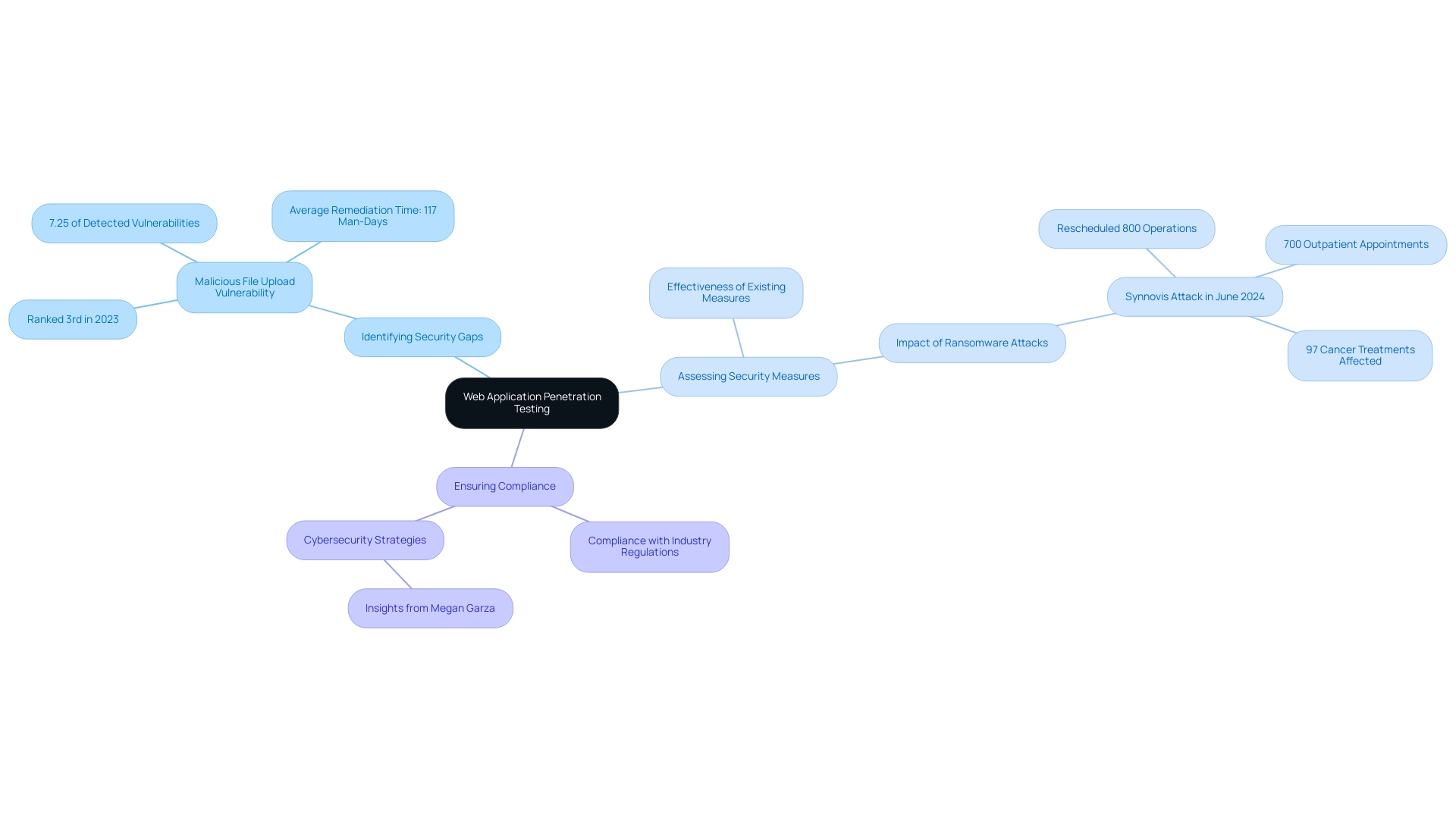
- Identifying security gaps
- Assessing the effectiveness of existing security measures
- Ensuring compliance with industry regulations
As cybersecurity expert Megan Garza highlights, cybersecurity is crucial for all sectors, including e-commerce, where recognizing weaknesses is key to safeguarding sensitive customer information. A notable case study highlighting this necessity is the Malicious File Upload Issue, which ranked as the third most common high/critical severity flaw in 2023, accounting for 7.25% of detected problems.
This weakness had an average remediation time of 117 man-days, underscoring the challenges organizations face in managing such risks. Additionally, the recent ransomware attack on Synnovis in London, which resulted in the rescheduling of over 800 operations and 700 outpatient appointments, including 97 cancer treatments, illustrates the real-time impact of cyber threats. For e-commerce companies managing sensitive customer information, security assessments are not only crucial for protecting digital assets but also for strengthening customer confidence in online platforms.
By conducting pen testing web applications to uncover vulnerabilities before they can be exploited, organizations can significantly reduce their risk exposure and enhance their overall cybersecurity framework.
Key Methodologies for Effective Penetration Testing
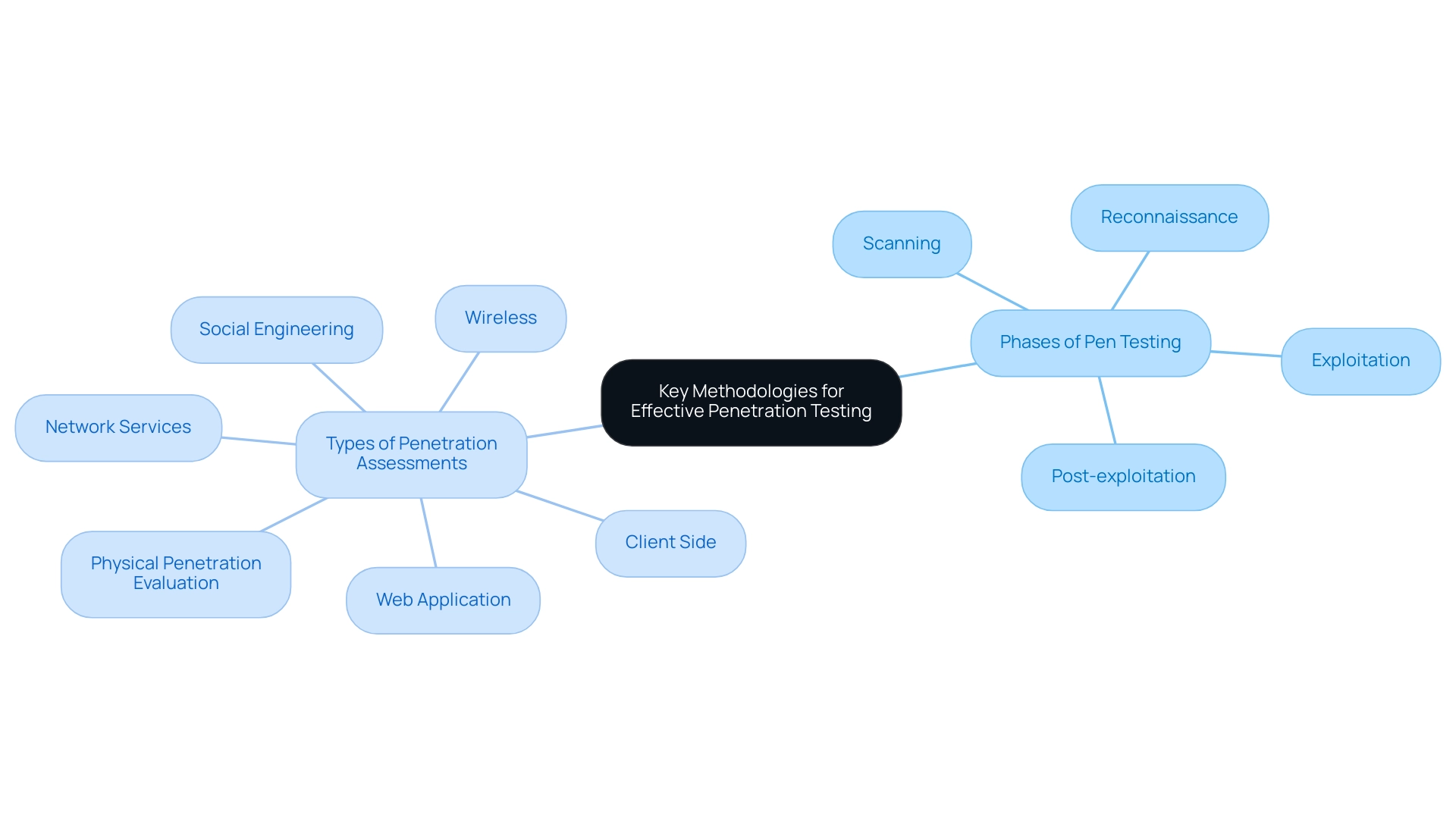
Effective evaluations of pen testing web applications hinge on the application of well-defined methodologies. The OWASP Testing Guide stands out as a pivotal framework for pen testing web applications, covering essential phases such as:
- Reconnaissance
- Scanning
- Exploitation
- Post-exploitation
This structured approach not only enhances the thoroughness of the evaluation process but also aligns with industry best practices recommended by the NIST SP 800-115 guide, which underscores the necessity of systematic examination.
By adhering to these methodologies, organizations can conduct comprehensive pen testing web applications, systematically addressing potential vulnerabilities that could be exploited by malicious actors. There are six significant types of penetration assessments:
- Network Services
- Wireless
- Web Application
- Client Side
- Physical Penetration Evaluation
- Social Engineering
Furthermore, incorporating threat modeling at the onset of the evaluation process plays a crucial role in identifying high-risk areas, allowing for targeted efforts in those domains.
As Andrea Sugden, Chief Sales and Customer Relationship Officer, emphasizes, "Let’s Talk To get started with a Viking Cloud cybersecurity and compliance assessment, email, call or click: Contact Us." This highlights the importance of engaging with experts to enhance security measures. Additionally, the case study titled 'Stages of Penetration Testing Methodologies' outlines the various stages involved in pen testing web applications, which include:
- Scoping and planning
- Building inventory
- Reconnaissance
- Analysis
- Attack launch
- Reporting
Each stage is crucial for understanding the client's infrastructure and identifying vulnerabilities. As organizations navigate the complexities of cybersecurity in 2024, leveraging established methodologies is imperative for ensuring robust security postures.
Essential Tools for Web Application Pen Testing
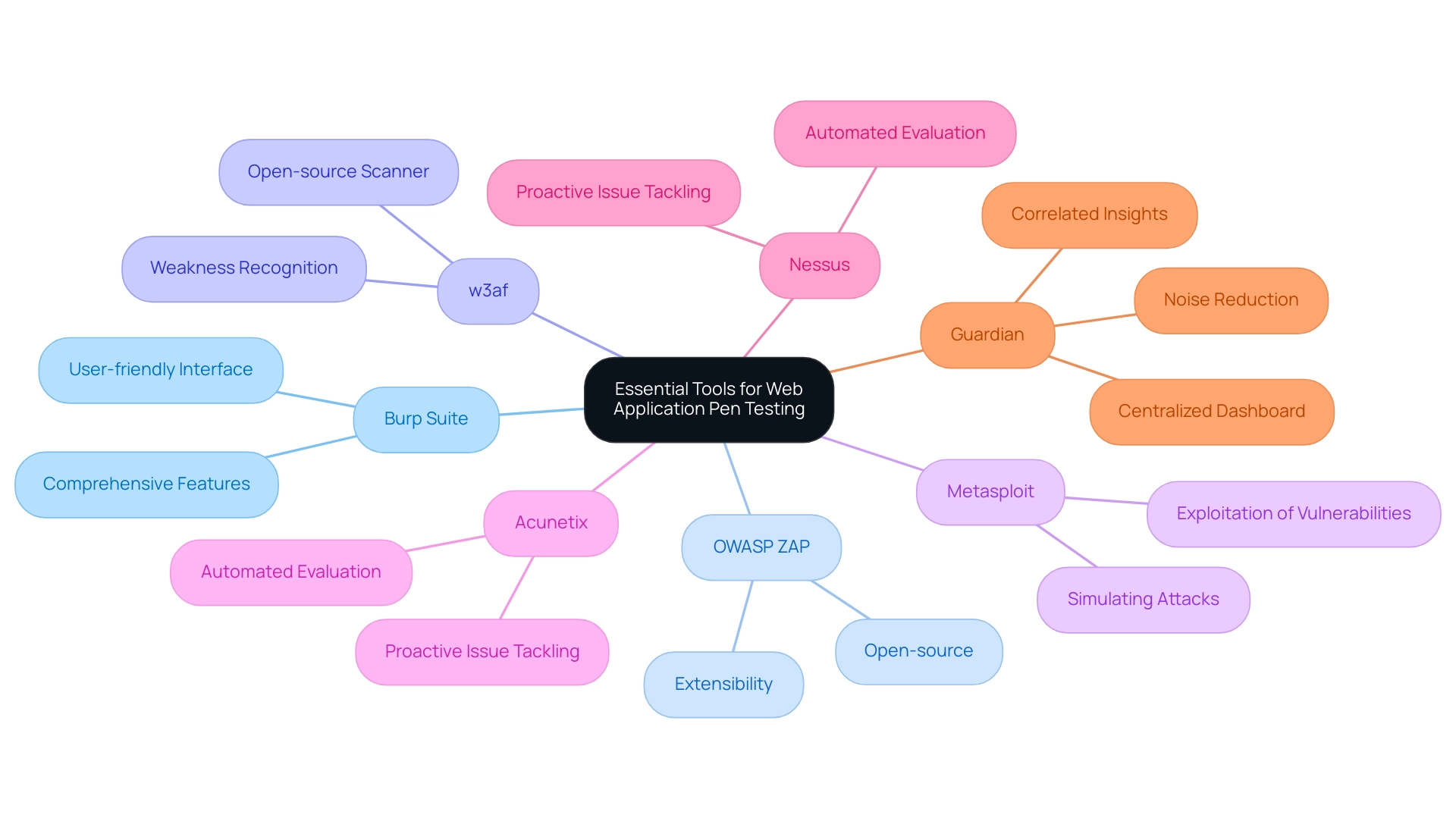
Effective pen testing web applications hinges on the right set of tools tailored to specific objectives and application requirements. In 2024, Burp Suite and OWASP ZAP stand out as two of the most popular tools for pen testing web applications, recognized for their robust capabilities in identifying weaknesses and conducting thorough scans. Security professionals often praise Burp Suite for its comprehensive features and user-friendly interface, while OWASP ZAP is lauded for its open-source nature and extensibility, both of which are valuable tools for pen testing web applications.
A significant case study from 2013 emphasizes how researchers from the University of California, Santa Barbara, employed w3af for pen testing web applications, revealing weaknesses in major banks' web applications and resulting in considerable improvements in online banking safety. As noted by the researchers, 'w3af assisted in recognizing several weaknesses in the pen testing web applications of major banks, aiding in enhancements to the overall protection of online banking platforms.' For those focused on exploiting identified vulnerabilities, pen testing web applications using Metasploit serves as a powerful tool that can simulate attacks to demonstrate potential risks.
Meanwhile, automated evaluation solutions like Acunetix and Nessus provide valuable insights into vulnerabilities that are critical for pen testing web applications, allowing teams to tackle issues proactively. Notably, with more than 1,000 comprehensive software reviews available, selecting the right tools not only maximizes effectiveness but also reinforces a commitment to security, ultimately fostering trust with customers and stakeholders. Additionally, Guardian is presented as an Application Security Posture Management solution that assists in managing results from testing tools, featuring a centralized dashboard, noise reduction, and correlated insights.
Reporting and Remediation: Closing the Loop on Pen Testing
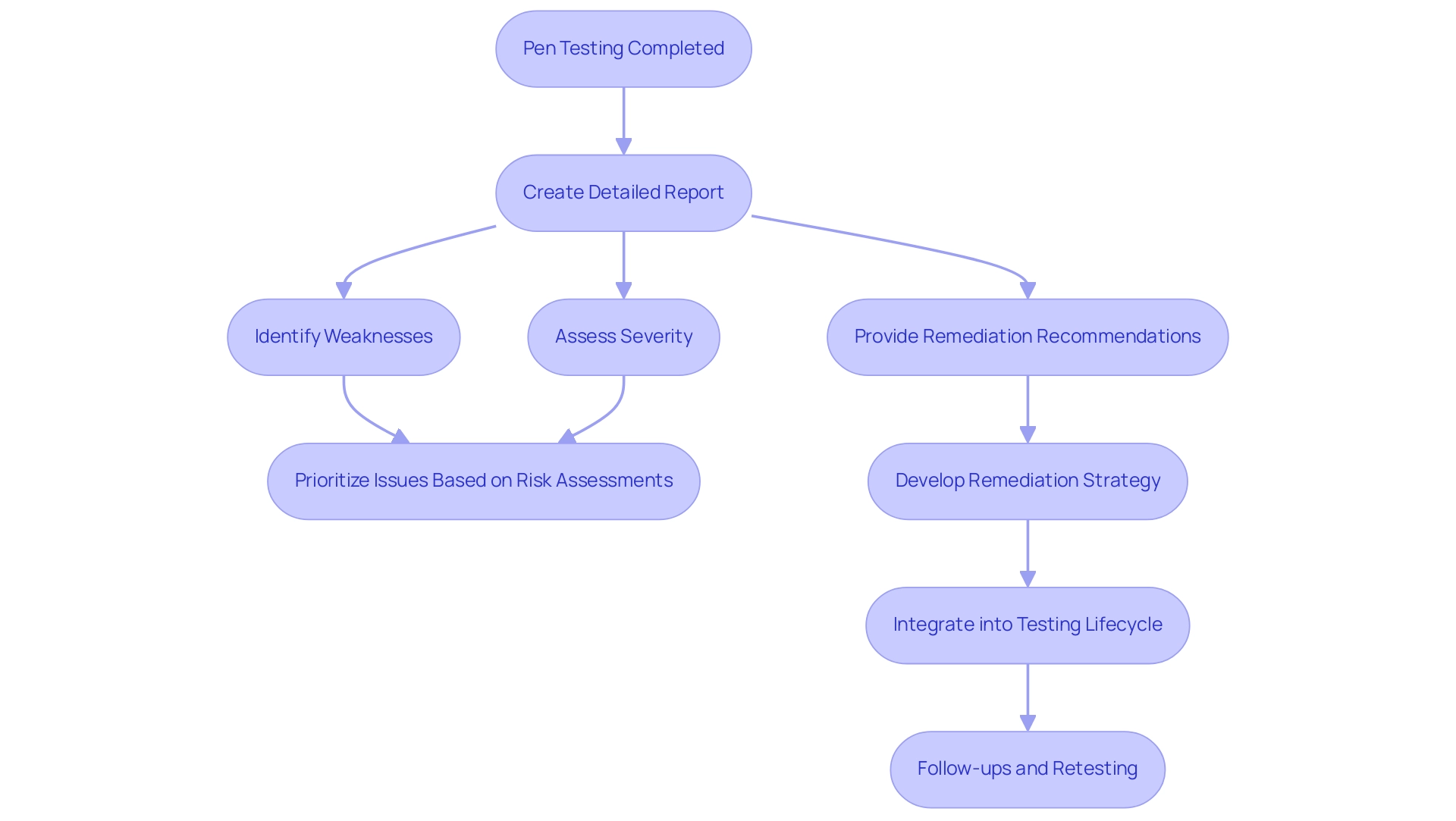
Once pen testing web applications is completed, it is essential to create a detailed report. This document should outline the identified weaknesses, assess their severity, and provide clear remediation recommendations. Given that 32% of software weaknesses reported by ethical hackers remain undetected, prioritizing these issues based on comprehensive risk assessments is critical for organizations.
Furthermore, the oldest flaw discovered in 2020, CVE-1999-0517, serves as a stark reminder of the long-term risks associated with these issues and the importance of addressing them promptly. An effective report must include an executive summary tailored for stakeholders who may lack technical expertise, ensuring that all levels of the organization understand the findings and implications. Creating a strong remediation strategy is essential, including best practices that effectively tackle the identified weaknesses found in pen testing web applications.
For instance, BreachLock's Penetration Testing as a Service (PaaS) offering exemplifies how integrating remediation into the testing lifecycle can lead to enhanced protection outcomes and compliance. Consistent follow-ups and retesting are essential to confirm the effectiveness of remediation efforts and to ensure that new weaknesses do not arise during application updates or modifications. This proactive method not only strengthens protection but also improves resource efficiency in risk management.
As the worldwide network security market is anticipated to expand considerably, the importance of security assessments and efficient vulnerability management will only rise. Moreover, security assessments for the public sector are expected to enhance future growth by 2028, emphasizing its significance across different industries.
The Importance of Regular Penetration Testing for Security
Regular pen testing web applications is a cornerstone of effective cybersecurity for web and mobile applications, especially as cyber threats continue to evolve. Experts recommend conducting these tests at least annually, or even quarterly or continuously for companies in high-risk industries, especially when significant changes are made to the application. This proactive method assists organizations in recognizing and addressing weaknesses before they can be exploited.
The higher education sector has become increasingly vulnerable, with 40% of ransomware attacks attributed to exploited vulnerabilities. This statistic highlights the critical necessity for organizations to prioritize vulnerability assessment as part of their protective strategy. The case study on ransomware attacks in higher education demonstrates that ignoring security assessments not only leaves organizations vulnerable to cyber threats but can also obstruct adherence to regulations such as the Family Educational Rights and Privacy Act.
As stated by Steve Morgan, Founder and Editor-in-Chief at Cybersecurity Ventures, Tiger teams were government and industry-sponsored groups of crackers who sought to breach the defense of computer systems to reveal, and ultimately fix, vulnerabilities. This historical perspective reinforces the necessity of ongoing vigilance in cybersecurity practices and highlights how lessons learned from the past can inform modern strategies. By adhering to industry standards and regulations, organizations not only protect sensitive data but also foster consumer trust, ensuring their defenses are both robust and resilient in the face of emerging threats.
Integrating regular pen testing web applications into an overall security strategy is imperative for maintaining a strong cybersecurity posture in 2024 and beyond.
Conclusion
In today's rapidly evolving digital landscape, the significance of web application penetration testing cannot be overstated. As outlined, this proactive strategy not only identifies vulnerabilities but also fortifies an organization's defenses against increasingly sophisticated cyber threats. With a 30% rise in malware threats, the urgency for businesses to adopt robust security measures has reached a critical juncture.
The methodologies and tools discussed are essential for conducting thorough penetration tests. By adhering to established frameworks like the OWASP Testing Guide and employing powerful tools such as Burp Suite and OWASP ZAP, organizations can systematically assess their security posture. The case studies presented highlight real-world implications, demonstrating the tangible benefits of identifying and remediating vulnerabilities before they can be exploited.
Furthermore, the importance of comprehensive reporting and remediation processes ensures that organizations can effectively address identified risks. Regular penetration testing, as emphasized, is not merely a recommendation but a necessity, particularly for sectors vulnerable to cyber threats. By integrating these practices into their security strategies, organizations can foster consumer trust and safeguard sensitive data, ultimately reinforcing their resilience against future attacks.
As cyber threats continue to evolve, maintaining a proactive stance through regular penetration testing will be paramount. Organizations that prioritize these efforts will not only protect their assets but also cultivate a culture of security awareness that permeates their operations. The time to act is now; a robust cybersecurity framework is essential for thriving in the digital age.





